CS7 and CS5 will both be the same within cake, but CS7 can be interpreted badly by some switches and some ISPs so if you send it out to your ISP they can maybe treat it badly. But the same is actually true for any DSCP, it's just what tests work for you.
OK, I've got today's snapshot loaded with nftables-json and kmod-nft-nat. I disabled ssh on WAN per the comments in the conf file. I also was able to re-enable the wanin ingress chain using the variable $wan without any errors, so results will depend on 21.02 versus snapshot.
Now I want to experiment with sets and dnsmasq. Does nftables differentiate between ipv4 and ipv6 in a set?
EDIT: nftables set in dnsmasq comes in the next 2.87 version.
Yes, each set must be one or the other so you'll need two sets and two rules
I pushed some enhancements, including setting up a low priority ipv4 and ipv6 set, so you can either edit the file, or run nft commands to pre-load some ip addresses, or hook that to dnsmasq once that lands.
nftable sets and maps are huge performance enhancements vs a sequence of repeated rules, so it's best to utilize them rather than have rule after rule like in iptables.
@dlakelan i had to make some changes to the lines for it to work
.
masqin chain:
iifname $lan udp dport 53 redirect to 5353 #to redirect your DNS on the router
input chain:
iifname $lan tcp dport {8080} accept # adguard web acces
iifname $lan udp dport {domain,5353} meter dommeter4adguard { ip saddr limit rate 240/minute burst 240 packets} accept
iifname $lan udp dport {domain,5353} meter dommeter6adguard { ip6 saddr limit rate 240/minute burst 240 packets} accept
Yea I was using the same command as you except I was using br-lan. I only was using CS7 to better differentiate between my rules and the rules Daniel made when looking at the wireshark table. I once made some tests with different DSCP Tags for the high priority class (CS5,CS6,CS7,EF) in @dlakelan‘s gaming script and none of them really made a difference for my gaming experience so I guess my Isp is washing them or at least does not treat them in any way. So in his script all these high priority tags will also go into the same class and as Daniel said it’s the same here with cake. It goes all to the Voice tin so it should not really make a difference. Played 1 or 2 test games with these settings and got a Warzone dub despite using cs7 yesterday.
What really would be interesting for gaming is using a NFtable version of Daniels gaming script.
Once we have enough testing and have worked out some of the issues here it should be pretty straightforward to translate.
ok i don't understand when you said you had a dub?
but to have CS7 in 3074 you have to add something like that which we spoke at the beginning with daniel?
define gameports = {3074,3659,9308,30000-45000} ## or whatever ....
udp dport $ gameports ip dscp set cs5
udp dport $ gameports ip6 dscp set cs5
udp sport $ gameports ip dscp set cs5
udp sport $ gameports ip6 dscp set cs5
edit : i has download a old script 
Dub = Win
I don’t know what you mean? Yea i added a few lines in the script to tag port 3074 udp as cs7….
daniel has add like that
define bulksize = 35000000 ## total transfer before being sent to CS1
define voipservers = {10.0.98.113} ## add ipv4 addresses of fixed voip / telephone servers you use here
define cs5ports = {123,3478-3479,25565} # high priority ports udp + tcp
define af41ports = {10000,8801-8810} # jitsi meet, and zoom
ah ok sorry i didn't understand for win 
Hi @dlakelan could you check this error?
root@OpenWrt:~# /etc/init.d/nftables restart
restart
/etc/nftables.conf:102:36-42: Error: Could not resolve service: Unrecognized service
elements = {3074 : 192.168.1.55, 1.1.1.1 : 192.168.1.55} # set these up to map ports to specific internal IPs
^^^^^^^
If I remove 1.1.1.1 : 192.168.1.55 than it works
The format of the map is Port : IP address, you have put IP address : IP address.
what a bstrd 
Misunderstood the port 8888 like a dns ahah
Thanks!
hello everybody my tc -s qdisc after a long games
root@OpenWrt:~# tc -s qdisc
qdisc noqueue 0: dev lo root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 0: dev eth0 root refcnt 2 limit 10240p flows 1024 quantum 1518 ta rget 5ms interval 100ms memory_limit 4Mb ecn drop_batch 64
Sent 1808332356 bytes 3094850 pkt (dropped 0, overlimits 0 requeues 6)
backlog 0b 0p requeues 6
maxpacket 1508 drop_overlimit 0 new_flow_count 28 ecn_mark 0
new_flows_len 0 old_flows_len 0
qdisc noqueue 0: dev lan1 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev lan2 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev lan3 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc noqueue 0: dev lan4 root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc cake 8011: dev wan root refcnt 2 bandwidth 16Mbit diffserv4 triple-isolate nonat nowash no-ack-filter split-gso rtt 100ms noatm overhead 44
Sent 692632401 bytes 1584560 pkt (dropped 1104, overlimits 834928 requeues 0)
backlog 0b 0p requeues 0
memory used: 386090b of 4Mb
capacity estimate: 16Mbit
min/max network layer size: 28 / 1490
min/max overhead-adjusted size: 72 / 1534
average network hdr offset: 14
Bulk Best Effort Video Voice
thresh 1Mbit 16Mbit 8Mbit 4Mbit
target 18.2ms 5ms 5ms 5ms
interval 113ms 100ms 100ms 100ms
pk_delay 112us 3.46ms 106us 290us
av_delay 9us 205us 6us 134us
sp_delay 1us 6us 2us 4us
backlog 0b 0b 0b 0b
pkts 473311 436318 280 675755
bytes 369697222 210878549 44344 113653444
way_inds 0 17361 0 11287
way_miss 10 10793 49 3814
way_cols 0 164 0 0
drops 98 1006 0 0
marks 0 0 0 0
ack_drop 0 0 0 0
sp_flows 1 1 0 1
bk_flows 0 1 0 0
un_flows 0 0 0 0
max_len 26414 31584 914 1322
quantum 300 488 300 300
qdisc cake 800b: dev br-lan root refcnt 2 bandwidth 56Mbit diffserv4 triple-isol ate nonat nowash no-ack-filter split-gso rtt 100ms noatm overhead 44
Sent 1103103945 bytes 1509226 pkt (dropped 3461, overlimits 1035876 requeues 0)
backlog 0b 0p requeues 0
memory used: 634638b of 4Mb
capacity estimate: 56Mbit
min/max network layer size: 28 / 1500
min/max overhead-adjusted size: 72 / 1544
average network hdr offset: 14
Bulk Best Effort Video Voice
thresh 3500Kbit 56Mbit 28Mbit 14Mbit
target 5.19ms 5ms 5ms 5ms
interval 100ms 100ms 100ms 100ms
pk_delay 9.54ms 864us 71us 27us
av_delay 5.74ms 180us 5us 3us
sp_delay 126us 1us 3us 2us
backlog 0b 0b 0b 0b
pkts 412257 477089 277 623064
bytes 418496433 501295828 47346 188454102
way_inds 0 7917 0 189
way_miss 13 9894 4 827
way_cols 0 17 0 0
drops 1000 2461 0 0
marks 0 0 0 0
ack_drop 0 0 0 0
sp_flows 2 2 1 0
bk_flows 0 1 0 0
un_flows 0 0 0 0
max_len 13536 18048 2324 1330
quantum 300 1514 854 427
root@OpenWrt:~#
to start
with those who arrive on the way,
I did the following:
open putty
and download
opkg update
opkg install nftables kmod-nft-nat
then
in putty always
cd /etc
wget https://raw.githubusercontent.com/dlakelan/OpenWrtNFTables/main/nftables.conf
then
cd /etc/init.d
wget https://raw.githubusercontent.com/dlakelan/OpenWrtNFTables/main/nftables
then in putty always
Summary
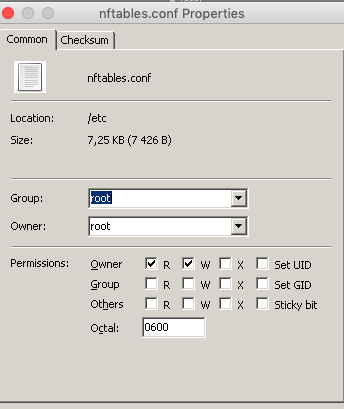
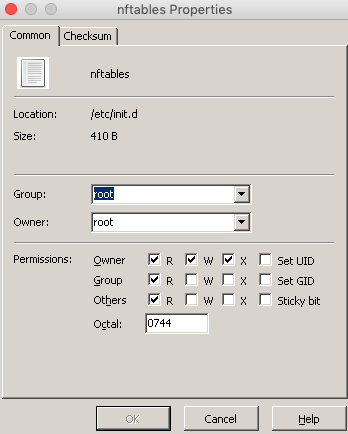
chmod 600 /etc/nftables.conf
chmod 744 /etc/init.d/nftables
/etc/init.d/nftables enable
/etc/init.d/firewall disable
/etc/init.d/firewall stop
I didn't need to do this command because nft-nat was already in the modules.d file
echo "nf_nat" >> /etc/modules "not necessary"
important place in your script the true interface of router
define wan = eth1 the mine is wan
define lan = eth0 the mine is br-lan
then test with nft list ruleset for see appair the rules in putty
to be sure it works, I restarted the router and my firewall was still deactivated and the nftables rules were launched.
the dmz doesn't work at my home so i had add the port forward manually 3074.... like this in the script,
tell me if I left out something.
ps : i would like add my vpn ? is possible
Yes, it should be possible, you can probably just treat it like WAN (unless it's a site-to-site VPN for a second LAN).
define wan = {wan,vpn} #change name of device to your vpn device name
might work by itself. There might be some other tricks needed.
ok usually i use luci-app-open-vpn with open-ssl and my file in it
this manipulation is necessary I suppose again
then I create the vpn interface
then I put I apply the rules of the firewall which I think will no longer be necessary ... for the latter since it has replaced by nftables?
you will have to edit the nftables to enable the vpn instead of adjusting iptables rules. You want to treat the VPN like a second WAN probably.
It seems strange to add the VPN to the LAN firewall zone. Setting up the VPN itself should be exactly the same, you just need to know what is the device name for the VPN tunnel device. In your case tun0
Then start with trying
define wan = {wan,tun0}
in the nftables script.
ok i wil try
so
define wan = {wan,tun0} #change name of device to your vpn device name
ok put nothing here ?
no lan and no wan
or i make custom tun0
ok no error this time