So basically i've tried to make WireGuard interface with another SSID wifi. Here is the old post, But now the problem is i can not connect to the internet when i tried on my phone. maybe a dns or dhcp issue, So how do i fix it?
without posting any config, you/we can't.
I think i should have posted the new logs here. Sorry for that.
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd44:3ba1:58b1::/48'
config interface 'wan'
option device 'eth0.1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '2 4 6t'
config interface 'WireGuard_JP'
option proto 'wireguard'
option private_key '+M0XAn0='
list addresses '10.2.0.2/32'
list dns '10.2.0.1'
option force_link '1'
config wireguard_WireGuard_JP
option description 'ProtonVPN WireGuard Japan'
option public_key '9Yy7/zeaFvKd/='
list allowed_ips '0.0.0.0/0'
option endpoint_host '149.88.103.48'
option endpoint_port '51820'
config route
option interface 'WF_WireGuard'
option target '0.0.0.0/0'
option table '102'
config rule
option src '192.168.5.0/24'
option lookup '102'
option in 'WireGuard_JP'
option out 'WF_WireGuard'
config interface 'WF_Guests'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'WF_WireGuard'
option proto 'static'
option ipaddr '192.168.5.1'
option netmask '255.255.255.0'
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option channel '13'
option band '2g'
option htmode 'HT20'
option country 'KR'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Wireless Freedom'
option encryption 'psk2'
option key '@'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'ap'
option ssid 'Wireless Freedom WireGuard'
option encryption 'psk2'
option key '@'
option network 'WF_WireGuard'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'Wireless Freedom Guests'
option encryption 'none'
option network 'WF_Guests'
option disabled '1'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'WF_WG'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'WF_WireGuard'
config rule
option name 'WireGuard DNS'
option src 'WF_WG'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'WireGuard DHCP'
list proto 'udp'
option src 'WF_WG'
option dest_port '67'
option target 'ACCEPT'
config zone
option name 'WG_JP'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'WireGuard_JP'
config forwarding
option src 'WF_WG'
option dest 'WG_JP'
config zone
option name 'WF_Guests'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'WF_Guests'
config forwarding
option src 'WF_Guests'
option dest 'wan'
config rule
option name 'WF_Guests DNS'
option src 'WF_Guests'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'WF_Guests DHCP'
list proto 'udp'
option src 'WF_Guests'
option dest_port '67'
option target 'ACCEPT'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'WF_Guests'
option interface 'WF_Guests'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'WF_WireGuard'
option interface 'WF_WireGuard'
option start '100'
option limit '150'
option leasetime '12h'
Even i did, No one is replying. OpenWRT Forum support is really bad NGL.
@Linux-DADDY
we're on the same boat, similar thread here
I might get another router, just for fun. for the sake of WireGuard access point
I'm not sure how everyone missed this thread, but I see it now. I don't have time to answer right now though.
There are some problems with your configuration in regard to mixing up the roles of the two networks (local users vs the wireguard tunnel). I will try to post a detailed reply later.
I guess we really are.
You can do it, but i think one OpenWRT router is able to do it, "If we set that up correctly."
Please make some time man, i am stuck at this same as @nitinjs .
Do it when you get free time, I will wait.
thank you for reply man, as no one was replying here for the info or fix.
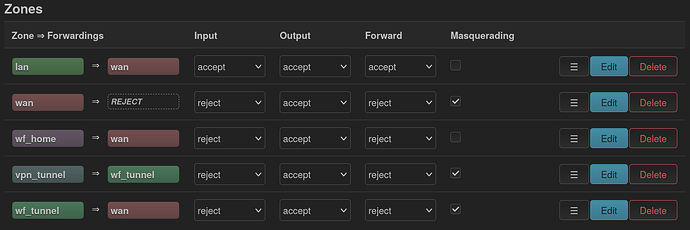
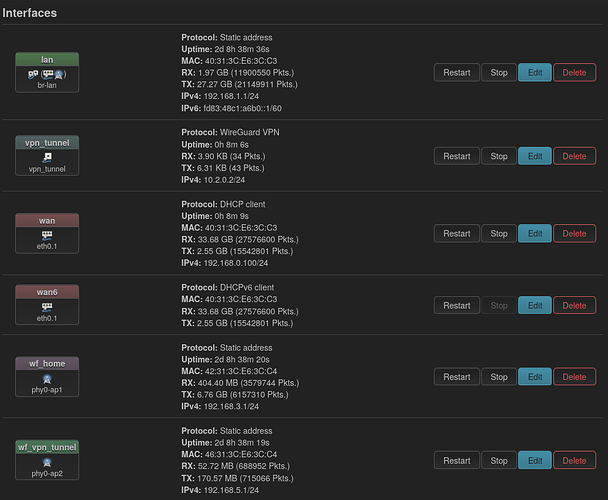
OK there's an interface for the wireguard tunnel which you have named WireGuard_JP and a local interface for wireguard users which you have named WF_WireGuard. This is ok though it would help to use simple descriptive names like vpntunnel and vpnusers respectively.
With that in mind, this is wrong:
in should be WF_WIreGuard, since this is where packets from the wifi users will come in to be considered for routing. Do not specify out, since the kernel doesn't know which interface the packet is going out on until the proper table has been consulted. (It assumes it will be wan). Actually I think you only need to specify src or in, though it won't break to use both as long as they are matching.
In the firewall, masq needs to be set on the outgoing zone not the incoming one. It's the same situation as masquerading on wan so your packets seem to come from the only IP the ISP knows you by, the one on WAN. The VPN service only knows you as 10.2.0.2, they can't handle packets with a source IP of 192.168.5.X.
Making this /24 is recommended, as that gives you an automatic route in the default table to 10.2.0.1. Then you can ping down the tunnel and most VPN servers are set up to answer pings.
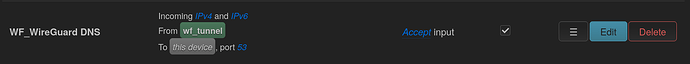
Do not do this here. A list dns on any interface does the same thing, it adds it to a global list that will be used in round-robin fashion. You want to use regular DNS only for the regular LAN and guests. VPN users may use a DNS that is reachable through the tunnel. Use a dhcp option 6 to advertise to WF_WireGuard users that they are to use 10.2.0.1 for DNS. You can back this up by blocking them from local DNS in the firewall (since that zone's default input policy is REJECT, remove the rule that allows input on port 53).
I think that is everything. Things to check if it still does not work:
- wifi clients should get a 192.168.5 DHCP address
- wg show should show that handshakes are occurring.
- From the router you should be able to ping down the tunnel (ping -I 10.2.0.2) to 10.2.0.1 and traceroute down the tunnel (I think that is a small i to force the source) to an Internet site.
Thank you for the detailed message but sorry i didn't understand some part of it.
but i have tried my best. check the config and pictures.
Now the configs.
** Network **
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd83:48c1:a6b0::/48'
config interface 'wan'
option device 'eth0.1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.1'
option proto 'dhcpv6'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '2 4 6t'
config interface 'wf_home'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'vpn_tunnel'
option proto 'wireguard'
option private_key 'sB77m5++='
list addresses '10.2.0.2/24'
list dns '10.2.0.1'
config wireguard_vpn_tunnel
option description 'ProtonVPN WireGuard Japan JP-FREE#301021'
option public_key '/='
list allowed_ips '0.0.0.0/0'
option endpoint_host '37.19.205.198'
option endpoint_port '51820'
config interface 'wf_vpn_tunnel'
option proto 'static'
option ipaddr '192.168.5.1'
option netmask '255.255.255.0'
config route
option interface 'wf_vpn_tunnel'
option target '0.0.0.0/0'
option table '102'
option source '192.168.5.1'
config rule
option in 'wf_vpn_tunnel'
option src '192.168.5.0/24'
option lookup '102'
** Firewall **
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
option flow_offloading '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wf_home'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wf_home'
config rule
config rule
option name 'WF_Home DHCP'
option src 'wf_home'
option dest_port '67'
option target 'ACCEPT'
list proto 'udp'
config rule
option name 'WF_Home DNS'
option src 'wf_home'
option dest_port '53'
option target 'ACCEPT'
config forwarding
option src 'wf_home'
option dest 'wan'
config zone
option name 'vpn_tunnel'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpn_tunnel'
option masq '1'
option mtu_fix '1'
config zone
option name 'wf_tunnel'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wf_vpn_tunnel'
option masq '1'
option mtu_fix '1'
config rule
option name 'WF_WireGuard DHCP'
list proto 'udp'
option src 'wf_tunnel'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'WF_WireGuard DNS'
option src 'wf_tunnel'
option dest_port '53'
option target 'ACCEPT'
option enabled '0'
config forwarding
option src 'vpn_tunnel'
option dest 'wf_tunnel'
config forwarding
option src 'wf_tunnel'
option dest 'wan'
If i don't set that, then i see no handshake from wireguard at all.
and yes (ping -I 10.2.0.2) to 10.2.0.1 this one is working.
Different VPN provider, but you'll get it working if you follow this closely:
How to use WireGuard VPN on your router
It's not as easy as OpenVPN, but it's doable.
Sorry, I do not think that will help. I think you misunderstood here, "I am trying to set the wireguard with another ssid, not just wireguard setup.", Anyways thank you.
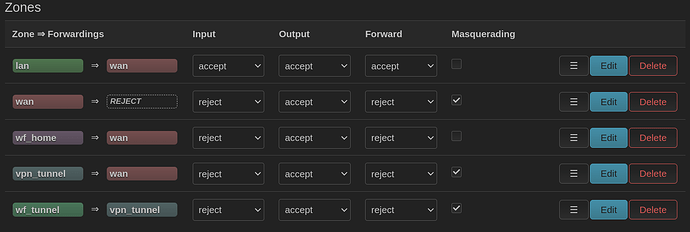
I see you have changed some names, but wf_vpn_tunnel is a confusing name. It should be called wf_vpn_user instead as it is the interface where the local users are. Then it becomes clear that the interface in the route to 0.0.0.0 in table 102 should be the actual tunnel to Japan, which you have named vpn_tunnel. Route tables are destination based, i.e. the kernel code consults the routing tables to answer the question "here a packet has come in over wifi, now where do I send it?"
Similarly your firewall config still does not allow forwarding from the local .5.0 users to the vpn tunnel, which of course is essential for this to work.
I had this turned off.
Now i enabled it, And i am getting internet tho but not from the wireguard, IP has not changed.
But bro what should i change? I am a really noob here, sorry, but please can you help me just tell what i change next?
And yes i got it, i have to change the firewall setting but which one?
In the firewall, allow forwarding from the zone you have named wf_tunnel to the one named vpn_tunnel. Forwarding in the other direction is not necessary. If you don't allow forwarding from wf_tunnel to wan, the VPN users won't be able to reach the Internet at all if the VPN is not working. This functionality (or lack thereof) is called "kill switch."
Not sure about the whole thing there, just noticed one thing you don't have is any route for the vpn host to go via the normal wan network.
e.g ?
config route
option interface 'wan'
option target '37.19.205.198/32'
option gateway '192.168.0.1'
Without something like this there's no way for the connection to happen, if you tell everything to go via the vpn, how do you actually get the connection going to the vpn server in the first place ? ![]()
Not sure what you're doing with this either
config route
option interface 'wf_vpn_tunnel'
option target '0.0.0.0/0'
option table '102'
option source '192.168.5.1'
Maybe you have a default route somewhere else getting added but it should be looking something like this ? :
config route
option interface 'vpn_tunnel'
option target '0.0.0.0/0'
option gateway '10.2.0.1/24'
I'm probably totally wrong though, my guess is you are trying to do some kind of source routing set up so you can route some clients via vpn and some clients without. In that case just disregard my post.
PBR package handles this well
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option drop_invalid '1'
option flow_offloading '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wf_home'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wf_home'
config rule
config rule
option name 'WF_Home DHCP'
option src 'wf_home'
option dest_port '67'
option target 'ACCEPT'
list proto 'udp'
config rule
option name 'WF_Home DNS'
option src 'wf_home'
option dest_port '53'
option target 'ACCEPT'
config forwarding
option src 'wf_home'
option dest 'wan'
config zone
option name 'vpn_tunnel'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpn_tunnel'
option masq '1'
option mtu_fix '1'
config zone
option name 'wf_tunnel'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wf_vpn_tunnel'
option masq '1'
option mtu_fix '1'
config rule
option name 'WF_WireGuard DHCP'
list proto 'udp'
option src 'wf_tunnel'
option dest_port '67'
option target 'ACCEPT'
config rule
option name 'WF_WireGuard DNS'
option src 'wf_tunnel'
option dest_port '53'
option target 'ACCEPT'
config forwarding
option src 'wf_tunnel'
option dest 'vpn_tunnel'
config forwarding
option src 'vpn_tunnel'
option dest 'wan'
Like this? Sorry if i am going all wrong again.
@wilsonyan Hey? I have changed now.
config interface 'wf_vpn_tunnel'
option proto 'static'
option ipaddr '192.168.5.1'
option netmask '255.255.255.0'
config route
option interface 'vpn_tunnel'
option target '0.0.0.0/0'
option source '10.2.0.1/24'
config rule
option in 'vpn_tunnel'
option src '10.2.0.2/24'
option lookup '102'
Does this looks good to you?
There are still several minor problems, but the one above is major and will prevent it from working. option in would be the interface of your VPNd wifi users, which is wf_vpn_tunnel. option src needs to be those users' IPs, which are 192.168.5.0/24, or preferably just remove option src. As you have it configured now, this rule will never match packets from the .5.0 users, so table 102 will never be used and all traffic will attempt to go by the default routing table, which is the regular wan.
Someone else mentioned that the pbr package is designed for this use case to simply set up multiple routing tables. I would recommend that, especially if you anticipate more complex conditional routing once this initial setup is working.
Minor problems I see are masq should not be set on the wf_tunnel firewall zone, and forwarding should not be allowed from vpn_tunnel to wan or anywhere else, since no connection attempts should ever be coming toward you from the VPN service.
Yeah i've used source routing in the past and it works but these days i'd just use two separate devices or two containers.