Context
I have known about Pi-hole quite a while from now. Initially, I started to use as ad blocker by pointing router to use Pi-hole's DNS services.
Later I discovered I can also use custom domains. So I've been configuring <service>.mydomain.tld to point to a reverse proxy IP.
With DNS for LAN pointed to the Pi-hole instance, the custom domain worked network wide.
Problem & Questions
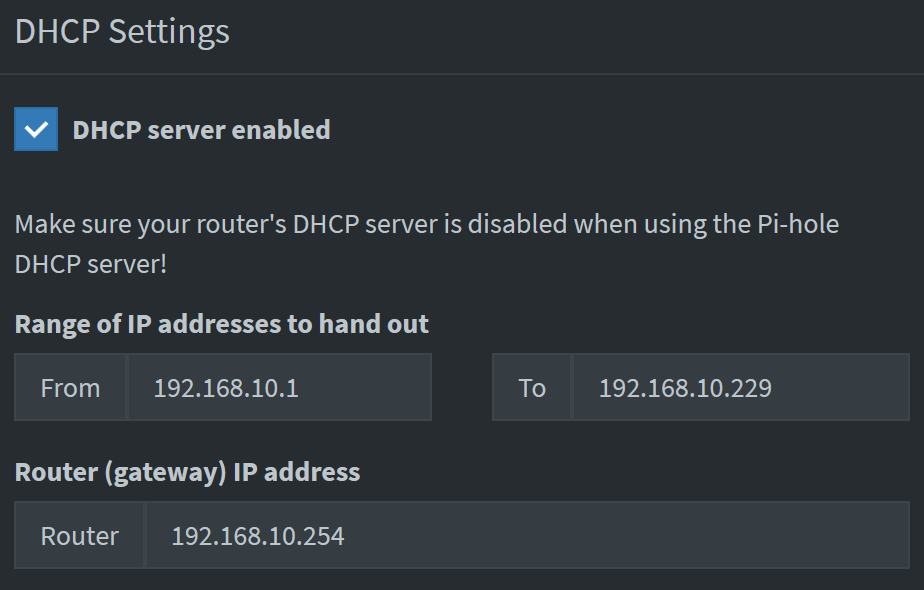
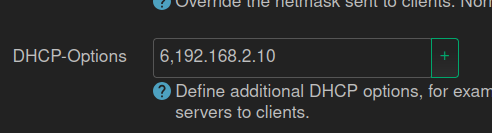
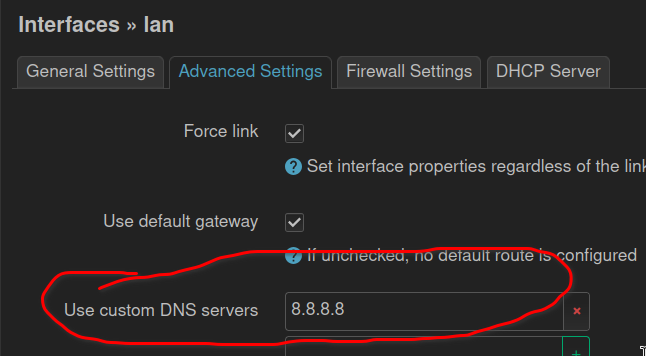
After having a working instance of OpenWrt on my main router, I followed the same setting to point DNS to Pi-hole instance IP. This time, this does not seem to be working. Neither ad blocking, nor custom domain.
Why is Pi-hole not working out of the box? Do I need to make any additional configuration?
At this point, I understand OpenWrt will be able to handle stuff Pi-hole was handing. So my question would be:
Any solution for adblocking + custom local domains native to OpenWrt?
Along the same lines, I have another question:
Is there a clever way to make custom domains work for client who also want to use VPN?
(for the later one, whenever I used a VPN provider on a device, my adblock and custom domains were useless, that's because VPN provider uses their own DNS for the connection)
Maybe I'm asking too much with DNS + VPN, but I have to get my DNS based adblocking and custom domains back to work.
Please point me to correct documentation. Thank you for your time in advance.