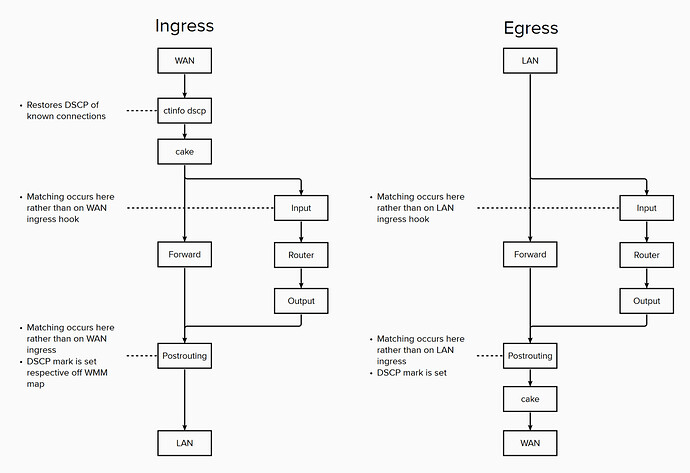
From a level I've implemented by classifification logic on the Input (to router) and postrouting (forwarded/instigated by router) hooks, rather than on the device ingress hooks.
The main rationalle here is so that I have full visibility of translated client/host IP addresses.
I've two classification methods:
- Compare the first non-connmarked packet travelling in the original connection direction against pre-defined rules, any packets that do not match a rule are marked with the dynamic bit.
- Any packets with a dynamic conntrack bit are sent to the dynamic chain
The dynamic chain has 3 mechanisms:
- Firstly the first packet of any new connectoin is sent to a connection threading detection chain
- This identifies any hosts which open >2 connections to the same service and IP range within 5 seonds.
- This identifies any hosts which open >10 connections from the same source port within 5 seconds.
- Any future packets which match one of the identified threaded sets are then assessed for reducing their DSCP class from CS0 to AF11/CS1.
- The first set works well at classifying threaded http downloads like steam.
- The second set works well at classifying P2P traffic (and importantly moving it into cake's bulk tin)
- The third mechanism emulates some of @ldir's iptables work and will increase the priority of low throughput small packet UDP streams (intended to capture game traffic)
No further logic occurs in the input chain (since it's already been received by its target host).
Packets in the postrouting chain are then DSCP marked either using the CT to WMM map (if exiting via LAN), or CT to DSCP map.
One could argue that the majority of forwarded packets from WAN to LAN should already have the correct DSCP due to the ctinfo restore (and therefore they could be skipped rather than marked in postrouting), assuming they'd been classified previously and we don't want to use WMM retagging.
I do still think that the WMM marking is something I'd like to explore, as noted by @amteza OpenWrt APs themselves actually do put EF in the VO bucket, as do a lot of commercial routers - but some don't (and I would like consistency in my network regardless of the AP vendor).
I guess the argument of dimishing returns is valid, but it doesn't really introduce any more overhead since it's just using an alternative map.