Do we need to create a template to configure the "local" captive portal system ( OpenNDS in our case, but I see Coovachilli in your github repo ) to speak to OpenWISP Radius and set up the specific networks / VLANs which should have captive portal ( template for the openNDS or Coova config files with Radius server / authentication server details, walled garden IP/ domains, local networks to intercept, directory of captive portal resources - php/ html.. whatever is sent to the client )?
Yes, templates if you want these configurations to be easily updatable from a central point, alternatively you can build the configurations into your firmware.
Does openwisp_config on the network device fetch the Web pages form the OpenWisp server and save it locally ( for Coova or OpenNDS to use )-> and how is this set up ?
The agent fetches whatever you put in templates, you can put files too although I wouldn't recommend defining web pages as templates, it would be a stretch and probably result in something painful to maintain.
For those who use RADIUS we have built an application which is designed to be hosted on a server and which can provide the web portal to sign up, perform log in to the captive portal, reset password, SMS verification and so on, this is called wifi-login-pages.
Is there a way to use the overlay network ( Wireguard / OpenVPN ) to get SSH access to devices for in field debugging -> like using https://xtermjs.org/ or something similar )
The tunnels can be used for management purposes, we just use SSH, HTTP and SNMP at the moment.
I like the idea of having the metrics/ monitoring more extensible to set up "strange" monitoing things, or call a local script to assemble data ( like connected users to a specific network , some networks are bridges of many interfaces like eth VLANS from dumb APs, multiple wifi cards etc ), or to figure out the current path thru the mesh taht batman-adv has chosen - need to do a batctl tr <current gateway> to get that traceroute to assist in mesh planning.
or to get wifi signal details for cleints and repeaters( iw <wlanx-y> station dump ).
Hopefully there will be enough interest in the near future to allow to easily define and collect custom metrics.
Right now it is possible to execute custom linux/unix commands and even define new commands in the UI which make it easier to send custom commands for less experienced users.
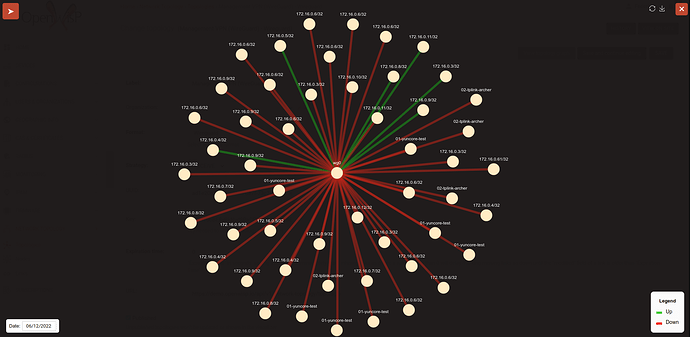
There's also a network topology module which is able to collect, store historic daily snapshots and visualize, network topology data (also from batman-adv), which can be also accessed via REST API.
In the OpenWISP demo system we are collecting topology data for OpenVPN and Wireguard.
Any interest in using MQTT as a way of submitting data form network devices to the server ?
Yes definitely, although I see this as a long term goal and not necessarily a short term pressing need.
When I started rewriting OpenWISP, I stayed as close as possible to the old system for different reasons, then I focused on building other features that I needed for the projects I have been working on, but over time is becoming clear that there's different parts of the system which need to be redesigned, and one of these is the way agents communicate with the server. I have been thinking about MQTT or MQTT over WebSocket as possible solutions.
I also think it's possible to allow OpenWISP to support standard protocols like TR069 or Netconf. Ideally we'll be able to support multiple protocols and multiple embedded OSes, that is my personal goal.