ccchan
September 15, 2020, 2:34am
19
hi, thx but....
Yes, the ports are unusual, however,
So, even using a stock TP1ink C2 archer,
THE ONLY THING I changed is the router, from C2 to openwrt (commercial GL inet BrumeW, or self flashed openwrt 20.x D1ink 842).
So i think the problem lies on the openwrt routers' settings.
If you mean I need "connect/forward" unusual ports on android to usual ports on win10,
thanks
ccchan
September 15, 2020, 2:50am
20
hi,
Yeah the D1ink 842 is flashed with the lastest snapshot of openwrt.
it's info here:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd4c:758e:daaa::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr 'xx.xx.xx.xx.xx.xx'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xx.xx.xx.xx.xx.xx'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
# allow interoperability with traceroute classic
# note that traceroute uses a fixed port range, and depends on getting
# back ICMP Unreachables. if we're operating in DROP mode, it won't
# work so we explicitly REJECT packets on these ports.
config rule
option name Support-UDP-Traceroute
option src wan
option dest_port 33434:33689
option proto udp
option family ipv4
option target REJECT
option enabled false
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
### EXAMPLE CONFIG SECTIONS
# do not allow a specific ip to access wan
#config rule
# option src lan
# option src_ip 192.168.45.2
# option dest wan
# option proto tcp
# option target REJECT
# block a specific mac on wan
#config rule
# option dest wan
# option src_mac 00:11:22:33:44:66
# option target REJECT
# block incoming ICMP traffic on a zone
#config rule
# option src lan
# option proto ICMP
# option target DROP
# port redirect port coming in on wan to lan
#config redirect
# option src wan
# option src_dport 80
# option dest lan
# option dest_ip 192.168.16.235
# option dest_port 80
# option proto tcp
# port redirect of remapped ssh port (22001) on wan
#config redirect
# option src wan
# option src_dport 22001
# option dest lan
# option dest_port 22
# option proto tcp
### FULL CONFIG SECTIONS
#config rule
# option src lan
# option src_ip 192.168.45.2
# option src_mac xx.xx.xx.xx.xx.xx
# option src_port 80
# option dest wan
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
# option target REJECT
#config redirect
# option src lan
# option src_ip 192.168.45.2
# option src_mac 0xx.xx.xx.xx.xx.xx
# option src_port 1024
# option src_dport 80
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'tplink'
option dns '1'
option mac 'xx.xx.xx.xx.xx.xx'
option ip '192.168.1.93'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.8.4 on Mon Sep 14 21:50:35 2020
*nat
:PREROUTING ACCEPT [992:97805]
:INPUT ACCEPT [735:49841]
:OUTPUT ACCEPT [224:21795]
:POSTROUTING ACCEPT [224:21795]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[992:97805] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[992:97805] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[224:21795] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[2:680] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[2:680] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[992:97805] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Mon Sep 14 21:50:35 2020
# Generated by iptables-save v1.8.4 on Mon Sep 14 21:50:35 2020
*mangle
:PREROUTING ACCEPT [8238:1072896]
:INPUT ACCEPT [7981:1024932]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [10245:7992593]
:POSTROUTING ACCEPT [10245:7992593]
[0:0] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Mon Sep 14 21:50:35 2020
# Generated by iptables-save v1.8.4 on Mon Sep 14 21:50:35 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[2288:214818] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[5695:810194] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[4860:751639] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[9:468] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[835:58555] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[0:0] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[2288:214818] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[7962:7778723] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[7960:7778043] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2:680] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[9:468] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[2:680] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[835:58555] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[835:58555] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[2:680] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[2:680] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[835:58555] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[0:0] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[0:0] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Mon Sep 14 21:50:35 2020
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
thx
pwned
September 15, 2020, 10:45am
21
How do you try to access your shares? Using IP or Hostname? For me it sounds like a name resolution issue. I can imagine that your TP-Link Archer C2 is running it's own samba server using Netbios/WINS (running as a master) to do name resolution for all samba servers and clients. This is not the case for a plain OpenWrt installation.
krazeh
September 15, 2020, 1:02pm
23
The pc and Android device are in the same subnet right? I.e. they both have a 192.168.1.x address?
pwned
September 15, 2020, 1:12pm
24
I got this already. I want to know how your phone is accessing the share. Over plain IP or hostname? E. g. smb://192.168.x.x or smb://mypc
ccchan
September 15, 2020, 1:14pm
25
yes,
for TP link that will be 192.168.0.*
for ALL combinations,
btw, PC-A, even with the multi port forwarder ON,
thx
ccchan
September 15, 2020, 1:18pm
27
LANdrive is the only android app I know that act as samba SERVER while you dont need the phone rooted i.e. it works UNROOTED.
ccchan
September 15, 2020, 1:21pm
28
provided every ping is working, every FTP into is working,
and the landrive working in TPlink and NOT working with openwrt (two different openwrt).
I simply can conclude it's the openwrt somehow prevented the landrive from working.
I could further do a regular testing later when free.
thanks
krazeh
September 15, 2020, 1:32pm
29
I've just installed LAN drive onto my phone and installed multi port forwarder on my pc. It works without any issues or needing to make any changes on my router.
I would double check the IP address assigned to the phone when you use a different router and ensure that any change has been updated in the multi port forwarder rules.
2 Likes
ccchan
September 15, 2020, 1:39pm
30
wow is it!?
using the phone as samba SERVER?!
let me try again and let me close all win/android firewall then!
thanks first.
krazeh
September 15, 2020, 1:41pm
31
Yep, literally just installed the app off the play store and added the rules in multi port forwarder as described in their tutorial. Then just used my phone's IP address in explorer (i.e. \\192.168.1.x\) to connect and browse the local storage.
1 Like
ccchan
September 15, 2020, 1:53pm
32
hi~
mind to try copy/move some files into the phone's share? becoz i could enter but it say "this folder is empty" but indeep it is not connected. thanks
krazeh
September 15, 2020, 1:58pm
33
I can only do limited testing as I don't have the full version and the trial is very speed limited, but I can open files stored on the phone from my pc so it's definitely connected.
2 Likes
ccchan
September 15, 2020, 2:06pm
34
ok, thank you.
i will check on my side, thanks
ccchan
October 11, 2020, 7:37pm
35
It's all MY faults, I apologize for this.
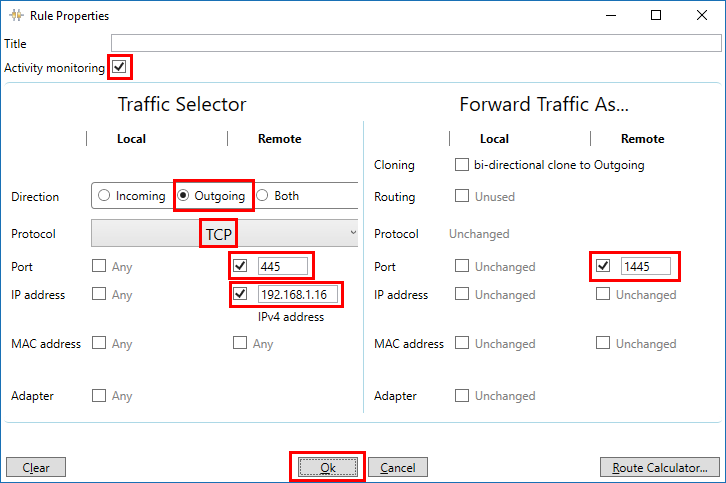
In Verigio, in the TCP tab, there is a hard code-ed IP address,
So I setup my Tplink within the trial period, thus working well.
Very much Thank you esp to Krazeh who helped by installing the app and software for me.
(PS seems that one have to buy the ultimate version of
The tutorial of landrive is here:
Esp TCP
The limitation of trial version of verigio is here:
tmomas
October 12, 2020, 3:19pm
36
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
ccchan
October 12, 2020, 3:45pm
37
title cant be changed,#5 ,
1 Like
system
October 22, 2020, 3:45pm
38
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.