Hi,
I'm trying to configure OpenVPN to work with Stunnel.
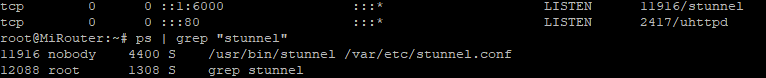
The problem is that, even I have tried to apply the config of Stunnel to Listen on 443 TCP, stunnel keep listening on 6000.
The config of stunnel.conf:
pid = /var/run/stunnel.pid
setuid = nobody
setgid = nogroup
socket = l:TCP_NODELAY=1
socket = r:TCP_NODELAY=1
cert = /etc/stunnel/stunnel.pem
foreground = yes
output = /var/log/stunnel.log
[openvpn]
client = no
accept = 0.0.0.0:443
connect = localhost:5567
OpenVPN could connect properly without Stunnel, but when using Stunnel, the log say that the connection is refused on 443 tcp post of server.
Any suggestion or solutions for this, it made me mad 2 days already :'(.
P/s: I found that everytime I start stunnel, the conf in /var/etc/stunnel.conf will automatically re-gen by uci
; STunnel configuration file generated by uci
; Written Fri Mar 12 17:42:55 2021
Is there anyway to change the conf location? I want to change it to /etc/stunnel/stunnel.conf.
Running stunnel only:
root@MiRouter:~# stunnel
[ ] Initializing inetd mode configuration
[ ] Clients allowed=500
[.] stunnel 5.58 on mipsel-openwrt-linux-gnu platform
[.] Compiled/running with OpenSSL 1.1.1j 16 Feb 2021
[.] Threading:PTHREAD Sockets:POLL,IPv6 TLS:ENGINE,OCSP,PSK,SNI
[ ] errno: (*__errno_location())
[ ] Initializing inetd mode configuration
[.] Reading configuration from file /etc/stunnel/stunnel.conf
[.] UTF-8 byte order mark not detected
[.] FIPS mode disabled
[ ] No PRNG seeding was required
[ ] Initializing service [openvpn]
[ ] stunnel default security level set: 2
[ ] Ciphers: HIGH:!aNULL:!SSLv2:!DH:!kDHEPSK
[ ] TLSv1.3 ciphersuites: TLS_AES_256_GCM_SHA384:TLS_AES_128_GCM_SHA256:TLS_CHACHA20_POLY1305_SHA256
[ ] TLS options: 0x02100004 (+0x00000000, -0x00000000)
[ ] Loading certificate from file: /etc/stunnel/stunnel.pem
[ ] Certificate loaded from file: /etc/stunnel/stunnel.pem
[ ] Loading private key from file: /etc/stunnel/stunnel.pem
[:] Insecure file permissions on /etc/stunnel/stunnel.pem
[ ] Private key loaded from file: /etc/stunnel/stunnel.pem
[ ] Private key check succeeded
[ ] DH initialization skipped: no DH ciphersuites
[ ] ECDH initialization
[ ] ECDH initialized with curves X25519:P-256:X448:P-521:P-384
[.] Configuration successful
[ ] Deallocating deployed section defaults
[ ] Binding service [openvpn]
[ ] Listening file descriptor created (FD=10)
[ ] Setting accept socket options (FD=10)
[ ] Option SO_REUSEADDR set on accept socket
[ ] Service [openvpn] (FD=10) bound to 0.0.0.0:443
[!] Cannot open log file: /var/log/stunnel.log
[ ] Unbinding service [openvpn]
[ ] Service [openvpn] closed (FD=10)
[ ] Service [openvpn] closed
Thanks.