I installed openNDS captive portal and it works as expected, with one exception:
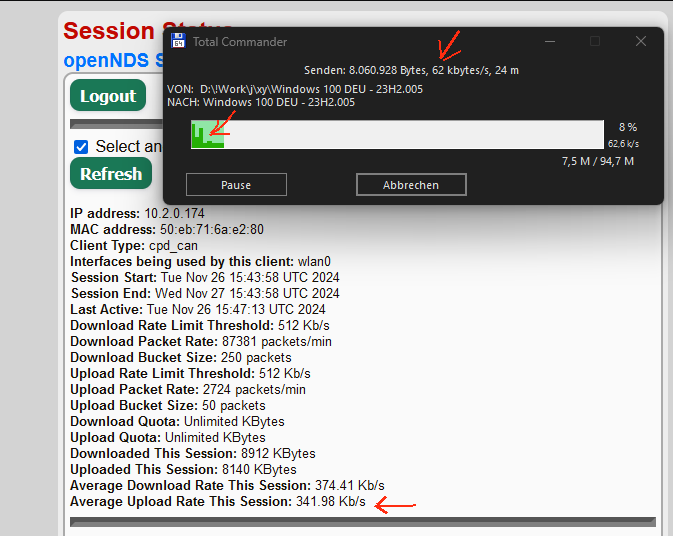
When limiting the upload rate (option uploadrate '512') clients still can upload up to the full speed of my internet connection. However, limiting the download rate (option downloadrate '512') works perfectly.
First I thought this could be due a conflict with other packages, so I set up Openwrt from the scratch using Openwrt 23.05.5 on a WRT3200ACM router, just installing minimum packages to run openNDS. But the issue is still there: Upload cannot be restricted, while download actually can be restricted by openNDS configuration.
Is anybody using openNDS with upload rate restrictions and can confirm that it is working? I would greatly appreciate advice what further information I could provide for anybody knowledgable and willing to help.
I only changed the following configuration options:
option gatewayinterface 'br-wifi_public'
option gatewayname 'Wifi Home'
option enable_serial_number_suffix '0'
option downloadrate '512'
option uploadrate '512'
This is the opennds startup logread output when using debuglevel 2, dnsmasq-full installed:
daemon.notice opennds[17897]: openNDS Version 10.3.0 is in startup
daemon.info opennds[17897]: openNDS Version 10.3.0 is in startup - Please wait....
daemon.notice opennds[17897]: The name of this gateway is Wifi Home
daemon.notice opennds[17897]: Attempting to Bind to interface: br-wifi_public
daemon.notice opennds[17897]: Interface br-wifi_public is up
daemon.notice opennds[17897]: Interface br-wifi_public is at 10.2.0.10 (6238e0bf1e01)
daemon.notice opennds[17897]: MHD version is 0.9.75
daemon.notice opennds[17897]: Number of Upstream gateway(s) [ 0 ]
daemon.notice opennds[17897]: Preemptive authentication is enabled
daemon.notice opennds[17897]: Created web server on 10.2.0.10:2050
daemon.notice opennds[17897]: Maximum Html Page size is [ 10240 ] Bytes
daemon.notice opennds[17897]: Socket access at /tmp/ndsctl.sock
daemon.notice opennds[17897]: Click to Continue option is Enabled.
daemon.notice opennds[17897]: Preauth is Enabled - Overriding FAS configuration.
daemon.notice opennds[17897]: sha256sum provider is available
daemon.err opennds[17897]: Error returned from system call - Continuing
daemon.notice opennds[17897]: Forwarding Authentication is Enabled.
daemon.notice opennds[17897]: Binauth is Enabled.
daemon.notice opennds[17897]: Externals flagged with debuglevel 1.
daemon.notice opennds[17897]: Initializing firewall rules
daemon.err opennds[17897]: Dnsmasq reload failed!
daemon.info opennds[17897]: list users_to_router is [ allow%20udp%20port%2053 allow%20udp%20port%2067 allow%20tcp%20port%2022 allow%20tcp%20port%20443 ]
daemon.info opennds[17897]: list preauthenticated_users is [ ]
daemon.info opennds[17897]: list authenticated_users is [ allow%20all ]
daemon.err opennds[17897]: Dnsmasq reload failed!
daemon.notice opennds[17897]: openNDS is now running.
This is the opennds startup logread output when using debuglevel 2, dnsmasq (standard, not full) installed:
daemon.notice opennds[23969]: openNDS Version 10.3.0 is in startup
daemon.info opennds[23969]: openNDS Version 10.3.0 is in startup - Please wait....
daemon.notice opennds[23969]: The name of this gateway is Wifi Home
daemon.notice opennds[23969]: Attempting to Bind to interface: br-wifi_public
daemon.notice opennds[23969]: Interface br-wifi_public is up
daemon.notice opennds[23969]: Interface br-wifi_public is at 10.2.0.10 (6238e0bf1e01)
daemon.notice opennds[23969]: MHD version is 0.9.75
daemon.notice opennds[23969]: Number of Upstream gateway(s) [ 0 ]
daemon.notice opennds[23969]: Preemptive authentication is enabled
daemon.notice opennds[23969]: Created web server on 10.2.0.10:2050
daemon.notice opennds[23969]: Maximum Html Page size is [ 10240 ] Bytes
daemon.notice opennds[23969]: Socket access at /tmp/ndsctl.sock
daemon.notice opennds[23969]: Click to Continue option is Enabled.
daemon.notice opennds[23969]: Preauth is Enabled - Overriding FAS configuration.
daemon.notice opennds[23969]: sha256sum provider is available
daemon.err opennds[23969]: Error returned from system call - Continuing
daemon.notice opennds[23969]: Forwarding Authentication is Enabled.
daemon.notice opennds[23969]: Binauth is Enabled.
daemon.notice opennds[23969]: Externals flagged with debuglevel 1.
daemon.notice opennds[23969]: Initializing firewall rules
daemon.err opennds[23969]: Dnsmasq reload failed!
daemon.info opennds[23969]: list users_to_router is [ allow%20udp%20port%2053 allow%20udp%20port%2067 allow%20tcp%20port%2022 allow%20tcp%20port%20443 ]
daemon.info opennds[23969]: list preauthenticated_users is [ ]
daemon.info opennds[23969]: list authenticated_users is [ allow%20all ]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq nftset complile option not available - Upgrade to dnsmasq-full version. Trying ipset option....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq ipset complile option not available -- Upgrade to dnsmasq-full version. Unable to configure walledgarden....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq nftset complile option not available - Upgrade to dnsmasq-full version. Trying ipset option....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq ipset complile option not available -- Upgrade to dnsmasq-full version. Unable to configure blocklist....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq nftset complile option not available - Upgrade to dnsmasq-full version. Trying ipset option....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq ipset complile option not available -- Upgrade to dnsmasq-full version. Unable to configure walledgarden....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq nftset complile option not available - Upgrade to dnsmasq-full version. Trying ipset option....]
daemon.warn opennds[23969]: libopennds - [Warning: dnsmasq ipset complile option not available -- Upgrade to dnsmasq-full version. Unable to configure blocklist....]
daemon.err opennds[23969]: Dnsmasq reload failed!
daemon.notice opennds[23969]: openNDS is now running.
daemon.err opennds[23969]: failure: /usr/lib/opennds/libopennds.sh "auth_restore" &
Any advice appreciated!