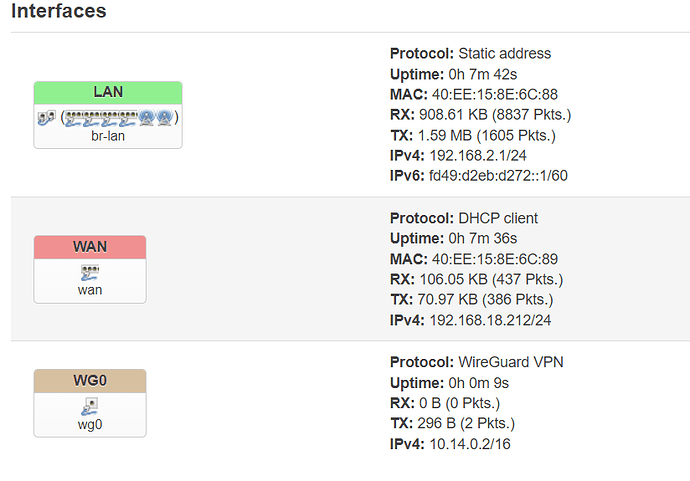
I have a setup where my OpenWrt router connects to an external WAN modem as a DHCP client and routes all the traffic to it through Wireguard VPN.
Recently (after changing the WAN connection) the VPN interface has 0 traffic through it (sometimes 0 changes to a few bytes). What is wrong?
/tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "5.10.146",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "TOTOLINK X5000R",
"board_name": "totolink,x5000r",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.2",
"revision": "r19803-9a599fee93",
"target": "ramips/mt7621",
"description": "OpenWrt 22.03.2 r19803-9a599fee93"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fd49:d2eb:d272::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wg0'
option proto 'wireguard'
list addresses '10.14.0.2/16'
option peerdns '0'
option mtu '1420'
list dns '162.252.172.57'
list dns '149.154.159.92'
option metric '10'
option private_key 'XXXXXX'
config wireguard_wg0
option description 'uslax'
option public_key 'm+L7BVQWDwU2TxjfspMRLkRctvmo7fOkd+eVk6KC5lM='
option endpoint_host 'us-lax.prod.surfshark.com'
option endpoint_port '51820'
option persistent_keepalive '25'
option route_allowed_ips '1'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option disabled '1'
config wireguard_wg0
option description 'plwaw'
option public_key 'vBa3HK7QXietG64rHRLm085VMS2cAX2paeAaphB/SEU='
option endpoint_host 'pl-waw.prod.surfshark.com'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
config interface 'wan'
option device 'wan'
option type 'bridge'
option proto 'dhcp'
option metric '20'
config wireguard_wg0
option description 'plgdn'
option endpoint_host 'pl-gdn.prod.surfshark.com'
option endpoint_port '51820'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option public_key '4lZhg/fKDCRLjvULGntx21qfebzQv5TJjZ1pc82sUgc='
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'DESKTOP-UILC81S'
option ip '192.168.1.240'
option mac '70:85:C2:00:6F:42'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'tun0'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'vpn'
head: /etc/firewall.user: No such file or directory
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
7: wan@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP q len 1000
inet 192.168.18.212/24 brd 192.168.18.255 scope global wan
valid_lft forever preferred_lft forever
10: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP ql en 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
17: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN ql en 1000
inet 10.14.0.2/16 brd 10.14.255.255 scope global wg0
valid_lft forever preferred_lft forever
default via 192.168.18.1 dev wan src 192.168.18.212 metric 20
5.187.49.187 via 192.168.18.1 dev wan metric 20
10.14.0.0/16 dev wg0 scope link metric 10
37.28.156.117 via 192.168.18.1 dev wan metric 20
45.134.212.231 via 192.168.18.1 dev wan metric 20
45.134.212.236 via 192.168.18.1 dev wan metric 20
45.134.212.248 via 192.168.18.1 dev wan metric 20
178.255.44.68 via 192.168.18.1 dev wan metric 20
192.168.2.0/24 dev br-lan scope link src 192.168.2.1
192.168.18.0/24 dev wan scope link metric 20
broadcast 10.14.0.0 dev wg0 table local scope link src 10.14.0.2
local 10.14.0.2 dev wg0 table local scope host src 10.14.0.2
broadcast 10.14.255.255 dev wg0 table local scope link src 10.14.0.2
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.2.0 dev br-lan table local scope link src 192.168.2.1
local 192.168.2.1 dev br-lan table local scope host src 192.168.2.1
broadcast 192.168.2.255 dev br-lan table local scope link src 192.168.2.1
broadcast 192.168.18.0 dev wan table local scope link src 192.168.18.212
local 192.168.18.212 dev wan table local scope host src 192.168.18.212
broadcast 192.168.18.255 dev wan table local scope link src 192.168.18.212
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Oct 14 22:44 /etc/resolv.conf -> /tm p/resolv.conf
-rw-r--r-- 1 root root 47 Jan 21 19:19 /tmp/resolv.conf
-rw-r--r-- 1 root root 108 Jan 22 17:02 /tmp/resolv.conf.d/reso lv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 108 Jan 22 17:02 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wg0
nameserver 162.252.172.57
nameserver 149.154.159.92
# Interface wan
nameserver 192.168.18.1