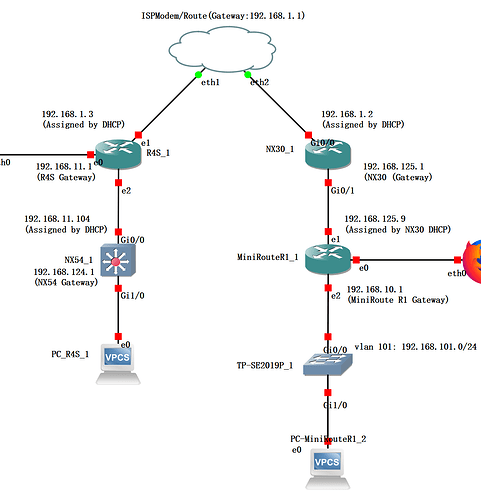
I have been using an Arm-based openWRT R4S device for the past 3 years. Recently, I decided to upgrade my internal network capability to 10G/2.5G, which requires me to update the hardware from R4S to Mini Route R1. The upgrade was rather straight forward and went without a hitch. That said, this did require me to migrate some of my internal service under R4S to Mini Route. I had a thought about it, Instead of migration, I can still retain R4S as a redundancy for some non-critical service just in case my Mini Route decide to quit. So I designed the following topology and implemented it under GNS3. After a bit of tuning, it worked (I do not have the proper firmware for NX30, NX54 and TP-Link Layer 2 Switch, so I used Cisco IOSv and IOSv2 instead.).
However, after I implemented the same configuration in the real environment, it just didn’t work. I would love for the some input so that I can proceed further. Please find my configuration below;
Static Routing
NX54
ip route 0.0.0.0 0.0.0.0 192.168.11.1
ip route 192.168.1.0 255.255.255.0 192.168.11.1
ip route 192.168.125.0 255.255.255.0 192.168.11.1
ip route 192.168.101.0 255.255.255.0 192.168.11.1
ip route 192.168.10.0 255.255.255.0 192.168.11.1
R4S
ip route 0.0.0.0 0.0.0.0 192.168.1.1
ip route 192.168.124.0 255.255.255.0 192.168.11.104
ip route 192.168.125.0 255.255.255.0 192.168.1.2
ip route 192.168.10.0 255.255.255.0 192.168.1.2
ip route 192.168.101.0 255.255.255.0 192.168.1.2
NX30
Ip route 0.0.0.0 0.0.0.0 192.168.1.1
Ip route 192.168.10.0 255.255.255.0 192.168.125.9
ip route 192.168.101.0 255.255.255.0 192.168.125.9
ip route 192.168.11.0 255.255.255.0 192.168..1.3
ip route 192.168.124.0 255.255.255.0 192.168.1.3
MiniRoute R1
ip route 0.0.0.0 0.0.0.0 192.168.125.1
ip route 192.168.1.0 255.255.255.0 192.168.125.1
ip route 192.168.11.0 255.255.255.0 192.168.125.1
ip route 192.168.124.0 255.255.255.0 192.168.125.1
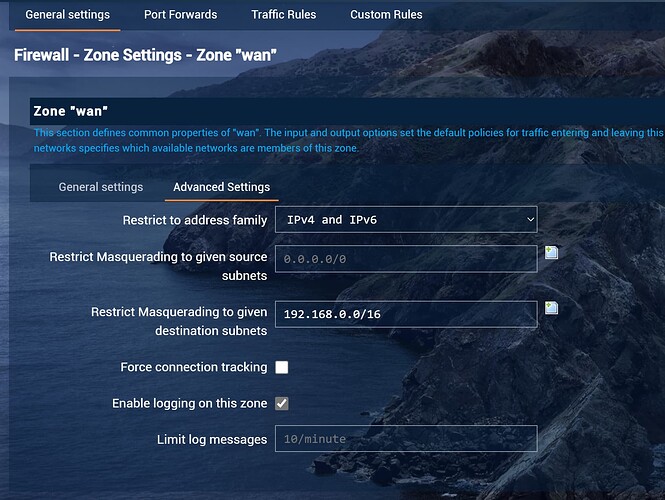
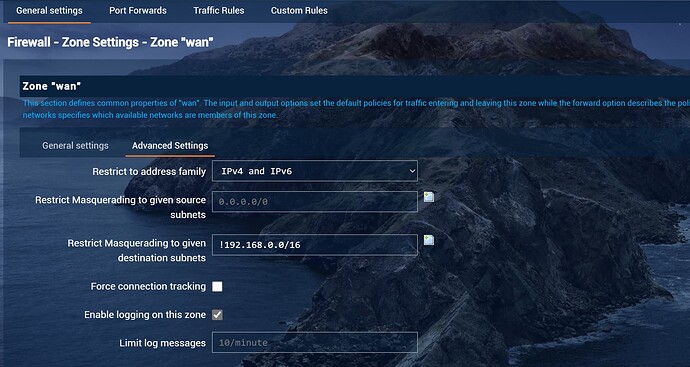
Firewall Setting
In GNS3, the only change I configured were the following;
R4S, in default, forward changed from ‘reject’ to ‘accept’
MiniRoute R1, WAN -> Reject, disable masquerade
I tried above in live environment, it didn’t work. Both PCs can reach Internet without any problem. However, they cannot reach each other. I tried ping to different segment, and I found the following;
R4S side can only reach up to 192.168.1.2 (Gateway of NX30).
MiniRoute side can only reach up to 192.168.1.3 (Gateway of R4S).
After the some investigation, I really can’t think of anything wrong with the routing. So I decided to continue experimenting on firewall. Because Miniroute is a bit hard to reload if anything goes wrong, I decided to make R4S pingable first. I tried following; but none worked.
Combination 1:
Default Firewall Behavior: accept, accept, accept
WAN -> Reject reject, accept, accept
Combination 2:
Default Firewall Behavior: accept, accept, accept
WAN -> Reject accept, accept, forward
Combination 3
Default Firewall Behavior: accept, accept, accept
WAN -> LAN reject, accept, accept
Combination 4
Default Firewall Behavior: accept, accept, accept
WAN -> Reject reject, accept, reject
A Firewall Rule
Home_Internal any protocol from 192.168.125.0/24 at WAN to all IPs in this device.
Also, interestingly, I can ping from PC under NX54 to 192.168.1.2. But after I sshed into R4s, I can ping 192.168.124.1, but not the terminal PC.
I’d appreciate it if someone can help me further this. Many thanks.