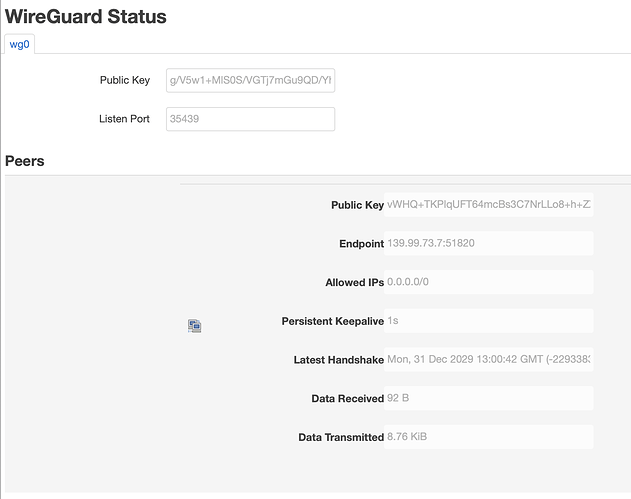
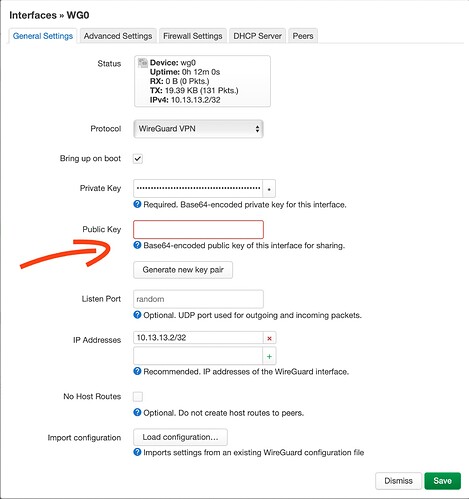
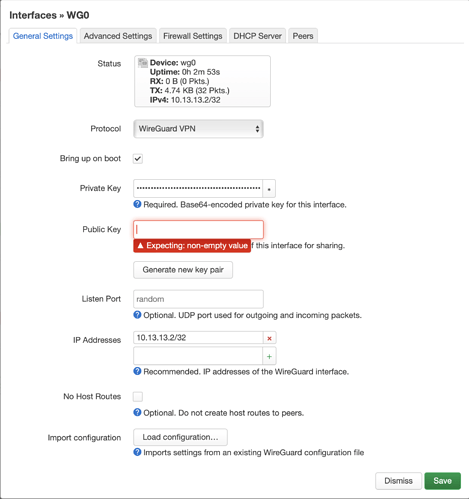
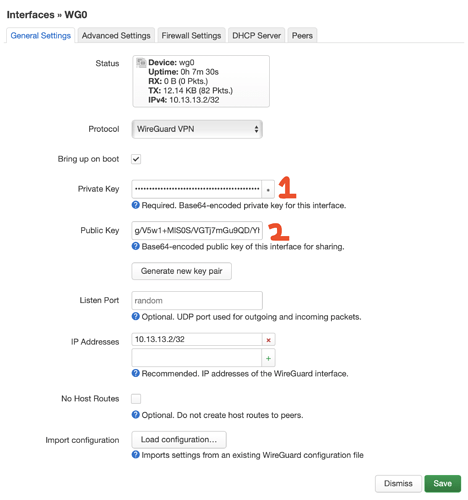
I'm trying to set up my router (TP-Link Archer C20) as a WireGuard client/peer, but no traffic is passing through. I have a WireGuard instance set up as a server on a VPS, which is what I am trying to connect to. I am using LuCI.
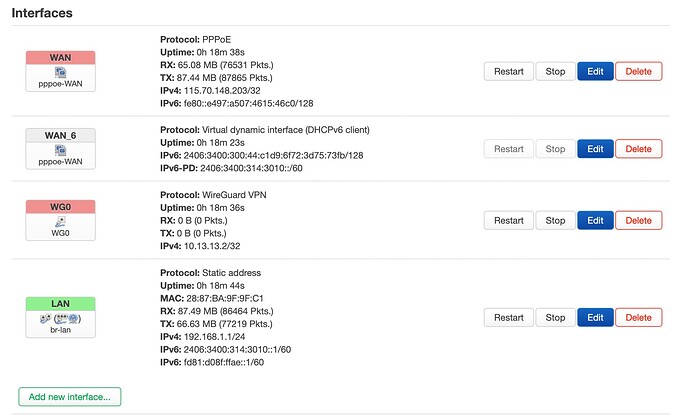
Here is an image of my interfaces:
To set up the WireGuard interface, I simply paste the peer config file from my server into the Import Configuration section on the General Settings tab of the WireGuard interface. This fills out all of the fields correctly as far as I can tell. Here is an example of the config file I am pasting in (the keys and IP addresses have been modified so nobody else uses my info):
[Interface]
Address = 10.13.13.2
PrivateKey = 6OBZ122eDdyCrC5CofGjgyix8Otl2o4ntybIBXOG+XI=
ListenPort = 51820
DNS = 1.1.1.1
[Peer]
PublicKey = vWHQ+TPRlqUFT64mtBs3C7NrLLo8+h+ZX6eCFDSH2n4=
PresharedKey = CkIHo7hdEmFVT2ZCFACTWG1e0tTypsid/9bCm3JLY+A=
Endpoint = 139.79.75.7:51820
AllowedIPs = 0.0.0.0/0
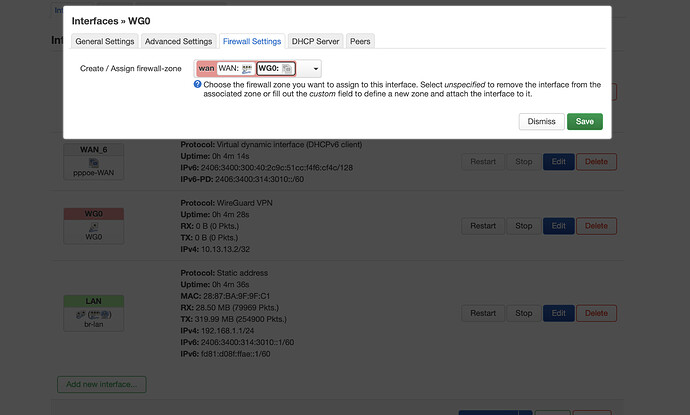
I have set the firewall zone for the WireGuard interface to WAN. I have also tried creating a new zone solely for the WireGuard interface with identical settings to the WAN interface and forwarding my LAN traffic into the new zone. Neither of these produce any effect.
I have tested the WireGuard config file with WireGuard on my laptop and on my phone, and both work fine. However I'm just having no luck at all on my router. I have spent hours and hours and hours on this and I know it's probably something simple I'm missing.
Some extra info:
- The router is brand new (I bought it yesterday)
- I've set the date & time correctly on the router and the VPS
- Apart from setting up my PPPoE interface and forwarding some ports I have made no changes in OpenWRT
- I can ping my VPS from my router
Output of /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd81:d08f:ffae::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr '28:87:ba:9f:9f:c2'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'WAN'
option proto 'pppoe'
option device 'eth0.2'
option username 'x'
option password 'x'
option ipv6 'auto'
option peerdns '0'
list dns '1.1.1.1'
list dns '9.9.9.9'
config interface 'WG0'
option proto 'wireguard'
option private_key 'x'
option listen_port '51820'
list addresses '10.13.13.2'
option peerdns '0'
list dns '1.1.1.1'
config wireguard_WG0
option description 'Imported peer configuration'
option public_key 'vWHQ+TPRlqUFT64mtBs3C7NrLLo8+h+ZX6eCFDSH2n4='
option preshared_key 'CkIHo7hdEmFVT2ZCFACTWG1e0tTypsid/9bCm3JLY+A='
list allowed_ips '0.0.0.0/0'
option endpoint_host '139.79.75.7'
option endpoint_port '51820'
Thank you in advance for any help or ideas.
Your interface should definition should not have a listen port. Try removing that and then see what happens.
If that doesn’t work, let’s see your firewall configuration and the output of wg show
1 Like
No luck removing the listen port.
Here is the output of wg show:
interface: WG0
public key: g/V5w1+MlS0S/VGTj7mGu9QD/Yh90dEv9A+xYFRTtnw=
private key: (hidden)
listening port: 50974
peer: vWHQ+TKPlqUFT64mcBs3C7NrLLo8+h+ZX6eCFDSH2n4=
preshared key: (hidden)
endpoint: 139.79.75.7:51820
allowed ips: 0.0.0.0/0
Here is the contents of /etc/config/firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'WAN'
list network 'WG0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'SSH'
list proto 'tcp'
option src 'wan'
option src_dport '22'
option dest_ip '192.168.1.4'
option dest_port '22'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'HTTPS'
list proto 'tcp'
option src 'wan'
option src_dport '443'
option dest_ip '192.168.1.4'
option dest_port '443'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'BitTorrent'
option src 'wan'
option src_dport '51413'
option dest_ip '192.168.1.4'
option dest_port '51413'
config forwarding
option src 'lan'
option dest 'wan'
Here are the firewall settings for the WireGuard interface:
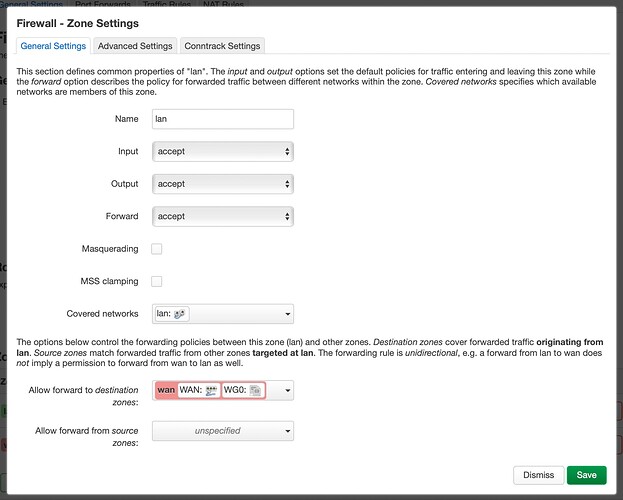
Here are the LAN firewall zone settings:
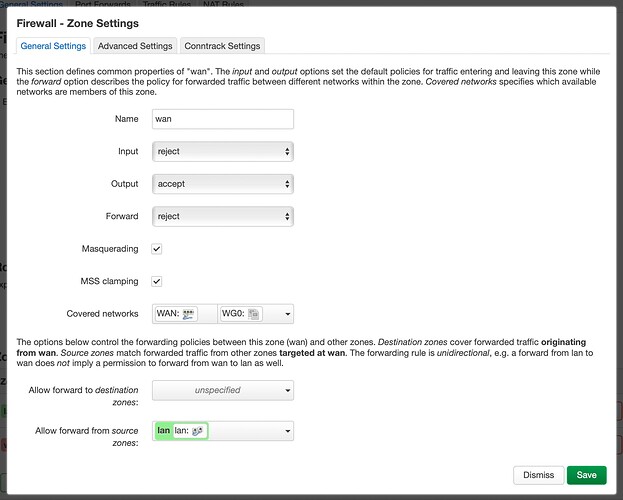
Here are the WAN firewall zone settings:
You are not getting a handshake. Check the keys - chances are that there is an error somewhere. In particular, the private key for the interface definition must be the same as the private key you were using in the config on the laptop or phone. And those systems must not be connected when you attempt to connect from your router.
1 Like
I don't understand how that's possible, as I'm importing a generated config file directly:
Thanks for helping anyway, I'll keep trying 
Have you restarted the router or at least the wg interface since you added the configuration?
1 Like
Yes I have.
I might be getting something confused with the keys, so I just thought explain the way I'm using them. This is my WireGuard directory on my server (which I'm trying to connect my router to).
.
├── coredns
│ └── Corefile
├── peer1
│ ├── peer1.conf
│ ├── peer1.png
│ ├── presharedkey-peer1
│ ├── privatekey-peer1
│ └── publickey-peer1
├── server
│ ├── privatekey-server
│ └── publickey-server
├── templates
│ ├── peer.conf
│ └── server.conf
└── wg0.conf
At the moment I'm using the contents of privatekey-server and publickey-server as the private and public keys in the WireGuard interface settings on my router.
I'm using presharedkey-peer1, privatekey-peer1, and publickey-peer1 in the peer configuration of my WireGuard interface on the router. Is that correct?
If the wireguard instance on your openwrt router is “peer 1”, you need the interface private key on openwrt to be the peer 1 private key. Then, you will populate the server public key in the openwrt peer configuration section as well as the peer 1 preshared key.
1 Like
Thank you. What about the interface public key on openwrt?
Holy jesus. I got a handshake after adding a Persistent Keep Alive. Except the date is 2029 
Check your time sync on both sides. But more importantly, is traffic flowing?
1 Like
No traffic flow. Time & date is good on both ends. Just to confirm my key setup:
.
├── peer1
│ ├── peer1.conf
│ ├── peer1.png
│ ├── presharedkey-peer1 [Peer Preshared Key]
│ ├── privatekey-peer1 [Interface Private Key]
│ └── publickey-peer1 [Interface Public Key]
├── server
│ ├── privatekey-server
│ └── publickey-server [Peer Public Key]
├── templates
│ ├── peer.conf
│ └── server.conf
└── wg0.conf
No. This needs to be in the peer config of the other side (the server).
1 Like
I know my server side peer config is fine, because I can connect to the WG server by using the peer1.conf generated by the server with my WireGuard desktop program or phone app.
Sorry for being stupid, but where do I get the key for this field?
Is it any of these files in my WireGuard directory on my server, or do I need to create it, or do I need to derive it from a private key?
.
├── coredns
│ └── Corefile
├── peer1
│ ├── peer1.conf
│ ├── peer1.png
│ ├── presharedkey-peer1
│ ├── privatekey-peer1
│ └── publickey-peer1
├── server
│ ├── privatekey-server
│ └── publickey-server
├── templates
│ ├── peer.conf
│ └── server.conf
└── wg0.conf
That should be auto generated by wireguard. For that to work, the private key must be right.
1 Like
The private key is right, but I'm not sure where I get the public key from, where is it auto-generated to?
I can't save the interface settings on openwrt without entering a public key.
Ok. So try entering it there (peer 1 public key) and see what happens.
1 Like
Ok, yeah that's what I have had it as the whole time. No handshake.
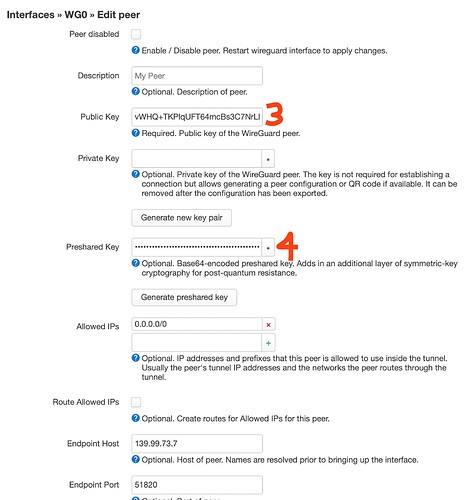
Here's where I have my keys in relation to everything that's autogenerated on my WG server:
WireGuard Server on VPS
.
├── coredns
│ └── Corefile
├── peer1
│ ├── peer1.conf
│ ├── peer1.png
│ ├── presharedkey-peer1 --> 4
│ ├── privatekey-peer1 --> 1
│ └── publickey-peer1 --> 2
├── server
│ ├── privatekey-server
│ └── publickey-server --> 3
├── templates
│ ├── peer.conf
│ └── server.conf
└── wg0.conf
I hope that makes sense.
Enable the route allowed ips option.
2 Likes
P Sherman, THANK YOU. OH MY GOD. That was exhausting. Sorry for being a n00b. You are a legend.