I followed the youtube guide below and configured a VPN for my use. I can connect to the VPN from my phone and ping the LAN devices.
OpenWRT - How to VPN into your Home network from anywhere using OpenVPN | Roadwarrior - YouTube
But, I am unable to browse internet when I am on this VPN. I want route my traffic through the VPN when I am connected to it.
Consider me a noob and I have tried everything I can think of to make it work, but failed at the end.
any ideas, directions would be highly appreciated,
A few things...
-
We recommend following the tutorials on OpenWrt's wiki. These are vetted and known to be working in the vast majority of cases. Here is the OpenVPN wiki.
-
Unless you have a specific need to use OpenVPN, I'd highly recommend that you consider WireGuard. It is easier to configure and much more performant. You want the Road Warrior configuration.
-
If you want help with respect to your current configuration, you will need to post the relvant info -- we cannot read minds, so we need to see the actual config to understand what might be wrong.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/openvpn
cat /etc/config/firewall
Also useful is the log information from both sides (server and client), and the client configuration files.
1 Like
Thank you so much for your advise. No wonder why I call myself a noob.
First of all, my requirement here is to be able to VPN into my home network from across the world. I tried but I couldn't find a way to do it with WireGuard. as far as I understood, WG connects me to a 3rd party VPN service.
here are the config files you asked for.
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fdb4:a04a:ca37::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option delegate '0'
list dns '192.168.2.1'
option dns_metric '0'
config interface 'SLT'
option proto 'static'
option device 'wan'
option netmask '255.255.255.0'
option delegate '0'
option metric '10'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns '94.140.14.49'
list dns '94.140.14.59'
option dns_metric '1'
config interface 'DIALOG'
option proto 'static'
option device 'lan2'
option ipaddr '192.168.8.2'
option netmask '255.255.255.0'
option gateway '192.168.8.1'
option delegate '0'
list dns '94.140.14.14'
list dns '94.140.15.15'
option dns_metric '2'
cat /etc/config/openvpn
config openvpn 'RoadWarrior'
option proto 'tcp-server'
option cipher 'AES-256-GCM'
option client_to_client '1'
option comp_lzo 'no'
option dev 'tun_roadwarrior'
option duplicate_cn '1'
option enabled '1'
option keepalive '10 120'
option mode 'server'
option mssfix '1450'
option persist_key '1'
option persist_tun '1'
option port '7500'
option remote_cert_tls 'client'
option reneg_sec '0'
option server '10.100.0.0 255.255.255.0'
option topology 'subnet'
option verb '3'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/Server_SiteA.crt'
option dh '/etc/openvpn/dh.pem'
option key '/etc/openvpn/Server_SiteA.key'
list push 'redirect-gateway def1'
list push 'route 192.168.2.0 255.255.255.0'
list push 'redirect-gateway def1'
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list device 'tun_roadwarrior'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'SLT'
list network 'DIALOG'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option target 'ACCEPT'
option name 'OpenVPN'
option dest_port '7500'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'openvpn_external'
option src 'wan'
option src_dport '7500'
option dest_ip '192.168.2.1'
option dest_port '7500'
option src_ip '192.168.1.1'
option src_port '7500'
option src_dip '192.168.1.2'
config forwarding
option src 'lan'
option dest 'wan'
Client Config file
client
dev tun_roadwarrior
remote test.ddns.net 7500
auth-nocache
cipher AES-256-GCM
comp-lzo no
connect-retry 5 60
keepalive 10 120
mssfix 1450
nobind
persist-key
persist-tun
proto tcp
pull
remote-cert-tls server
reneg-sec 0
verb 3
# Uncomment below to force Internet traffic over VPN, instead of just accessing devices.
redirect-gateway def1
<ca>
</ca>
<cert>
</cert>
<key>
</key>
This is incorrect. WG is a peer-to-peer VPN where you can connect directly to your home from your devices while you travel (road-warrior). It can be used in other configurations (such as via a 3rd party), but that's not common.
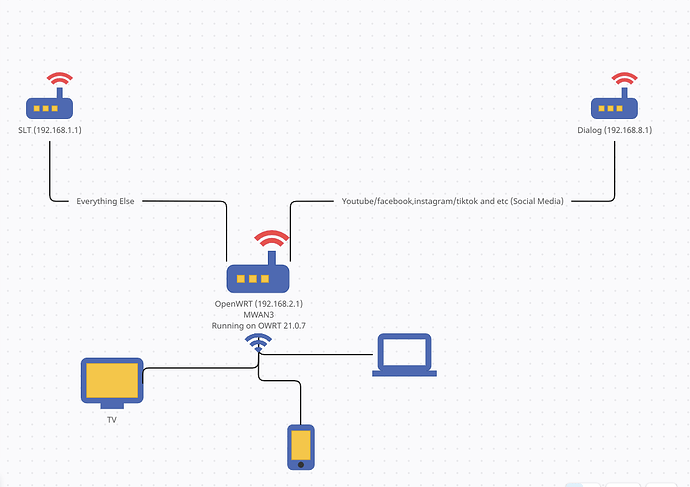
Quite honestly, you have a lot going on here that is not standard... can you describe your situation.
- this seems like it is not the main router in your network... you presumably have an upstream router at 192.168.1.1. Is that correct
- what is the DIALOG network for? It seems like it's not likely configured properly, unless it is connecting to another router (that is also a gateway) at 192.168.8.1?
Can you show a quick diagram of your network topology so that we can understand how all of these networks and devices are connected?
So I understood WG incorrect 
If you could point me in the direction to setup P2P VPN with wireguard, please.
Yes you are correct, my OpenWRT sits behind another ISP router. 192.168.1.1 is my Fibre link.
and then I have another ISP router 192.168.8.1 which i use to route only specific traffic(social media stuff to be specific). I do this using MWAN3
for example, if I access Microsoft.com, the traffic will route through 192.168.1.1
if I access youtube.com the traffic will route through 192.168.8.1
My goal was to make the VPN work only through my Fibre link(192.168.1.1).
see if this diagram makes sense.
I would recommend using WG for this -- I think it will be much more straight forward.
My recommendation would be to delete all things OpenWrt (including the network interface, the server config, and the fireawll rules. Then configure WireGuard and we'll go from there.
1 Like
Thank you. I removed everything I did under openvpn and installed WG.
Did some wg setup. But i am stuck at the same issue. No internet. I am missing something and I can't see what it is 
Ok... let's see your latest configuration.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:

Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
wg show
Sure, here we go
ubus call system board
"kernel": "5.4.238",
"hostname": "OpenWRTX4AG",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "Xiaomi Mi Router 4A Gigabit Edition",
"board_name": "xiaomi,mi-router-4a-gigabit",
"release": {
"distribution": "OpenWrt",
"version": "21.02.7",
"revision": "r16847-f8282da11e",
"target": "ramips/mt7621",
"description": "OpenWrt 21.02.7 r16847-f8282da11e"
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fdb4:a04a:ca37::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option delegate '0'
list dns '192.168.2.1'
option dns_metric '0'
config interface 'SLT'
option proto 'static'
option device 'wan'
option netmask '255.255.255.0'
option delegate '0'
option metric '10'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns 'x.x.x.x'
list dns x.x.x.x'
option dns_metric '1'
config interface 'DIALOG'
option proto 'static'
option device 'lan2'
option ipaddr '192.168.8.2'
option netmask '255.255.255.0'
option gateway '192.168.8.1'
option delegate '0'
list dns 'x.x.x.x'
list dns 'x.x.x.x'
option dns_metric '2'
config interface 'VPN'
option proto 'wireguard'
option peerdns '0'
option delegate '0'
option listen_port '1234'
option private_key 'xxxxxxxxxxxxxxxx'
list addresses '192.168.10.5/24'
list dns '8.8.8.8'
list dns '1.1.1.1'
config wireguard_VPN
option description 'MalithW'
option public_key 'xxxxxxxxxxxxxxx'
option route_allowed_ips '1'
option persistent_keepalive '25'
cat /etc/config/firewall
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fdb4:a04a:ca37::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option delegate '0'
list dns '192.168.2.1'
option dns_metric '0'
config interface 'SLT'
option proto 'static'
option device 'wan'
option netmask '255.255.255.0'
option delegate '0'
option metric '10'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns 'x.x.x.x'
list dns 'x.x.x.x'
option dns_metric '1'
config interface 'DIALOG'
option proto 'static'
option device 'lan2'
option ipaddr '192.168.8.2'
option netmask '255.255.255.0'
option gateway '192.168.8.1'
option delegate '0'
list dns 'x.x.x.x'
list dns 'x.x.x.x'
option dns_metric '2'
config interface 'VPN'
option proto 'wireguard'
option peerdns '0'
option delegate '0'
option listen_port '1234'
option private_key 'xxxxxxxxxxxxxxxxxxxxxxx'
list addresses '192.168.10.5/24'
list dns '8.8.8.8'
list dns '1.1.1.1'
config wireguard_VPN
option description 'MalithW'
option public_key 'xxxxxxxxxxxxxxxxxxxxxx'
option route_allowed_ips '1'
option persistent_keepalive '25'
root@OpenWRTX4AG:~# ^C
root@OpenWRTX4AG:~# clear
root@OpenWRTX4AG:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'tun_roadwarrior'
list network 'lan'
list network 'VPN'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'SLT'
list network 'DIALOG'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config forwarding
option src 'lan'
option dest 'wan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WireGuard'
list proto 'udp'
option src 'wan'
option dest_ip '192.168.2.1'
option src_dport '1234'
option dest_port '1234'
config rule
option name 'WireGuard'
list proto 'udp'
option src 'wan'
option src_port '1234'
option dest 'lan'
list dest_ip '192.168.2.1'
option dest_port '1234'
option target 'ACCEPT'
wg show
interface: VPN
public key: xxxxxxxxxxxxxxxxxx
private key: (hidden)
listening port: 1234
peer: xxxxxxxxxxxxxxxxxxxxxxxx
allowed ips: (none)
persistent keepalive: every 25 seconds
So it looks like you're not getting a handshake... we'll get to that in a moment.
First... to clean some things up....
remove the dns related lines here (they don't do anything), as well as the delegate option.
likewise, remove the dns entries and delegate options on the wg interface:
You need an allowed_ips line in the peer config on the router...
list allowed_ips '192.168.5.0/24'
config wireguard_VPN
option description 'MalithW'
option public_key 'xxxxxxxxxxxxxxxxxxxxxx'
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '192.168.10.2/32'
remove this (for now... we can revisit later)
Delete this (it's wrong... we'll add below):
Instead, it should look like this:
config rule
option name 'WireGuard'
option src 'wan'
option dest_port '1234'
option target 'ACCEPT'
list proto 'udp'
Let's also see the config from the remote peer (your phone or laptop or whatever).
Very bad idea. Start from OpenVPN.
BTW, suggesting WG instead of OpenVPN is OK, I do not see any comments?
Please ignore the comment above... WG will be a better and more performant solution for your needs.
2 Likes