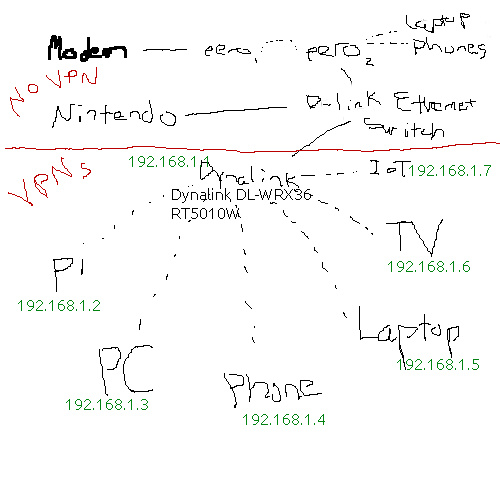
Using solid lines for wired connections, dashed lines for wireless connections.fla
(I have the Dynalink to serve as an OpenWRT device. Because OpenWRT has occasional issues like downed vpns, and I find it important that certain devices only ever use a vpn, and there are tech unsavvy people in the house, yes they will use their personal devices to access the internet without the OpenWRT providing policy based routing. Just easier for them rather than dead internet requiring me to troubleshoot.)
Plex is not on the OpenWrt system. Plex Server is running on a raspberry pi (192.168.1.2). Plex clients and web browsers acting as plex clients are not on the OpenWrt system. They are running on PC (192.168.1.3), Phone (192.168.1.4), and 192.168.1.6 (TV).
All devices seem to have access to WAN. I can access OpenWRT (192.168.1.1) on both Phone and PC. I cannot access pi via ssh or vnc from either Phone or PC. I cannot access the pi as a plex server from Phone or PC. However the TV can access the pi as a plex server. I expect, but cannot perform, that if I could ssh from TV to pi that they would connect. I do not know how to ssh into the TV from PC, and in attempting to I get a connection refused message.
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.137",
"hostname": "OpenWrt",
"system": "ARMv8 Processor rev 4",
"model": "Dynalink DL-WRX36",
"board_name": "dynalink,dl-wrx36",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ipq807x/generic",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'ip6address redacted out of caution::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
list dns '9.9.9.9'
list dns '149.112.112.112'
option broadcast '1'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2620:fe::fe' ; this is quad9's ip6 address, it is okay to publish, it is not private info accidentally being published
list dns '2620:fe::9' ; this is quad9's ip6 address, it is okay to publish, it is not private info accidentally being published
option auto '0'
config rule6
option priority '1'
option action 'blackhole'
option out 'wan'
option dest '::/0'
config interface 'vpnclient'
option proto 'none'
option device 'ovpnc0'
list dns '9.9.9.9'
list dns '149.112.112.112'
config interface 'vpnStream'
option proto 'none'
option device 'ovpnc1'
list dns '9.9.9.9'
list dns '149.112.112.112'
config interface 'vpnTorrent'
option proto 'none'
option device 'ovpnc2'
list dns '9.9.9.9'
list dns '149.112.112.112'
config interface 'vpnstate92'
option proto 'none'
option device 'ovpnc3'
list dns '9.9.9.9'
list dns '149.112.112.112'
config device
option name 'ovpnc3'
option ipv6 '0'
config device
option name 'ovpnc1'
option ipv6 '0'
config device
option name 'ovpnc0'
option ipv6 '0'
config device
option name 'ovpnc2'
option ipv6 '0'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/c000000.wifi'
option channel '44'
option band '5g'
option htmode 'HE80'
option country 'US'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'myssid 5ghz'
option encryption 'psk2'
option key 'mywifipassword'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/c000000.wifi+1'
option channel '4'
option band '2g'
option htmode 'HE20'
option country 'US'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'myssid 2.4ghz'
option encryption 'psk2'
option key 'mywifipassword'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '9.9.9.9'
list server '149.112.112.112'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'PC'
option ip '192.168.1.3'
option mac 'redacted'
option leasetime 'infinite'
option duid 'redacted'
config host
option name 'Phone'
option mac 'redacted'
option leasetime 'infinite'
option ip '192.168.1.4'
config host
option name 'raspberrypi'
option mac 'redacted redacted'
option ip '192.168.1.2'
option leasetime 'infinite'
config host
option name 'laptop'
option mac 'redacted'
option ip '192.168.1.5'
option leasetime 'infinite'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'ovpnc0'
list device 'ovpnc1'
list device 'ovpnc2'
list device 'ovpnc3'
list network 'wan'
list network 'wan6'
list network 'vpnclient'
list network 'vpnStream'
list network 'vpnTorrent'
list network 'vpnstate92'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'redacted 4-digit hex prefix?::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
To be clear, I would be able to fix everything and have to wait ~3 weeks to do a follow up if the Dynalink router was simply rebooted. That's what I did 3 weeks ago to fix it when I hit this issue. I'm going to try keeping it going as long as I can, and if the uptime stays >21 days and can resolve itself, cool. This is in part why I've waited months to post about it because I wanted to notice this pattern where we hit 20 days or 3 weeks mark (not quite sure what the earliest or average time of noticing the issue is) and be confident it wasn't a fluke.
When I first noticed this many months ago, I had been trying to ssh into the pi from my laptop and couldn't get in and did a series of tests seeing who could connect to who and basically found if A and B could talk, and C and D could talk, but A cannot get to C, then A could not get to D either and B could not get to C or D. It was as if they were on entirely different networks, or as if a virtual LAN is emerging spontaneously.
