Hello,
I've used openwrt as my main router for quite some time now and it works to the perfection. Recently, I started to use VLAN to have a somehow cleaner network infrastructure to separate my lan, from my dmz and from another "lan" network for IOT with access to wan disabled.
Today, I changed my ISP and upgraded my PC and my NAS to 2.5gbps and it led me to significant changes.
The things to know first are :
- I want my connection PC-NAS to be 2.5gbps
- I want my connection PC-Internet to be 2.5gbps
- My OpenWrt router is only 1gbps on WAN and on all 4 LAN ports
- My ISP router provides a single 2.5gbps port, and then two 1gbps ports
- I want to have a DMZ with various virtual machine that can be accessed from the internet (behind nat)
- I don't want these DMZ machines to access my LAN
- I want my LAN to be able to access my DMZ (ideally without adding a custom route on my computer)
- I want my OpenWrt router to emit a WLAN for my IOT devices that won't have access to anything (no WAN, no LAN, no DMZ). But at least one LAN machine should be able to reach
- I have a 2.5gbps unmanaged switch
- ISP router does not support vlan
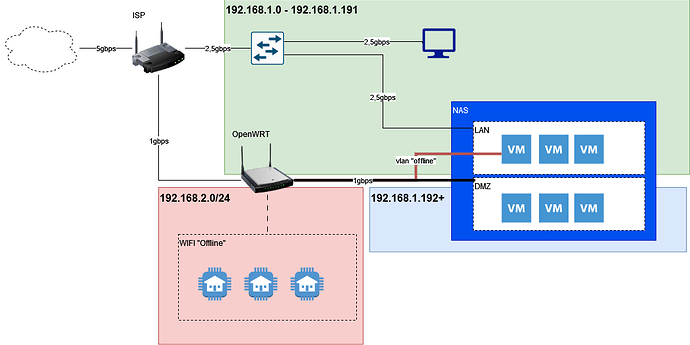
So with all that, I thought about doing something like that:
The idea is to have one 192.168.1.0/24 network that would contain both LAN and DMZ (allowing LAN to contact DMZ without manually adding route on my LAN machines).
The DMZ part would be differentiated by either a sub-range (192.168.1.192/26) or simply by the physical ports on my openwrt router.
The openwrt router would just bridge the ISP router to the DMZ adding some firewall rules in-between to limit the DMZ exchanges.
For the IOT part, I'd have a dedicated wlan interface on my router with its own dhcp server and no forwarding rules between zones. Then a VM would have a network interface with the appropriate VLAN to access these devices.
And then... I tried to implement all that. But it doesn't quite work :
- I don't seem to be able to control the traffic from my DMZ to my LAN
- EDIT: no longer true apparently? //I can't connect to my 'iot' wifi. In OpenWRT it shows my device getting an IP but my device reports getting no IP//
So, do you have idea recommendation/improvement regarding my base design?
Then, do you have an idea of what I have done wrong?
Network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fd0d:56a4:b54e::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'wan'
config interface 'lan'
option proto 'dhcp'
option device 'br-lan.1'
config interface 'offline'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option device 'br-lan.2'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1:u*'
list ports 'lan2:u*'
list ports 'lan3:u*'
list ports 'lan4:u*'
list ports 'wan:u*'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan1:t'
config device
option name 'br-lan.1'
option type '8021q'
option ifname 'br-lan'
option vid '1'
Firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'offline'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'offline'
option forward 'ACCEPT'
config include
option path '/etc/firewall.user'
# not working:
config rule
option src 'lan'
list src_ip '192.168.1.192/26'
option dest 'lan'
list dest_ip '!192.168.1.192/26'
list proto 'all'
option target 'REJECT'
Wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option encryption 'psk2'
option key 'myPassword'
option network 'offline'
option ssid 'IOT'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option disabled '1'
DHCP
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option dhcpv4 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option start '200'
option limit '50'
option leasetime '7d'
option ra 'hybrid'
option dhcpv6 'hybrid'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'offline'
option interface 'offline'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
list ra_flags 'none'