Hm, looks here is any big mistake- PRESENT configuration without VLAN worked even 2 year. Without problem.
Present network is 10.16.0.0/30:
network
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.252.0'
option ip6assign '60'
option ipaddr '10.16.0.1'
DHCP
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option limit '254'
option start '10.16.1.1'
Earlier was my complete configuration. This work. I know this work reason it.... work. Static IP-area is 10.16.0.1....10.16.0.254. Dynamic ip area is 10.16.1.1...10.16.1.254.
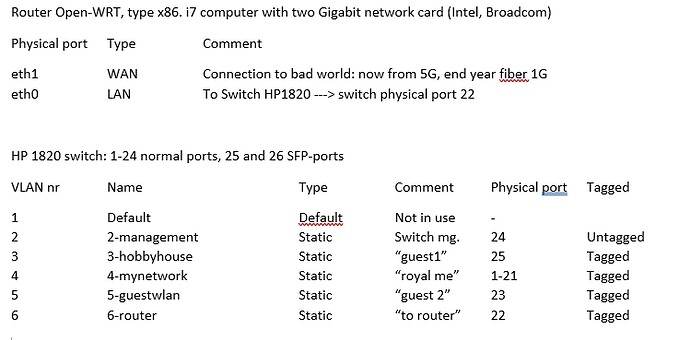
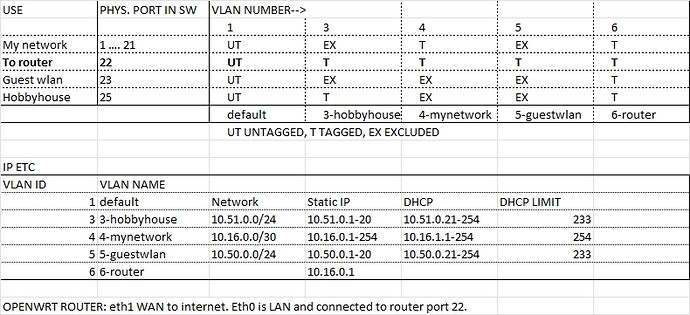
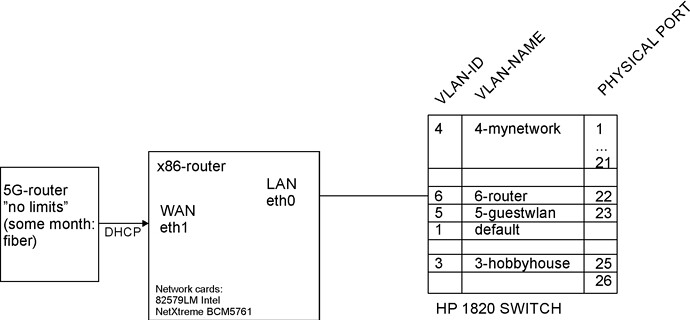
New configuration, so, this "VLAN", this "10.16" go to VLAN number 4.
This I cannot understand: "I have told you several times already: the start value should not be a full address. It is just a single number (like 21 instead of 10.51.0.21)." This must be wrong!?
Compare: "network", 10.16.0.1 etc, dhcp 10.16.1.1 etc. This work, all my network is filled with static-ip-devices (printers, etc). And when I put dhcp-device, voilá, ip is 10.16.1.1...254!
Now I add it two area more, 10.50.0.0/24 and 10.51.0.0/24. Of course: network-file "10.50.0.1" and dhcp 10.50.0.21 (and 51 same).
This logic does not go to my brains. Now "static 10.16.0.1, dhcp 10.16.1.1 and this is ok. But suddendly 10.50.0.1 static, DHCP NOT 10.50.0.21. Why this is not logical? "Sometimes in dhcp you must use full ip, sometimes only start- it is no any rule why, if ask why, it is no reason.... so, use dice..."
Network: No, I does not delete lan-zone. I read information you wrote earlier. "You does not need bridge" etc.
Here is one earlier configuration, now I fill it with last right information. But you said it was wrong...
config device
option type 'bridge'
option name 'br-BASIC'
option bridge_empty '1'
list ports 'eth0'
config device
option name 'br-hobbyhouse.3'
option type '8021q'
option ifname 'br-BASIC'
option vid '3'
config device
option name 'br-mynetwork.4'
option type '8021q'
option ifname 'br-BASIC'
option vid '4'
config device
option name 'br-guestwlan.5'
option type '8021q'
option ifname 'br-BASIC'
option vid '5'
config interface 'lan3'
option proto 'static'
option device 'br-hobbyhouse.3'
option netmask '255.255.255.0'
option gateway '10.51.0.1'
option ipaddr '10.16.0.1'
list dns '8.8.8.8'
config interface 'lan5'
option proto 'static'
option device 'br-guestwlan.5'
option netmask '255.255.255.0'
option gateway '10.50.0.1'
option ipaddr '10.16.0.1'
list dns '8.8.8.8'
config interface 'lan4'
option proto 'static'
option device 'br-mynetwork.4'
option netmask '255.255.252.0'
option gateway '10.16.0.1'
option ipaddr '10.16.0.1'
list dns '8.8.8.8'
This was any earlier configuration I try. I complete it now with last information, "locked" vlan numbers, names, ip:s. Now I cannot understand- is it any exact way how to make this? Please see my last complete configuration. So, I must add it "lan" to it set, but If I does not use bridge, how I add it? Please notify, my last complete configuration set.... I try follow your information as exact as possible. I read and read earlier discuss, also I google, read other thread, check videos- and no, no any information. My brains say, "only way make this is use bridge", but looks it is also wrong way?
I remove it lan... reason you said earlier this configuration was wrong :(.
--
In my opinion this my case is very, very typical. But, it is too typical- it is not possible found sample network, dhcp and firewall-files... but, I follow exactly all you wrote, but when I follow, "this is wrong". Also some details are fuzzy- eg. it dhcp start, "sometimes complete ip, sometimes only one number"- no logic....