I'm running nlbwmon (2020-04-11.1-34a18876-3) under OpenWrt 21.02.0.
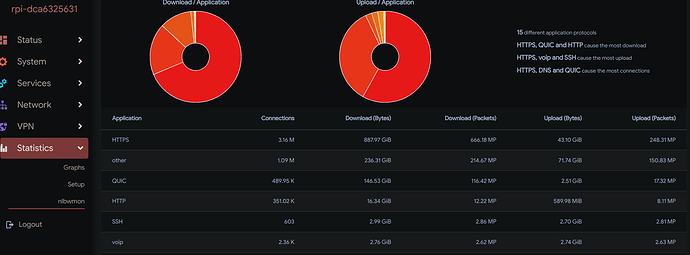
After adding some more triples (IP protocol, port number, name of the mapped protocol) under Configuration/Protocol-Mapping I get a more detailed list under Display/Apllication-Protocols.
BUT: I'm not able to catch VoIP traffic.
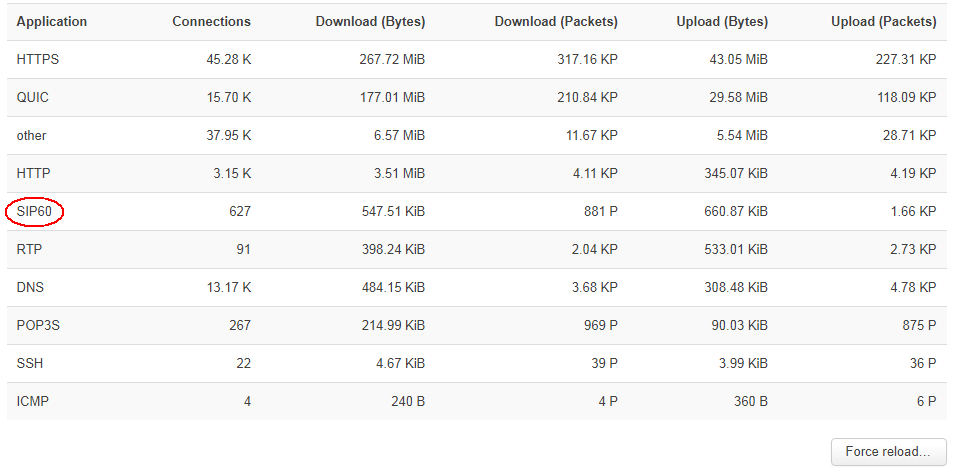
I've added the following triple for the SIP traffic:
6 5060 SIP
17 5060 SIP
and it appears in the display list.
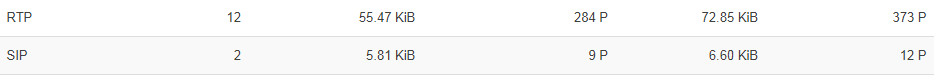
I've added furthermore the following triples for the RTP traffic:
6 40040 RTP
17 40040 RTP
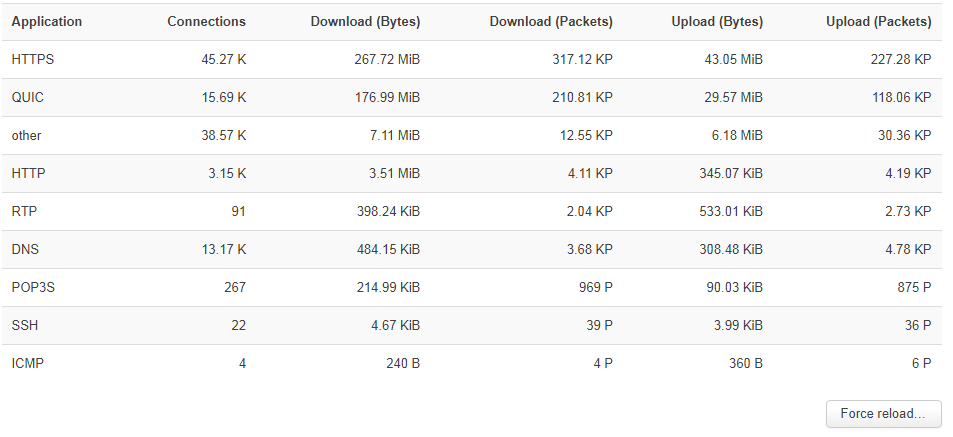
but it doesn't appear in the display list (although tcpdump shows traffic with just this protocol and port number).
I fear, I'm missing something, but I don't know what?
Any experienced nlbwmon user near by?