I have a mental block sometimes when it comes to networking, so if anyone could please help me, I would greatly appreciate it. I'm sure I'm missing some secret setting that I know nothing about.
I'm trying to get pbr working where default traffic goes out the wan interface, but certain sites go out the vpn.
I'm running 23.05 on a Raspberry Pi4. Everything seems to be ok. I have an OpenVPN client working. It starts up and connects. It creates a tun0 device. I've tried following a few different guides for getting that working. I created a new interface named OpenVPN, unmanaged protocol on device tun0. (I can only post 1 screenshot ![]() )
)
As part of the openvpn config, I disabled the default route. I also have not set up the kill-switch yet. (Maybe that's what I'm missing but I didn't think it was required.)
I tried some things on the firewall page, even creating a new zone, but nothing seemed to help there so I have just the 2 "normal" zones.
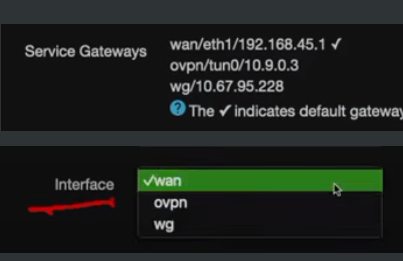
I'm trying to setup the pbr and am using the luci UI. On this page, I see my default route is indeed the wan, and the ovpn looks to be available and has an IP address (OpenVPN/tun0/10.x.x.x).
So, I jump to create a new policy, and this is my dilemma: the OpenVPN(tun0) interface is not an option:
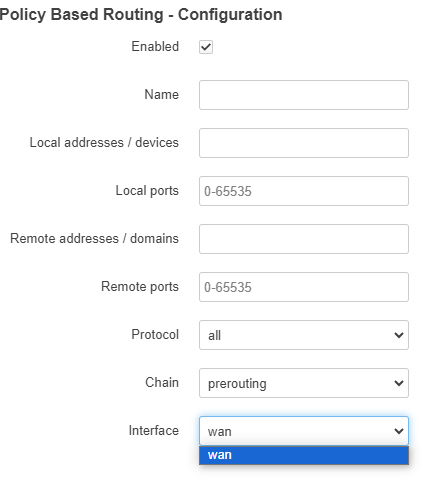
I have tried a lot of different things like adding the interface to the firewall, adding a new zone to the firewall, some settings in the interface itself related to the firewall, and maybe a few others that I can't remember. I'm pretty sure I've backed them all out and have a fairly clean config right now, but nothing gives me the option to select the vpn interface for a policy.
I'm pretty much out of ideas of where to look. I don't know enough about routing and nft to really figure this out. I have it working in dd-wrt but that device is slowly failing and I really want to drop dd-wrt and move to OpenWRT!
Any help is appreciated, and I can post more screenshots of pages if needed. Thanks!