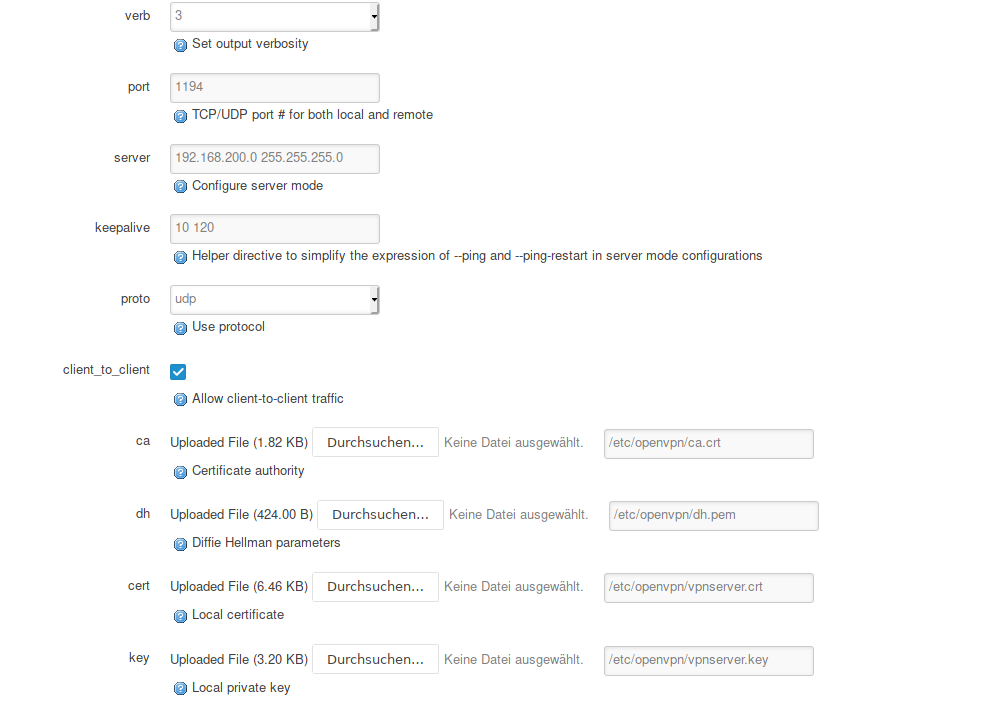
Thank you it works now. However when I connect this Error occurs. Seems to be some local problem but maybe you can help. My machine is running Arch Linux
[me@linux ~]$ sudo openvpn vpn.ovpn
Fri Feb 15 12:28:55 2019 OpenVPN 2.4.6 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Apr 24 2018
Fri Feb 15 12:28:55 2019 library versions: OpenSSL 1.1.1a 20 Nov 2018, LZO 2.10
Fri Feb 15 12:28:55 2019 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Feb 15 12:28:55 2019 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Feb 15 12:28:55 2019 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
Fri Feb 15 12:28:55 2019 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
Fri Feb 15 12:28:55 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]IP
Fri Feb 15 12:28:55 2019 Socket Buffers: R=[212992->212992] S=[212992->212992]
Fri Feb 15 12:28:55 2019 UDP link local: (not bound)
Fri Feb 15 12:28:55 2019 UDP link remote: [AF_INET]IP
Fri Feb 15 12:28:55 2019 TLS: Initial packet from [AF_INET]IP, sid=7d44b3b5 0739ad0a
Fri Feb 15 12:28:56 2019 VERIFY OK: depth=1, CN=vpnca
Fri Feb 15 12:28:56 2019 VERIFY KU OK
Fri Feb 15 12:28:56 2019 Validating certificate extended key usage
Fri Feb 15 12:28:56 2019 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Fri Feb 15 12:28:56 2019 VERIFY EKU OK
Fri Feb 15 12:28:56 2019 VERIFY OK: depth=0, CN=vpnserver
Fri Feb 15 12:28:56 2019 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1541', remote='link-mtu 1542'
Fri Feb 15 12:28:56 2019 WARNING: 'comp-lzo' is present in remote config but missing in local config, remote='comp-lzo'
Fri Feb 15 12:28:56 2019 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Fri Feb 15 12:28:56 2019 [vpnserver] Peer Connection Initiated with [AF_INET]IP
Fri Feb 15 12:28:57 2019 SENT CONTROL [vpnserver]: 'PUSH_REQUEST' (status=1)
Fri Feb 15 12:28:57 2019 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,compress lzo,persist-tun,persist-key,dhcp-option DOMAIN lan,redirect-gateway def1,route 192.168.1.0 255.255.255.0,dhcp-option DNS 192.168.1.1,compress lzo,persist-tun,persist-key,dhcp-option DOMAIN lan,redirect-gateway def1,dhcp-option DOMAIN lan,dhcp-option DNS 192.168.1.1,persist-tun,persist-key,redirect-gateway def1,dhcp-option DOMAIN lan,dhcp-option DNS 192.168.1.1,persist-tun,persist-key,redirect-gateway def1,dhcp-option DOMAIN lan,dhcp-option DNS 192.168.1.1,persist-tun,persist-key,redirect-gateway def1,dhcp-option DOMAIN lan,dhcp-option DNS 192.168.1.1,persist-tun,persist-key,route-gateway 192.168.8.1,topology subnet,ping 10,ping-restart 120,ifconfig 192.168.8.2 255.255.255.0,peer-id 0,cipher AES-256-GCM'
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: timers and/or timeouts modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: compression parms modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: --persist options modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: --ifconfig/up options modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: route options modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: route-related options modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: peer-id set
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: adjusting link_mtu to 1624
Fri Feb 15 12:28:57 2019 OPTIONS IMPORT: data channel crypto options modified
Fri Feb 15 12:28:57 2019 Data Channel: using negotiated cipher 'AES-256-GCM'
Fri Feb 15 12:28:57 2019 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Feb 15 12:28:57 2019 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Fri Feb 15 12:28:57 2019 ROUTE_GATEWAY 192.168.43.1/255.255.255.0 IFACE=wlp3s0 HWADDR=MAC
Fri Feb 15 12:28:57 2019 TUN/TAP device tun0 opened
Fri Feb 15 12:28:57 2019 TUN/TAP TX queue length set to 100
Fri Feb 15 12:28:57 2019 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Fri Feb 15 12:28:57 2019 /usr/bin/ip link set dev tun0 up mtu 1500
Fri Feb 15 12:28:57 2019 /usr/bin/ip addr add dev tun0 192.168.8.2/24 broadcast 192.168.8.255
Fri Feb 15 12:28:57 2019 /usr/bin/ip route add 91.64.43.171/32 via 192.168.43.1
Fri Feb 15 12:28:57 2019 /usr/bin/ip route add 0.0.0.0/1 via 192.168.8.1
Fri Feb 15 12:28:57 2019 /usr/bin/ip route add 128.0.0.0/1 via 192.168.8.1
Fri Feb 15 12:28:57 2019 /usr/bin/ip route add 192.168.1.0/24 via 192.168.8.1
Fri Feb 15 12:28:57 2019 /usr/bin/ip route add 192.168.1.0/24 via 192.168.8.1
RTNETLINK answers: File exists
Fri Feb 15 12:28:57 2019 ERROR: Linux route add command failed: external program exited with error status: 2
Fri Feb 15 12:28:57 2019 Initialization Sequence Completed
Also hostname dont seem to be working. I can access 192.168.1.1 but not openwrt.lan