Hi,
The OpenWrt community is proud to announce the second release candidate of the upcoming OpenWrt 24.10 stable series.
OpenWrt 24.10.0-rc2 incorporates over 5100 commits since branching the previous OpenWrt 23.05 release and has been under development for over one year.
This is just a release candidate and not the final release yet.
Download firmware images using the OpenWrt Firmware Selector:
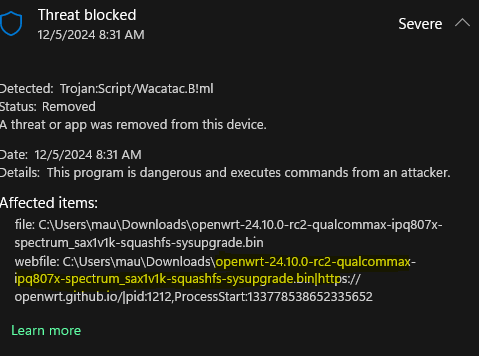
- https://openwrt.github.io/firmware-selector-openwrt-org?version=24.10.0-rc2
Download firmware images directly from our download servers: - https://downloads.openwrt.org/releases/24.10.0-rc2/targets/
Please test this version
This is not the final version, this is a test version. Please report problems and bugs in our issue tracker. https://github.com/openwrt/openwrt/issues
Changes between OpenWrt 24.10.0-rc1 and 24.10.0-rc2
- Fixed opkg installation of kernel modules. The path to the kernel module packages was fixed.
For a detailed list of changes since OpenWrt 24.10.0-rc2 see the 24.10.0-rc2 changelog.
Highlights in OpenWrt 24.10:
General changes
- TLS 1.3 support in default images
- mbedtls was updated to version 3.6 which includes support for TLS 1.3
- Activate POSIX Access Control Lists and file system security attributes for all file systems on devices with big flash sizes. This is needed by docker nowadays.
- Activate kernel support for Multipath TCP on devices with big flash sizes.
- Improved support for WiFi6 (802.11ax) and initial support for WiFi7 (802.11be)
- Not many Wifi7 devices are supported by OpenWrt yet
- Improved Link Layer Discovery Protocol (LLDP) support
- OpenWrt 24.10 uses OPKG only, APK packages are not supported. Only main branch was changed to APK.
Many new devices added
OpenWrt 24.10 supports over 1950 devices. Support for over 100 new devices was added in addition to the device support by OpenWrt 23.05.
- Added support for OpenWrt One
Target changes
- Added d1 target for AllWinner D1 RISC-V SoC
- Added ixp4xx target for Intel XScale IXP4xx SoCs.
- Added loongarch64 target for SoCs with Loongson LoongArch CPUs.
- Added starfive target for StarFive JH71x0 (7100/7110) SoCs.
- Added stm32 target for STMicroelectronics STM32 SoCs.
- Renamed ipq807x target to qualcommax.
- Removed ath25 target. It supported Atheros ieee80211g devices with maximum 16MB RAM
- Removed bcm63xx target. It supported some Broadcom DSL MIPS SoCs and was replaced by the bmips target. The Broadcom DSL itself was never supported.
- Removed octeontx target. It supported the Octeon-TX CN80XX/CN81XX based boards.
- Removed oxnas target. It supported the PLXTECH/Oxford NAS782x/OX8xx.
- The qoriq target for the NXP QorIQ (PowerPC) SoCs is build
- The ipq806x target for Qualcomm Atheros IPQ806X SoCs was converted to DSA
Core components update
Core components have the following versions in 24.10.0-rc2:
- Updated toolchain:
- musl libc 1.2.5
- glibc 2.38
- gcc 13.3.0
- binutils 2.42
- Updated Linux kernel
- 6.6.63 for all targets
- Network:
- hostapd master snapshot from September 2024, dnsmasq 2.90, dropbear 2024.86
- cfg80211/mac80211 from kernel 6.11.2
Upgrading to 24.10
Sysupgrade can be used to upgrade a device from 23.05 to 24.10, and configuration will be preserved in most cases.
-
Sysupgrade from 22.03 to 24.10 is not officially supported.
-
There is no configuration migration path for users of the ipq806x target for Qualcomm Atheros IPQ806X SoCs because it switched to DSA. You have to upgrade without saving the configuration.
-
User of the Linksys E8450 aka. Belkin RT3200 running OpenWrt 23.05 or earlier will need to run installer version v1.1.3 or later in order to reorganize the UBI layout for the 24.10 release. A detailed description is in the OpenWrt forum. Updating without using the installer will break the device. Sysupgrade will show a warning before doing an incompatible upgrade.
-
Users of the Xiaomi AX3200 aka. Redmi AX6S running OpenWrt 23.05 or earlier have to follow a special upgrade procedure described in the wiki. This will increase the flash memory available for OpenWrt. Updating without following the guide in the wiki break the device. Sysupgrade will show a warning before doing an incompatible upgrade.
Full release notes and upgrade instructions are available at
https://openwrt.org/releases/24.10/notes-24.10.0-rc2
In particular, make sure to read the regressions and known issues before upgrading:
https://openwrt.org/releases/24.10/notes-24.10.0-rc2#known_issues
For a detailed list of all changes since 24.10.0-rc1, refer to
https://openwrt.org/releases/24.10/changelog-24.10.0-rc2
To download the 24.10.0-rc2 images, navigate to:
https://downloads.openwrt.org/releases/24.10.0-rc2/targets/
Use OpenWrt Firmware Selector to download:
https://openwrt.github.io/firmware-selector-openwrt-org?version=24.10.0-rc2
As always, a big thank you goes to all our active package maintainers, testers, documenters and supporters.
Have fun!
The OpenWrt Community
To stay informed of new OpenWrt releases and security advisories, there
are new channels available:
-
a low-volume mailing list for important announcements:
https://lists.openwrt.org/mailman/listinfo/openwrt-announce -
a dedicated "announcements" section in the forum:
https://forum.openwrt.org/c/announcements/14 -
other announcement channels (such as RSS feeds) might be added in the
future, they will be listed at https://openwrt.org/contact