Hello! First, its amazing to see how responsive this community has been to all questions posted. I've been perusing this forum for the past couple of days trying to figure out how to setup VLAN. I did watch the videos by OneMarcFifty but haven't fully able to configure it correctly.
Device context:
Router: Netgear R7800
OpenWrt firmware: 23.05.1
Note: DSA is still not available for my router. Its still using swconfig
I'm trying to setup the usual 3 VLANs:
VLAN20 - Primary devices (phones, laptop etc)
VLAN30 - IOT
VLAN40 - Guest
- My primary devices have connected to the VLAN20 network (192.168.20.0/24)
- My IOT devices are on 2.4G, and have got the new IP address from VLAN30 network (192.168.30.0/24)
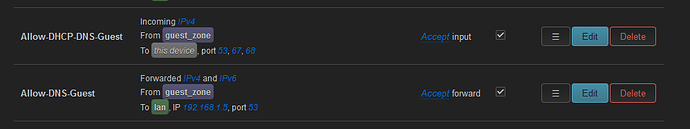
- However, I'm unable to connect to the guest network. I've added firewall rule to allow guest network to forward to WAN.
Here are the configs:
Network:
root@OpenWrt:/etc/config# cat network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ipv6 '0'
option delegate '0'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
option ipv6 '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
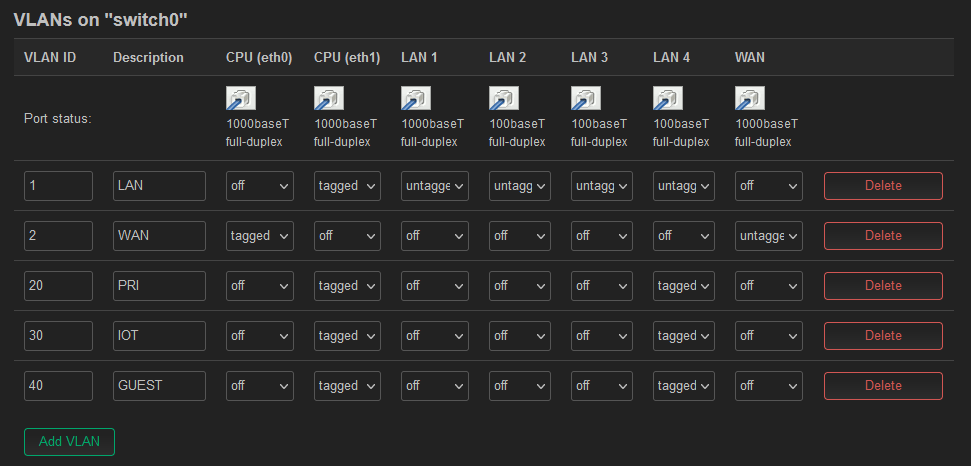
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
option vid '1'
option description 'LAN'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 5'
option vid '2'
option description 'WAN'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '20'
option ports '1t 6t'
option description 'PRI'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '30'
option ports '1t 6t'
option description 'IOT'
config switch_vlan
option device 'switch0'
option vlan '5'
option ports '1t 6t'
option vid '40'
option description 'GUEST'
config device
option type 'bridge'
option name 'br-pri'
list ports 'eth1.20'
option ipv6 '0'
config device
option type 'bridge'
option name 'br-iot'
list ports 'eth1.30'
option ipv6 '0'
config device
option type 'bridge'
option name 'br-guest'
list ports 'eth1.40'
option ipv6 '0'
config interface 'pri_interface'
option proto 'static'
option device 'br-pri'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
option delegate '0'
config interface 'iot_interface'
option proto 'static'
option device 'br-iot'
option ipaddr '192.168.30.1'
option netmask '255.255.255.0'
option delegate '0'
config interface 'guest_interface'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.40.1'
option netmask '255.255.255.0'
option delegate '0'
Firewall:
root@OpenWrt:/etc/config# cat firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
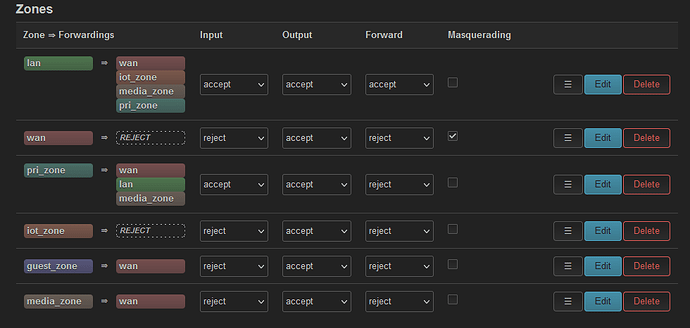
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'pri_zone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'pri_interface'
config zone
option name 'iot_zone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'iot_interface'
config zone
option name 'guest_zone'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest_interface'
config forwarding
option src 'pri_zone'
option dest 'iot_zone'
config forwarding
option src 'pri_zone'
option dest 'wan'
config forwarding
option src 'guest_zone'
option dest 'wan'
DHCP:
root@OpenWrt:/etc/config# cat dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,192.168.1.5,94.140.14.14,94.140.14.15,1.1.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'pri_interface'
option interface 'pri_interface'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,192.168.1.5,94.140.14.14,94.140.14.15,1.1.1.1'
config dhcp 'iot_interface'
option interface 'iot_interface'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,192.168.1.5,94.140.14.14,94.140.14.15,1.1.1.1'
config dhcp 'guest_interface'
option interface 'guest_interface'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,192.168.1.5,94.140.14.14,94.140.14.15,1.1.1.1'
Wireless:
root@OpenWrt:/etc/config# cat wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'soc/1b500000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-device 'radio1'
option type 'mac80211'
option path 'soc/1b700000.pci/pci0001:00/0001:00:00.0/0001:01:00.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'pri_interface'
option mode 'ap'
option ssid 'OpenWrt-5G'
option key 'REDACTED'
option encryption 'psk2'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'iot_interface'
option mode 'ap'
option ssid 'OpenWrt'
option key 'REDACTED'
option encryption 'psk2'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt Guest'
option encryption 'psk2'
option key 'REDACTED'
option network 'guest_interface'
Sorry this is such a long post