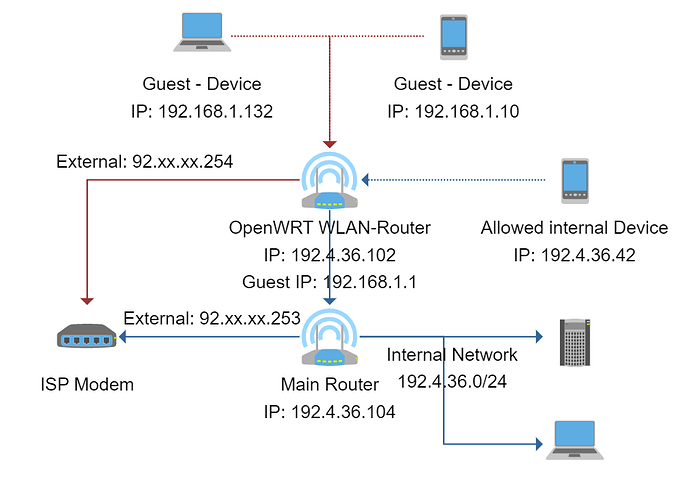
Hello everyone.
We got a TP-Link Archer C7 as our new Wireless Router and I wanted to span two different WIFI networks with it.
We have a main router, internal IP 192.4.36.104. This router manages all internal traffic als well as some IPsec routes to our Servers etc. So this router is our default gateway for all devices in our network.
Now I want to configure a new wireless router for our WIFI network as well as a guest WIFI network (dotted lines). The router needs to isolate the guest devices from our main network, but also needs to grant devices on the normal network access to our internal network as well as all other networks that our main router manages.
The normal network is working as intended. I can access all of our networks from the main WIFI.
The guest network however is not working.
I cannot get DHCP on the guest WIFI working again.
Guests, configured manually with a correct IP, cannot reach out from the router onwards.
Ping tells "target port unreachable"
I guess it has something to do with firewall settings.
Imgur album containing relevant screenshots
Interfaces:
Firewall zones:
Switch:
Now, does anyone know what I am doing wrong? Many things, I guess.
Thanks for the help!
It is not so easy to understand from the screenshots what is going in there, so could you post the configuration parts instead? You can wipe out any passwords, public IPs or MAC addresses.
uci show network;uci show wireless; \
uci show firewall; uci show dhcp; \
ip -4 addr ; ip -4 ro ; ip -4 ru; \
iptables-save; head -n -0 /etc/firewall.user; \
ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*
Please use "Preformatted text </>" for logs, scripts, configs and general console output.
I would have thought that you would want them the other way!
1 Like
mk24
July 9, 2019, 2:29pm
4
192.4.36 is not a private IP range. Use 192.168.X.0/24 with different X for your different networks.
If your OpenWrt router has a wired connection to the main router, you only need two networks in the OpenWrt router: lan and guest. lan is a static IP in the main router's lan range, or a DHCP client to get an IP from the main router. guest is a 192.168.X.1/24 with a DHCP server.
Forward from guest to lan with a simple config forwarding like the default one from lan to wan. This means you need to turn on masquerade and mss clamp on lan. Once that works, protect the lan with firewall rules so that guests can't access anything in the LAN, they only have the Internet.
@trendy of course, here you go:
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='REDACTED'
network.lan=interface
network.lan.type='bridge'
network.lan.proto='dhcp'
network.lan.clientid='root'
network.lan.ifname='eth0.1 eth0.2'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='static'
network.wan.ipaddr='192.4.36.102'
network.wan.netmask='255.255.255.0'
network.wan.gateway='192.4.36.104' // MAIN ROUTER
network.wan.broadcast='192.4.36.255'
network.wan.dns='192.4.36.104 9.9.9.9'
network.wan.metric='0'
network.wan_dev=device
network.wan_dev.name='eth0.2'
network.wan_dev.macaddr='REDACTED'
network.wan6=interface
network.wan6.ifname='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 4 5'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='0t 1'
network.@switch_vlan[1].vid='2'
network.@switch_vlan[2]=switch_vlan
network.@switch_vlan[2].device='switch0'
network.@switch_vlan[2].vlan='3'
network.@switch_vlan[2].ports='0t 2'
network.@switch_vlan[2].vid='1000'
network.WAN_Guest=interface
network.WAN_Guest.proto='static'
network.WAN_Guest.netmask='255.255.255.248'
network.WAN_Guest.gateway='REDACTED' // ISP GATEWAY
network.WAN_Guest.dns='REDACTED' //ISP DNS
network.WAN_Guest.ifname='eth0.1000'
network.WAN_Guest.metric='1000'
network.WAN_Guest.ipaddr='REDACTED' //EXTERNAL IP
network.LAN_Guest=interface
network.LAN_Guest.proto='static'
network.LAN_Guest.ipaddr='192.168.1.1'
network.LAN_Guest.netmask='255.255.255.0'
network.LAN_Guest.dns='192.168.1.1 9.9.9.9'
network.LAN_Guest.type='bridge'
network.LAN_Guest.ifname='eth0.1000 eth0.1001'
network.LAN_Guest.gateway='192.168.1.1'
network.@route[0]=route
network.@route[0].interface='LAN_Guest'
network.@route[0].target='0.0.0.0/0'
network.@route[0].gateway='REDACTED' // EXTERNAL IP
network.@switch_vlan[3]=switch_vlan
network.@switch_vlan[3].device='switch0'
network.@switch_vlan[3].vlan='4'
network.@switch_vlan[3].vid='1001'
network.@switch_vlan[3].ports='0t 3'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:00.0'
wireless.radio0.htmode='VHT80'
wireless.radio0.legacy_rates='1'
wireless.radio0.country='DE'
wireless.radio0.channel='auto'
wireless.radio0.txpower='20'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.mode='ap'
wireless.default_radio0.ssid='TP-AIR-1'
wireless.default_radio0.encryption='psk-mixed'
wireless.default_radio0.key='REDACTED'
wireless.default_radio0.network='lan'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.hwmode='11g'
wireless.radio1.path='platform/qca956x_wmac'
wireless.radio1.channel='auto'
wireless.radio1.htmode='HT40'
wireless.radio1.country='DE'
wireless.radio1.legacy_rates='1'
wireless.radio1.txpower='20'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.mode='ap'
wireless.default_radio1.network='lan'
wireless.default_radio1.ssid='TP-AIR-1-2.4'
wireless.default_radio1.encryption='psk-mixed'
wireless.default_radio1.key='REDACTED'
wireless.@wifi-iface[2]=wifi-iface
wireless.@wifi-iface[2].device='radio1'
wireless.@wifi-iface[2].mode='ap'
wireless.@wifi-iface[2].ssid='TP-Guest-2.4'
wireless.@wifi-iface[2].encryption='psk-mixed'
wireless.@wifi-iface[2].key='TebisGuest'
wireless.@wifi-iface[2].network='LAN_Guest'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].target='ACCEPT'
firewall.@rule[9].proto='udp'
firewall.@rule[9].dest_port='67-68'
firewall.@rule[9].name='Guest DHCP'
firewall.@rule[9].src='lan_guest'
firewall.@rule[10]=rule
firewall.@rule[10].target='ACCEPT'
firewall.@rule[10].proto='udp'
firewall.@rule[10].name='Guest DNS'
firewall.@rule[10].src='lan_guest'
firewall.@rule[10].dest_port='53'
firewall.@rule[11]=rule
firewall.@rule[11].target='ACCEPT'
firewall.@rule[11].src='lan_guest'
firewall.@rule[11].name='Guest Forward Out'
firewall.@rule[11].proto='all'
firewall.@rule[11].dest='wan_guest'
firewall.@rule[12]=rule
firewall.@rule[12].target='ACCEPT'
firewall.@rule[12].src='wan_guest'
firewall.@rule[12].name='Guest Forward In'
firewall.@rule[12].proto='all'
firewall.@rule[12].dest='lan_guest'
firewall.@rule[13]=rule
firewall.@rule[13].name='Deny Guest to Local'
firewall.@rule[13].src='lan_guest'
firewall.@rule[13].target='REJECT'
firewall.@rule[13].proto='all'
firewall.@rule[13].dest='lan'
firewall.@rule[14]=rule
firewall.@rule[14].name='Deny Guest to WAN'
firewall.@rule[14].proto='all'
firewall.@rule[14].src='lan_guest'
firewall.@rule[14].dest='wan'
firewall.@rule[14].target='REJECT'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].masq_dest='!192.4.36.102/24'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].network='wan wan6'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].name='lan_guest'
firewall.@zone[2].network='LAN_Guest'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[3]=zone
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].name='wan_guest'
firewall.@zone[3].masq='1'
firewall.@zone[3].mtu_fix='1'
firewall.@zone[3].network='WAN_Guest'
firewall.@zone[3].input='ACCEPT'
firewall.@zone[3].forward='ACCEPT'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='lan'
firewall.@forwarding[0].src='wan'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[1].src='lan'
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='SNAT'
firewall.@redirect[0].src='lan_guest'
firewall.@redirect[0].dest='wan_guest'
firewall.@redirect[0].proto='all'
firewall.@redirect[0].src_dip='REDACTED' // EXTERNAL IP
firewall.@redirect[0].name='Guest NAT'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].dest='wan_guest'
firewall.@forwarding[2].src='lan_guest'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].dest='lan_guest'
firewall.@forwarding[3].src='wan_guest'
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@dnsmasq[0].nonwildcard='1'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].interface='LAN_GUEST'
dhcp.@dnsmasq[0].notinterface='LAN' 'WAN'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
dhcp.LAN_Guest=dhcp
dhcp.LAN_Guest.interface='LAN_Guest'
dhcp.LAN_Guest.start='10'
dhcp.LAN_Guest.limit='230'
dhcp.LAN_Guest.force='1'
dhcp.LAN_Guest.leasetime='30m'
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
5: br-LAN_Guest: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-LAN_Guest
valid_lft forever preferred_lft forever
6: eth0.1000@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-LAN_Guest state UP qlen 1000
inet REDACTED.254/29 brd REDACTED.255 scope global eth0.1000 //EXTERNAL IP
valid_lft forever preferred_lft forever
10: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
inet 192.4.36.102/24 brd 192.4.36.255 scope global eth0.2
valid_lft forever preferred_lft forever
default via 192.4.36.104 dev eth0.2
default via REDACTED dev eth0.1000 metric 1000 // ISP GATEWAY
192.4.36.0/24 dev eth0.2 scope link src 192.4.36.102
REDACTED.248/29 dev eth0.1000 scope link metric 1000 // ISP NETWORK ID
192.168.1.0/24 dev br-LAN_Guest scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
# Generated by iptables-save v1.6.2 on Tue Jul 9 16:20:05 2019
*nat
:PREROUTING ACCEPT [18259:3295429]
:INPUT ACCEPT [200:34792]
:OUTPUT ACCEPT [1386:120002]
:POSTROUTING ACCEPT [1239:108894]
:postrouting_lan_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_guest_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_guest_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_guest_postrouting - [0:0]
:zone_lan_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_guest_postrouting - [0:0]
:zone_wan_guest_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i br-LAN_Guest -m comment --comment "!fw3" -j zone_lan_guest_prerouting
-A PREROUTING -i eth0.1000 -m comment --comment "!fw3" -j zone_wan_guest_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o br-LAN_Guest -m comment --comment "!fw3" -j zone_lan_guest_postrouting
-A POSTROUTING -o eth0.1000 -m comment --comment "!fw3" -j zone_wan_guest_postrouting
-A zone_lan_guest_postrouting -m comment --comment "!fw3: Custom lan_guest postrouting rule chain" -j postrouting_lan_guest_rule
-A zone_lan_guest_prerouting -m comment --comment "!fw3: Custom lan_guest prerouting rule chain" -j prerouting_lan_guest_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_guest_postrouting -m comment --comment "!fw3: Custom wan_guest postrouting rule chain" -j postrouting_wan_guest_rule
-A zone_wan_guest_postrouting -m comment --comment "!fw3: Guest NAT" -j SNAT --to-source REDACTED.254 // EXTERNAL IP
-A zone_wan_guest_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_guest_prerouting -m comment --comment "!fw3: Custom wan_guest prerouting rule chain" -j prerouting_wan_guest_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -d 192.4.36.0/24 -m comment --comment "!fw3" -j RETURN
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Jul 9 16:20:05 2019
# Generated by iptables-save v1.6.2 on Tue Jul 9 16:20:05 2019
*mangle
:PREROUTING ACCEPT [76715:10297415]
:INPUT ACCEPT [58655:7036742]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [50104:6669704]
:POSTROUTING ACCEPT [50104:6669704]
-A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o eth0.1000 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan_guest MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Jul 9 16:20:05 2019
# Generated by iptables-save v1.6.2 on Tue Jul 9 16:20:05 2019
*filter
:INPUT ACCEPT [73:8149]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_guest_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_guest_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_guest_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_guest_dest_ACCEPT - [0:0]
:zone_lan_guest_forward - [0:0]
:zone_lan_guest_input - [0:0]
:zone_lan_guest_output - [0:0]
:zone_lan_guest_src_ACCEPT - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_guest_dest_ACCEPT - [0:0]
:zone_wan_guest_forward - [0:0]
:zone_wan_guest_input - [0:0]
:zone_wan_guest_output - [0:0]
:zone_wan_guest_src_ACCEPT - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_ACCEPT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i br-LAN_Guest -m comment --comment "!fw3" -j zone_lan_guest_input
-A INPUT -i eth0.1000 -m comment --comment "!fw3" -j zone_wan_guest_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i br-LAN_Guest -m comment --comment "!fw3" -j zone_lan_guest_forward
-A FORWARD -i eth0.1000 -m comment --comment "!fw3" -j zone_wan_guest_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o br-LAN_Guest -m comment --comment "!fw3" -j zone_lan_guest_output
-A OUTPUT -o eth0.1000 -m comment --comment "!fw3" -j zone_wan_guest_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_guest_dest_ACCEPT -o br-LAN_Guest -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_guest_forward -m comment --comment "!fw3: Custom lan_guest forwarding rule chain" -j forwarding_lan_guest_rule
-A zone_lan_guest_forward -m comment --comment "!fw3: Guest Forward Out" -j zone_wan_guest_dest_ACCEPT
-A zone_lan_guest_forward -m comment --comment "!fw3: Deny Guest to Local" -j zone_lan_dest_REJECT
-A zone_lan_guest_forward -m comment --comment "!fw3: Deny Guest to WAN" -j zone_wan_dest_REJECT
-A zone_lan_guest_forward -m comment --comment "!fw3: Zone lan_guest to wan_guest forwarding policy" -j zone_wan_guest_dest_ACCEPT
-A zone_lan_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_guest_forward -m comment --comment "!fw3" -j zone_lan_guest_dest_ACCEPT
-A zone_lan_guest_input -m comment --comment "!fw3: Custom lan_guest input rule chain" -j input_lan_guest_rule
-A zone_lan_guest_input -p udp -m udp --dport 67:68 -m comment --comment "!fw3: Guest DHCP" -j ACCEPT
-A zone_lan_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Guest DNS" -j ACCEPT
-A zone_lan_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_guest_input -m comment --comment "!fw3" -j zone_lan_guest_src_ACCEPT
-A zone_lan_guest_output -m comment --comment "!fw3: Custom lan_guest output rule chain" -j output_lan_guest_rule
-A zone_lan_guest_output -m comment --comment "!fw3" -j zone_lan_guest_dest_ACCEPT
-A zone_lan_guest_src_ACCEPT -i br-LAN_Guest -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m comment --comment "!fw3: Zone wan to lan forwarding policy" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_guest_dest_ACCEPT -o eth0.1000 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_guest_dest_ACCEPT -o eth0.1000 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_guest_forward -m comment --comment "!fw3: Custom wan_guest forwarding rule chain" -j forwarding_wan_guest_rule
-A zone_wan_guest_forward -m comment --comment "!fw3: Guest Forward In" -j zone_lan_guest_dest_ACCEPT
-A zone_wan_guest_forward -m comment --comment "!fw3: Zone wan_guest to lan_guest forwarding policy" -j zone_lan_guest_dest_ACCEPT
-A zone_wan_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_guest_forward -m comment --comment "!fw3" -j zone_wan_guest_dest_ACCEPT
-A zone_wan_guest_input -m comment --comment "!fw3: Custom wan_guest input rule chain" -j input_wan_guest_rule
-A zone_wan_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_guest_input -m comment --comment "!fw3" -j zone_wan_guest_src_ACCEPT
-A zone_wan_guest_output -m comment --comment "!fw3: Custom wan_guest output rule chain" -j output_wan_guest_rule
-A zone_wan_guest_output -m comment --comment "!fw3" -j zone_wan_guest_dest_ACCEPT
-A zone_wan_guest_src_ACCEPT -i eth0.1000 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_ACCEPT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_ACCEPT -i eth0.2 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
COMMIT
# Completed on Tue Jul 9 16:20:05 2019
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
lrwxrwxrwx 1 root root 16 Jun 27 14:18 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jul 9 16:20 /tmp/resolv.conf
-rw-r--r-- 1 root root 194 Jul 9 15:16 /tmp/resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface LAN_Guest
nameserver 192.168.1.1
nameserver 9.9.9.9
# Interface wan
nameserver 192.4.36.104
nameserver 9.9.9.9
# Interface WAN_Guest
nameserver REDACTED // ISP DNS 1
nameserver REDACTED // ISP DNS 2
FYI this IPv6 is private, same as 192.168 in IPv4, so need to mask it.
This is wrong in all aspects. LAN is a bridge so basically you are bridging the LAN and the WAN.
Again here the same mistake.
You have here 2 options. Either you terminate the LAN and Guest networks on the OpenWrt or create bridged vlans and terminate them on the main router. As per my understanding the ISP modem doesn't have IP addresses in the LAN and is merely bridging the ADSL/VDSL/Fiber to the ethernet port of your main router.
1 Like