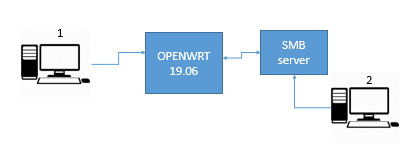
Hi, here is the result (I've removed some DNAT rules which are working fine and not really concern by this issue)
ubus call system board;
{
"kernel": "4.14.171",
"hostname": "Routeur",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "ZBT-WE3526",
"board_name": "zbtlink,zbt-we3526",
"release": {
"distribution": "OpenWrt",
"version": "19.07.2",
"revision": "r10947-65030d81f3",
"target": "ramips/mt7621",
"description": "OpenWrt 19.07.2 r10947-65030d81f3"
}
}
uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'XXXXXXXXXXXXX::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.1.1'
list dns '1.1.1.1'
list dns '208.67.222.222'
list dns '8.8.8.8'
option igmp_snooping '1'
config device 'lan_dev'
option name 'eth0.1'
option macaddr 'XXXXXXXXXXXXXXXX'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_dev'
option name 'eth0.2'
option macaddr 'XXXXXXXXXXXXXXXXX'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
option auto '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option network 'wan wan6'
option forward 'REJECT'
option input 'ACCEPT'
option masq '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config forwarding
option dest 'wan'
option src 'lan'
config redirect
option src 'wan'
option target 'DNAT'
option dest_ip '192.168.1.105'
option dest 'lan'
list proto 'udp'
option src_dport '137'
option name 'SAMBA_137'
option dest_port '137'
config redirect
option dest_port '138'
option src 'wan'
option name 'SAMBA_138'
option src_dport '138'
option target 'DNAT'
option dest_ip '192.168.1.105'
option dest 'lan'
list proto 'udp'
config redirect
option src 'wan'
option name 'SAMBA_139'
option src_dport '139'
option target 'DNAT'
option dest_ip '192.168.1.105'
option dest 'lan'
list proto 'tcp'
option dest_port '139'
config redirect
option src 'wan'
option name 'SAMBA_445'
option src_dport '445'
option target 'DNAT'
option dest_ip '192.168.1.105'
option dest 'lan'
list proto 'tcp'
option dest_port '445'
head -n -0 /etc/firewall.user;
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
iptables-save -c
# Generated by iptables-save v1.8.3 on Fri Jul 23 14:25:53 2021
*nat
:PREROUTING ACCEPT [539569:44735413]
:INPUT ACCEPT [225532:15394099]
:OUTPUT ACCEPT [26638:1957428]
:POSTROUTING ACCEPT [285780:17145688]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[825294:61864901] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[527834:43972331] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[297460:17892570] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[606617:40088765] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[285778:17145544] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[320837:22943077] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[285778:17145544] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.105/32 -p udp -m udp --dport 137 -m comment --comment "!fw3: SAMBA_137 (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.105/32 -p udp -m udp --dport 138 -m comment --comment "!fw3: SAMBA_138 (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.105/32 -p tcp -m tcp --dport 139 -m comment --comment "!fw3: SAMBA_139 (reflection)" -j SNAT --to-source 192.168.1.1
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.105/32 -p tcp -m tcp --dport 445 -m comment --comment "!fw3: SAMBA_445 (reflection)" -j SNAT --to-source 192.168.1.1
[527834:43972331] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 192.168.0.16/32 -p udp -m udp --dport 137 -m comment --comment "!fw3: SAMBA_137 (reflection)" -j DNAT --to-destination 192.168.1.105:137
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 192.168.0.16/32 -p udp -m udp --dport 138 -m comment --comment "!fw3: SAMBA_138 (reflection)" -j DNAT --to-destination 192.168.1.105:138
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 192.168.0.16/32 -p tcp -m tcp --dport 139 -m comment --comment "!fw3: SAMBA_139 (reflection)" -j DNAT --to-destination 192.168.1.105:139
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 192.168.0.16/32 -p tcp -m tcp --dport 445 -m comment --comment "!fw3: SAMBA_445 (reflection)" -j DNAT --to-destination 192.168.1.105:445
[320837:22943077] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[320837:22943077] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[297460:17892570] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[11:858] -A zone_wan_prerouting -p udp -m udp --dport 137 -m comment --comment "!fw3: SAMBA_137" -j DNAT --to-destination 192.168.1.105:137
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 138 -m comment --comment "!fw3: SAMBA_138" -j DNAT --to-destination 192.168.1.105:138
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 139 -m comment --comment "!fw3: SAMBA_139" -j DNAT --to-destination 192.168.1.105:139
[217:11172] -A zone_wan_prerouting -p tcp -m tcp --dport 445 -m comment --comment "!fw3: SAMBA_445" -j DNAT --to-destination 192.168.1.105:445
COMMIT
# Completed on Fri Jul 23 14:25:53 2021
# Generated by iptables-save v1.8.3 on Fri Jul 23 14:25:53 2021
*mangle
:PREROUTING ACCEPT [145593797:126831038161]
:INPUT ACCEPT [265724:20929472]
:FORWARD ACCEPT [145308290:126801769224]
:OUTPUT ACCEPT [305130:26922169]
:POSTROUTING ACCEPT [145612270:126828624545]
[567536:34005652] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Fri Jul 23 14:25:53 2021
# Generated by iptables-save v1.8.3 on Fri Jul 23 14:25:53 2021
*filter
:INPUT ACCEPT [157:12865]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_ACCEPT - [0:0]
[77:6762] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[265647:20922710] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[31207:4175610] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[10089:428956] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[215329:14757193] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[19111:1989907] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[145308290:126801769224] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[144703135:126761542875] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[297929:21805829] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[307226:18420520] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[93:9194] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[305037:26912975] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[278212:24923795] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[119:34657] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[26706:1954523] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[10089:428956] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[119:34657] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[297929:21805829] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[297929:21805829] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[215329:14757193] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[215329:14757193] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[119:34657] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[119:34657] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[215318:14756621] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[1156:68840] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[323479:23691512] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[307226:18420520] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[307226:18420520] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[19111:1989907] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[1180:37760] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[17931:1952147] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_ACCEPT
[26706:1954523] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[26706:1954523] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[17785:1939854] -A zone_wan_src_ACCEPT -i eth0.2 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
COMMIT
# Completed on Fri Jul 23 14:25:54 2021
ip -4 addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.0.16/24 brd 192.168.0.255 scope global eth0.2
valid_lft forever preferred_lft forever
ip -4 ro li tab all
default via 192.168.0.1 dev eth0.2 src 192.168.0.16
192.168.0.0/24 dev eth0.2 scope link src 192.168.0.16
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.0.0 dev eth0.2 table local scope link src 192.168.0.16
local 192.168.0.16 dev eth0.2 table local scope host src 192.168.0.16
broadcast 192.168.0.255 dev eth0.2 table local scope link src 192.168.0.16
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
ip -4 ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default