Hi,
I really hope someone can help me here.
HW: TP-Link TL-MR3420 v5
Firmware: OpenWrt 21.02.2 (same issue with OpenWrt 21.02.1)
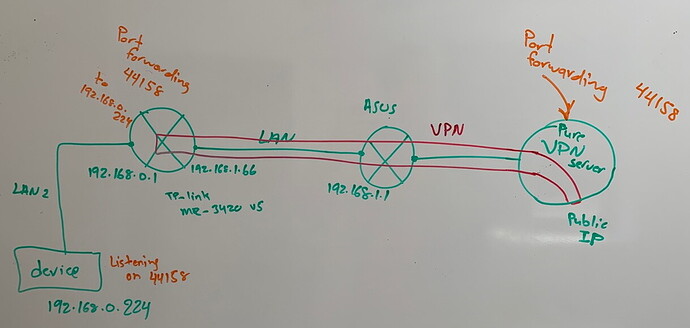
Network setup: please check below picture
I want to be able to reach my 44158 port from the public network, so I have a purevpn connection between my MR3420 router and the VPN server (through my other ASUS router).
I purchased and configured port forwarding in purevpn, and I can see it working when i connect from a pc to the vpn server and host a server on this port. But for some reason it is not working when I try to use the OpenWrt router.
The VPN connection works fine with OpenVPN in my router.
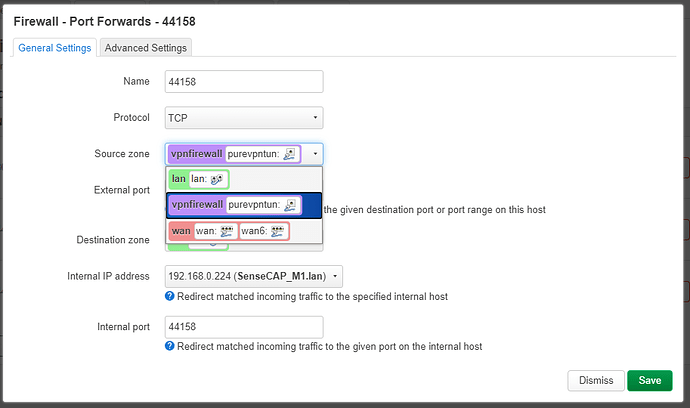
I configured port forwarding ... hopefully wrongly my I think now.
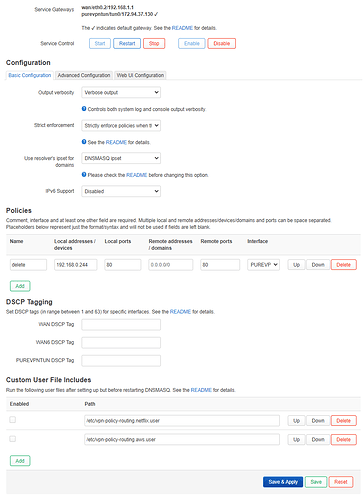
Here is my config:
network.loopback=interface
network.loopback.device='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='hidden'
network.@device[0]=device
network.@device[0].name='br-lan'
network.@device[0].type='bridge'
network.@device[0].ports='eth0.1'
network.lan=interface
network.lan.device='br-lan'
network.lan.proto='static'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ipaddr='192.168.0.1'
network.@device[1]=device
network.@device[1].name='eth0.2'
network.@device[1].macaddr='hidden'
network.wan=interface
network.wan.device='eth0.2'
network.wan.proto='dhcp'
network.wan6=interface
network.wan6.device='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='1 2 3 4 6t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='0 6t'
network.purevpntun=interface
network.purevpntun.proto='none'
network.purevpntun.device='tun0'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[2]=zone
firewall.@zone[2].name='vpnfirewall'
firewall.@zone[2].input='REJECT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].masq='1'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].network='purevpntun'
firewall.@zone[2].forward='ACCEPT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='lan'
firewall.@forwarding[1].dest='vpnfirewall'
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].name='80_vpn'
firewall.@redirect[0].src='vpnfirewall'
firewall.@redirect[0].src_dport='80'
firewall.@redirect[0].dest='lan'
firewall.@redirect[0].dest_ip='192.168.0.210'
firewall.@redirect[0].dest_port='80'
firewall.@redirect[1]=redirect
firewall.@redirect[1].target='DNAT'
firewall.@redirect[1].name='44158'
firewall.@redirect[1].proto='tcp'
firewall.@redirect[1].src='vpnfirewall'
firewall.@redirect[1].src_dport='44158'
firewall.@redirect[1].dest='lan'
firewall.@redirect[1].dest_port='44158'
firewall.@redirect[1].dest_ip='192.168.0.224'
firewall.@redirect[2]=redirect
firewall.@redirect[2].target='DNAT'
firewall.@redirect[2].name='44159'
firewall.@redirect[2].proto='tcp'
firewall.@redirect[2].src_dport='44159'
firewall.@redirect[2].dest='lan'
firewall.@redirect[2].dest_ip='192.168.0.224'
firewall.@redirect[2].dest_port='44159'
firewall.@redirect[2].src='vpnfirewall'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='vpnfirewall'
firewall.@forwarding[2].dest='lan'
Other Forwarding rules that was there already (not added by me)
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='false'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'