Hello again, According to this post it is possible to get one wireguard ssid and other normal ssid. I think some features or settings may have changed, because i was not able to find all of them as they said. I want to get that with LuCi the GUI openwrt interface. can please someone help me? thank you.
I am on openwrt stable build with wireguard installed which is working fine and two ssid also working fine but how do i set them?
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
ubus call system board
{
"kernel": "5.15.162",
"hostname": "OpenWrt",
"system": "MediaTek MT7628AN ver:1 eco:2",
"model": "Xiaomi MiWiFi 3C",
"board_name": "xiaomi,miwifi-3c",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.4",
"revision": "r24012-d8dd03c46f",
"target": "ramips/mt76x8",
"description": "OpenWrt 23.05.4 r24012-d8dd03c46f"
}
}
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix ':e852::/48'
config interface 'wan'
option device 'eth0.1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '10.0.0.1'
option netmask '255.0.0.0'
option ip6assign '60'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '2 4 6t'
config interface 'WireGuard_JP'
option proto 'wireguard'
option private_key 'wAXmO28D8XeWiHc+='
list addresses '10.2.0.2/32'
list dns '10.2.0.1'
config wireguard_WireGuard_JP
option description 'Imported peer configuration'
option public_key 'ZQ/KwfKaBt5q/='
list allowed_ips '0.0.0.0/0'
option endpoint_host ''
option endpoint_port '51820'
option route_allowed_ips '1'
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option channel '13'
option band '2g'
option htmode 'HT20'
option country ''
option cell_density '3'
option txpower '20'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wireless Freedom'
option encryption 'sae-mixed'
option key ''
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'ap'
option ssid 'Wireless Freedom WireGuard'
option encryption 'sae-mixed'
option key ''
option network 'lan'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
option flow_offloading '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'WireGuard_VPN'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'WireGuard_JP'
option masq '1'
config forwarding
option src 'lan'
option dest 'WireGuard_VPN'
Restore cell density to 1 - normal or 0-off, replace txpower with correct country code.
On the wired side of things you need to create routes from LAN-s with NAT in to wireguard, similar to current LAN->WAN route.
Okay i did.
but here i am not getting the original 22 dBm power on OpenWrt firmware stable version, i think i got that before. i even reset the router with official openwrt firmware and all default settings given by openwrt. country code = CH = CHINA.
Um, it's confused me, please rewrite.
CH i Switzerland, 20dBm max. You need CN.
Check luci/network/firewall first page how lan to wan is mapped, you need to add special zone with vpn interface, then forward wifi-guest-vlans to that interface zone.
You first need to make a guest wifi.
Both SSID's are now bridged to the lan interface
See: https://openwrt.org/docs/guide-user/network/wifi/guestwifi/configuration_webinterface
Then you need PBR to only route e.g. the guest wifi via Wireguard:
Sorry it really is CN = china. all though i did changed the country code to china - CN. which still not getting more than 20 dBm, i installed X-WRT just to check which gave me the 22 dBm more than openwrt. but i got 22 dBm before not now why? i'm right now on just basic default openwrt which still not giving me more than 20 dBm.
So i need to install PBR or just i have to set some things on openwrt firewall or interface? Also on Wireguard Vpn interface do i have to enable the Route Allowed IPs? otherwise it is not working for Wireguard SSID, and even i enable it i don't get any internet from normal SSID.
If you enable the route Allowed IPs then all LAN/wifi clients should use the WG tunnel.
If that is not working your WG setup might be wrong.
First check that out.
In the end you do not enable route allowed IPs but use Policy Based Routing, you do not need the full package but can do it manually basically create a routing table with default route via the WG interface and a routing rule to make the subnet (or interface) of the guest wifi use that routing table.
An example which I am using:
/etc/config/network
config route
option interface 'wg_mullv_se'
option table '102'
option target '0.0.0.0/0'
config rule
option src '192.168.30.0/24'
option lookup '102'
My WG interface is wg_mullv_se
I have created a routing table 102 with default route via that interface
The subnet 192.168.30.0/24 is the subnet of my guest interface which is now using this table 102 so is routed via the WG interface.
To make sure your guest wifi only use the WG tunnel you only forward from guest zone to vpn zone and not to wan zone.
Thank you, It is working now.
config route
option interface 'WireGuard_JP'
option target '0.0.0.0/0'
option table '102'
option source '192.168.3.1'
config rule
option src '192.168.3.1/24'
option lookup '102'
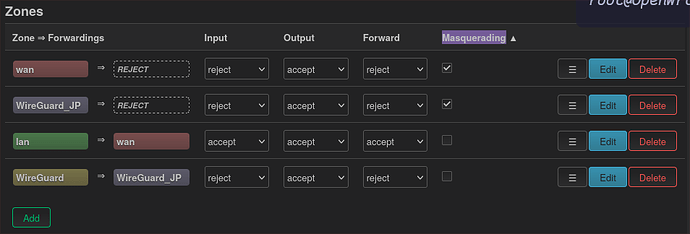
but i have a qus, on firewall do i need to enable Masquerading on last line which is WireGuard => Wireguard_JP?
It looks like you are setting up a WG tunnel to a commercial VPN provider.
I do not know what instructions you followed but these are pretty accurate:
of course there is our own wiki:
https://openwrt.org/docs/guide-user/services/vpn/wireguard/client
But yes you have to Masquerade because the commercial VPN provider does not know your return route and even if they did know it can collide with other users.
Um, I got stuck again. i enabled Masquerade tho, but now i am not getting any internet from the WireGuard SSID but telegram is working idk how, google and youtube and other sites are not working. this is not a problem with the Masquerade because i even turned off which gave the same results.
Please show the latest configs, redact passwords/keys etc:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
wg show
I am posting here the configs now.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fde8::/48'
config interface 'wan'
option device 'eth0.1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '2 4 6t'
config interface 'WireGuard'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'WireGuard_JP'
option proto 'wireguard'
option private_key '+='
list addresses '10.2.0.2/32'
list dns '10.2.0.1'
option mtu '1412'
config wireguard_WireGuard_JP
option description 'Imported peer configuration'
option public_key 'ZQ//='
list allowed_ips '0.0.0.0/0'
option endpoint_host '138.199.21.193'
option endpoint_port '51820'
config route
option interface 'WireGuard_JP'
option target '0.0.0.0/0'
option table '102'
config rule
option src '192.168.3.1/24'
option lookup '102'
/etc/config/network
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option channel '11'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wireless Freedom'
option encryption 'psk2'
option key '@'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'ap'
option ssid 'Wireless Freedom WireGuard'
option encryption 'psk2'
option key '@'
option network 'WireGuard'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'WireGuard'
option interface 'WireGuard'
option start '100'
option limit '150'
option leasetime '12h'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'WireGuard'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'WireGuard'
option masq '1'
config rule
option name 'WireGuard DNS'
option src 'WireGuard'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'WireGuard DHCP'
list proto 'udp'
option src 'WireGuard'
option dest_port '67'
option target 'ACCEPT'
config zone
option name 'WireGuard_JP'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'WireGuard_JP'
option masq '1'
config forwarding
option src 'WireGuard'
option dest 'WireGuard_JP'
wg show
interface: WireGuard_JP
public key: +M1XU=
private key: (hidden)
listening port: 55530
peer: ZQ//=
endpoint: 138.199.21.193:51820
allowed ips: 0.0.0.0/0
latest handshake: 1 minute, 49 seconds ago
transfer: 19.35 KiB received, 18.93 KiB sent
Add option mtu_fix '1'
The Masquerading is on the 'WireGuard_JP' zone no need to set it somewhere else so remove it here:
Reboot after changing
After reboot show output of:
ip route show
ip route show table 102
ip rule show
wg show
Your switch configuration looks wrong what happened here?:
Do you have normal internet via the lan ports and via the Wireless Freedom wifi?
default via 192.168.0.1 dev eth0.1 src 192.168.0.100
138.199.21.193 via 192.168.0.1 dev eth0.1
192.168.0.0/24 dev eth0.1 scope link src 192.168.0.100
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.3.0/24 dev phy0-ap1 scope link src 192.168.3.1
default dev WireGuard_JP scope link
0: from all lookup local
1: from 192.168.3.1/24 lookup 102
32766: from all lookup main
32767: from all lookup default
interface: WireGuard_JP
public key: +M1XU=
private key: (hidden)
listening port: 40533
peer: ZQ/=
endpoint: 138.199.21.193:51820
allowed ips: 0.0.0.0/0
Okay, listen, I do not think i have done anything to there yet it is just default what i got as far i know, If something is wrong please guide me to fix it.
I didn't understood what you said, but i got the internet connection from my uncle's router via a ethernt cable, and it is in lan right? also i have normal internet connection without vpn on wireless freedom SSID wifi.
It must be 192.168.3.0/24
config route
option interface 'WireGuard_JP'
option target '0.0.0.0/0'
option table '102'
config rule
option src '192.168.3.0/24'
option lookup '102'
Is this correct? It is not working, but somehow telegram and youtube are working. but the browser and browser's page are not.