Hello!
This is my first post in this forum, I hope it ends up where it belongs.
First of all: I am a beginner as far as network is concerned. So far network for me has been port shares in the Fritz!Box and not much else. Please bear with me.
Now to my problem:
I installed OpenWRT on a Fritz!Box 4040 I had lying around. The Fritz!Box, as I understand it, has a built in managed switch where I can assign VLANS to the various ports. This works fine. Depending on the LAN port and the corresponding settings, I end up in the main LAN or IOT LAN. So far so good. But if I want to put the Fritz!Box for internet access behind my "main" Fritz!Box, the WAN interface gets only an IP assigned and therefore access to the internet, if the VLAN-functionality is disabled. What could be the reason for this?
Hey Erik,
First things first:
- We cant guess what you have for Switch or DSA on your OpenWrt without your version.
- You'll have to provide the details necessary for the members to assist
- Start by running ssh into your OpenWrt device and execute the following command and then copy/paste it into a preformatted text box.
ubus call system board
Once the community sees your version, someone may be interested in asking for more information on your:
uci export dhcp; uci export network; uci export firewall
ubus call system board
returns
{
"kernel": "5.4.188",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 5 (v7l)",
"model": "AVM FRITZ!Box 4040",
"board_name": "avm,fritzbox-4040",
"release": {
"distribution": "OpenWrt",
"version": "21.02.3",
"revision": "r16554-1d4dea6d4f",
"target": "ipq40xx/generic",
"description": "OpenWrt 21.02.3 r16554-1d4dea6d4f"
}
}
uci export dhcp; uci export network; uci export firewall
returns
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'VLAN2'
option interface 'VLAN2'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdfd:2332:2c40::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0t 3'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '0t 4'
option vid '4'
config interface 'VLAN2'
option proto 'static'
option device 'eth0.2'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'VLAN2'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
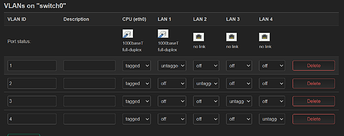
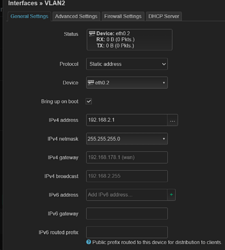
I will describe the steps I did to configure the VLANS.
I started by configuring the router internal switch
Then I created a new interface for vlan2
[image in reply to this message as I can only send one image per message]
VLAN2 Firewall unspecified
DHCP Server created, I didn't change anything
The at LAN2 connected devices get a 192.168.2.x IP-address as expected. However, I dont have access to the internet anymore. Neither with the default-LAN nor VLAN2 after applying the default lan firewall zone to it.
I'm a certified dummy when it comes to VLAN. So let me take the abuse I deserver right now.
...if the setting quoted above is to ignore dhcp from the wan's uplink, would it not follow that your lan and vlans can't see next hop out?
Please correct and help @9871741 solve this and in turn make me a better vlan student.
After enabling VLAN, you need to change eth0 to eth0.1
That part is correct, you mustn't run a dhcp-server on WAN. VLANs on ipq40xx is a bit tricky, as the hardware and its swconfig driver are very quirky, with a couple of nonsensical constraints; a PR migrating this to DSA is pending, fixing this once and for all.
VLANs on ipq40xx is a bit tricky
Thanks for trying to teach me.. but vlan'ing and DSA are Greek/Latin to me:
No offense meant to @trendy or @pavelgl ..
I'll just be the greeter/fluffer..
I performed a reset. After that I have tried to reproduce the problem. I just pinged google.com via the openwrt shell and changed VLAN settings. The problem occurs as soon as I create a new VLAN and set the CPU(eth0) as untagged or tagged. As soon as I click save and apply, the pinging fails.
Try including port 5 (wan) in the VLAN setup as described here.
I might be completely wrong but is that even related to my problem? I want to use the WAN port as an input from another router. My problem is enabling VLANS on the LAN ports.
I was actually going to ask if you have an upstream router -- what is the subnet on that router's LAN?
If it is 192.168.1.0/24 or 192.168.2.0/24, you have created a conflict. You need to make sure that you do not have the same subnet on the downstream router, so change one or the other.
its a Fritz!Box 4060. Subnet is 192.168.178.0/24. The problem occures as soon as i add a vlan and set CPU(eth0) to (un)tagged even if there is no Interface with a subnet created.
This fixed my problem:
Jeff, I think our definitions of "straightforward" are quite differentand you're way ahead of me. Intent is: two internal firewall zones "lan" and "guest" "lan" firewall zone includes 3 ports of the switch and the "home" SSID on both wifi bands "guest" zone includes 1 port and the "guest" SSID traffic is allowed from guest to wan, from lan to guest but not from guest to lan This way I can segregate a fussy wired client in the guest segment when needed. I gave your settings a…
I edited my network config to this:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd33:a93b:4b37::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option stp '1'
option device 'br-lan'
option ipaddr '192.168.1.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '101'
option vid '101'
option ports '0t 1'
option description 'LAN'
config switch_vlan
option device 'switch0'
option vlan '102'
option vid '102'
option ports '0t 2 3t'
option description 'IOT'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option stp '1'
option device 'br-guest'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.101'
config device
option name 'br-guest'
option type 'bridge'
list ports 'eth0.103'
config switch_vlan
option device 'switch0'
option vlan '103'
option ports '0t 4'
option vid '103'
option description 'GUEST'
config device
option type 'bridge'
option name 'br-iot'
list ports 'eth0.102'
config interface 'IOT'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option device 'br-iot'
do you see any possibilities for improvement?
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.