No Always not
My router renew each every 3 secondes the new dhcp at my pc
But i has access to putty and winscp
ok is good now  i has changed my name of interface !
i has changed my name of interface !
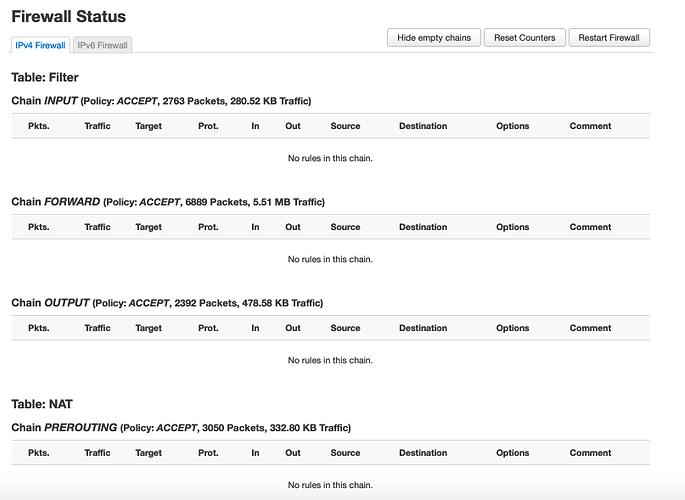
firewall is disabled i has access to internet
my firewall is empty
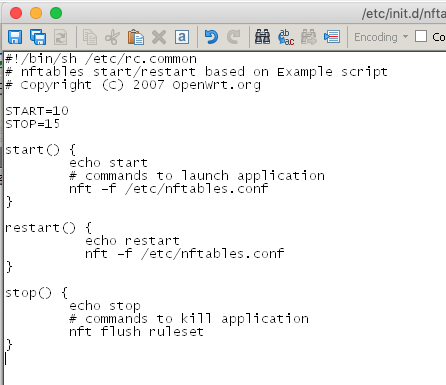
i has put the script like this
## this assumes eth0 is LAN and eth1 is WAN, modify as needed
flush ruleset
## change these
define wan = eth1
define lan = br-lan
define guest = eth0.10 # or remove these if you don't use guest or iot networks
define iot = eth0.5 ## but be sure to also remove the reference to them below
define bulksize = 35000000 ## total transfer before being sent to CS1
define voipservers = {10.0.98.113} ## add ipv4 addresses of fixed voip / telephone servers you use here
table inet filter {
chain input {
type filter hook input priority 0; policy drop;
# established/related connections
ct state established,related accept
# loopback interface
iifname lo accept
## icmpv6 is a critical part of the protocol, we just
## accept everything, you can lookin to making this
## more restrictive but be careful
ip6 nexthdr icmpv6 accept
# we are more restrictive for ipv4 icmp
ip protocol icmp icmp type { destination-unreachable, router-solicitation, router-advertisement, time-exceeded, parameter-problem } accept
ip protocol igmp accept
ip protocol icmp meta iifname $lan accept
## ntp protocol accept from LAN
udp dport ntp iifname $lan accept
## DHCP accept
iifname $lan ip protocol udp udp sport bootpc udp dport bootps log prefix "FIREWALL ACCEPT DHCP: " accept
## DHCPv6 accept from LAN
iifname $lan udp sport dhcpv6-client udp dport dhcpv6-server accept
## allow dhcpv6 from router to ISP
iifname $wan udp sport dhcpv6-server udp dport dhcpv6-client accept
# SSH (port 22), limited to 10 connections per minute per source host,
# you might prefer to not allow this from WAN for
# OpenWrt, in which case you should also add an
# iifname $lan filter in the front so we're only
# allowing from LAN
ct state new tcp dport ssh meter ssh-meter4 {ip saddr limit rate 10/minute burst 15 packets} accept
ct state new ip6 nexthdr tcp tcp dport ssh meter ssh-meter6 {ip6 saddr limit rate 10/minute burst 15 packets} accept
## allow access to LUCI from LAN
iifname $lan tcp dport {http,https} accept
## DNS for main LAN, we limit the rates allowed from each LAN host to reduce chance of denial of service
iifname $lan udp dport domain meter dommeter4 { ip saddr limit rate 240/minute burst 240 packets} accept
iifname $lan udp dport domain meter dommeter6 { ip6 saddr limit rate 240/minute burst 240 packets} accept
iifname $lan tcp dport domain meter dommeter4tcp { ip saddr limit rate 240/minute burst 240 packets} accept
iifname $lan tcp dport domain meter dommeter6tcp { ip6 saddr limit rate 240/minute burst 240 packets} accept
## allow remote syslog input? you might want this, or remove this
# iifname $lan udp dport 514 accept
counter log prefix "FIREWALL INPUT DROP: " drop
}
chain forward {
type filter hook forward priority 0; policy drop;
ct state established,related accept
iifname lo accept
iifname {$guest,$iot} oifname $lan drop ## guests can't connect to LAN
iifname {$lan,$guest,$iot} oifname $wan accept ## allow inside to forward to WAN
counter log prefix "FIREWALL FAIL FORWARDING: " drop
}
}
## masquerading for ipv4 output on WAN
table ip masq {
chain masqout {
type nat hook postrouting priority 0; policy accept;
oifname $wan masquerade
}
## this empty table is required to make the kernel do the unmasquerading
chain masqin {
type nat hook prerouting priority 0; policy accept;
}
}
## lets create a tagger table
table inet tags {
#chain wanin {
# type filter hook eth1 device eth1 priority 0; ## FIXME, this can't be a variable so put your WAN device here
# jump tagchain
#}
chain tagrouted {
type filter hook postrouting priority 0; policy accept;
jump cttags
}
chain cttags {
ip protocol tcp tcp sport != {2049} ip dscp < af41 ct bytes ge $bulksize ip dscp set cs1
ip6 nexthdr tcp tcp sport != {2049} ip6 dscp < af41 ct bytes ge $bulksize ip6 dscp set cs1
ip protocol udp ip dscp < cs5 udp dport != {http,https,domain} udp sport != {http,https,domain} meter udp4meter {ip saddr . ip daddr . udp sport . udp dport limit rate over 200/second burst 100 packets } counter ct mark set 0x55
ip6 nexthdr udp ip6 dscp < cs5 udp dport != {http,https,domain} udp sport != {http,https,domain} meter udp6meter {ip6 saddr . ip6 daddr . udp sport . udp dport limit rate over 200/second burst 100 packets } counter ct mark set 0x55
ct mark 0x55 numgen random mod 10000 < 5 ct mark set 0x00 comment "small probability to unmark over-threshold connections"
## prioritize small packet udp flows on any ports:
ct mark != 0x55 ip protocol udp ip dscp < cs5 udp dport != {http,https,domain} udp sport != {http,https, domain} ct avgpkt 0-450 counter ip dscp set cs5
ct mark != 0x55 ip6 nexthdr udp ip6 dscp < cs5 udp dport != {http,https,domain} udp sport != {http,https,domain} ct avgpkt 0-450 counter ip6 dscp set cs5
jump tagchain
}
chain tagchain {
## VOIP servers UDP traffic
ip saddr $voipservers ip protocol udp ip dscp set cs6
ip daddr $voipservers ip protocol udp ip dscp set cs6
## tag UDP that stays below 200pps and 450 bytes per packet to CS5 priority
## udp flows that have more than 200 packets per second get marked 0x55, then non 0x55 flows
## with avg packetsize less than 450 bytes get marked cs5
#playstation network port
udp dport 3478-3479 ip dscp set cs5
udp dport 3478-3479 ip6 dscp set cs5
udp sport 3478-3479 ip dscp set cs5
udp sport 3478-3479 ip6 dscp set cs5
# minecraft java edition source
tcp sport 25565 ip dscp set cs5
tcp sport 25565 ip6 dscp set cs5
# minecraft java edition dest
tcp dport 25565 ip dscp set cs5
tcp dport 25565 ip6 dscp set cs5
# jitsi meet:
udp sport 10000 ip dscp set af41
udp dport 10000 ip dscp set af41
# zoom udp
udp sport {3478,3479,8801-8810} ip dscp set af41
udp dport {3478,3479,8801-8810} ip dscp set af41
}
}
 i has changed my name of interface !
i has changed my name of interface !