Greetings to all!!!
I have finally found some spare time and tried to tackle the still present issues that I would like getting sorted out.
I am proud and very satisfied to share that the DNS leaks belong to the past.
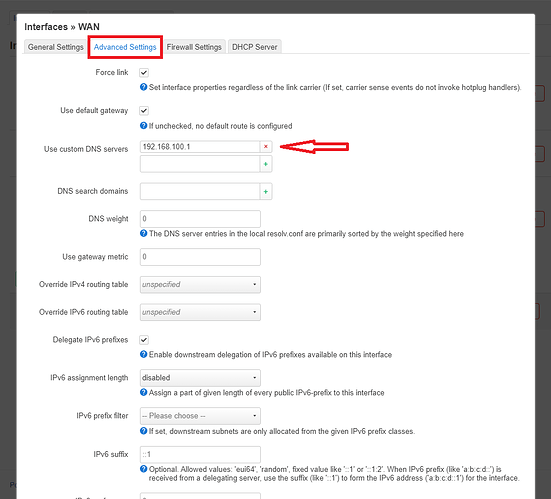
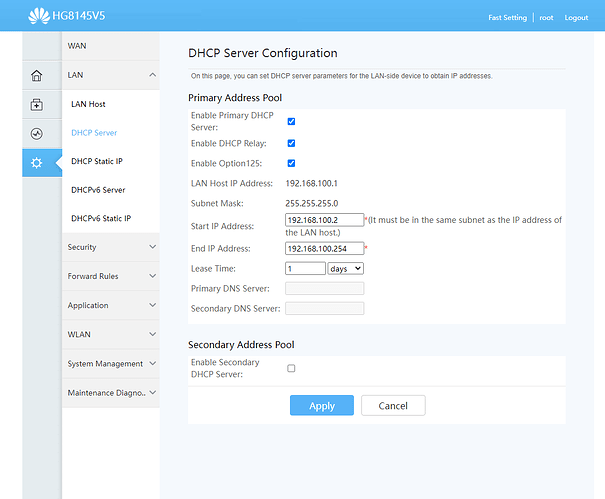
The reason for the DNS leak was the assigned custom DNS server in the WAN interface which is the stock IP address of the primary Huawei HG8145V5 router (192.168.100.1).
When I was instructed by Pavel on how to fix the faulty configured WAN interface he suggested to use the primary router's IP address which helped me to finally get the internet connection established between the 2 routers:

After that I have installed the OpenVPN and was confronted with unexpected low internet speeds and constant DNS leaks.
As Peter explained:
I was WRONGLY assuming that 50-60 Mbps was low internet speed caused by the use of OpenVPN and routing the traffic through the VPN provider's server.
In reality the above mentioned speed (I will come back to that later) was the regular internet speed circumventing the VPN tunnel as I was still using the primary router's DNS address (my ISP's one) while having the OpenVPN switched on. This also explains the constant DNS leakage.
After being disillusioned by the performance of OpenVPN I downloaded the Wireguard package as well as the configuration settings from the VPN provider.
In the configuration file I found out that 10.2.0.1 was the VPN provider's server and I used it to set it as custom DNS server in the WAN interface, just like IIeachii suggested:
So this was the culprit of the DNS leaks:
I have replaced the 192.168.100.1 custom server with the custom 10.2.0.1 DNS server.
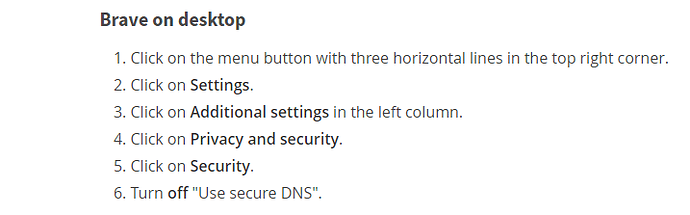
After that I still had DNS leaks but I found out that I also needed to adjust the settings in my Brave internet browser:
In all the internet browsers the "Use secure DNS" option should be switched off.
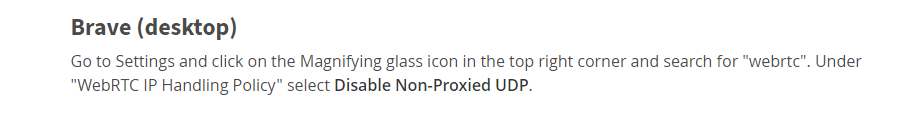
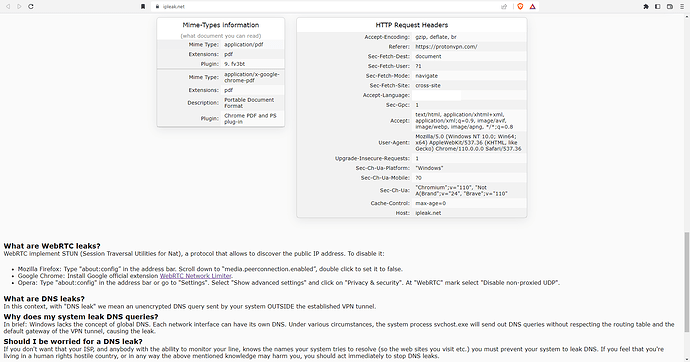
After testing my connection on the "mullvad.net" website I discovered that I also had WebRTC leaks and so I had to take care of them in the Brave browser too:
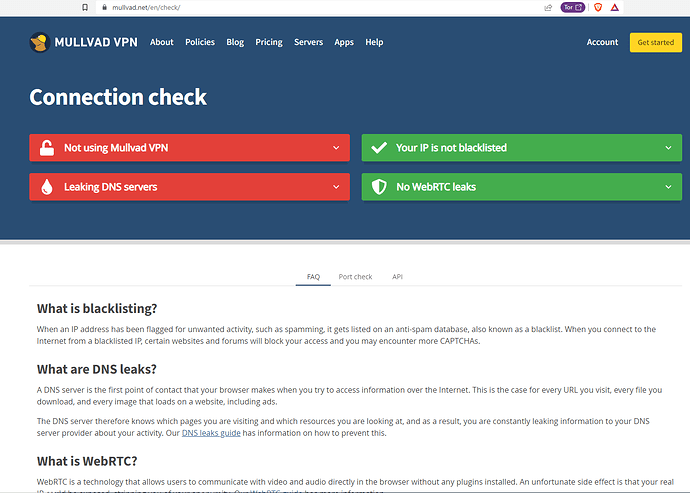
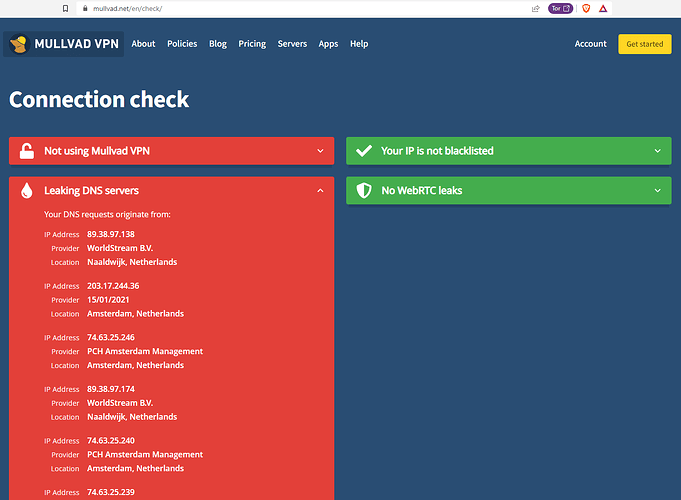
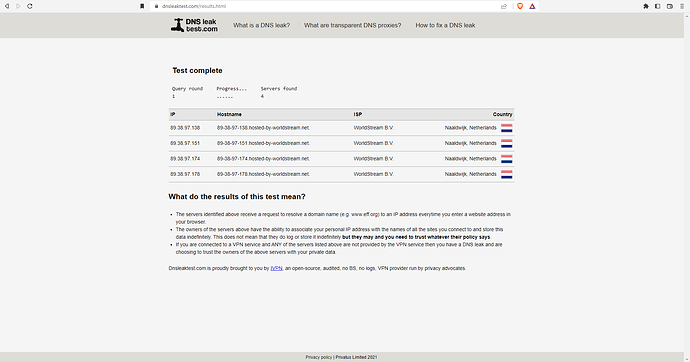
I visited the "mullvad.net" website and a few other sites to check if my DNS & WebRTC were still leaking. These are the results:
It says that my DNS servers are still leaking:
These leaks are okay as they all belong to the VPN provider's servers and not to my ISP's servers.
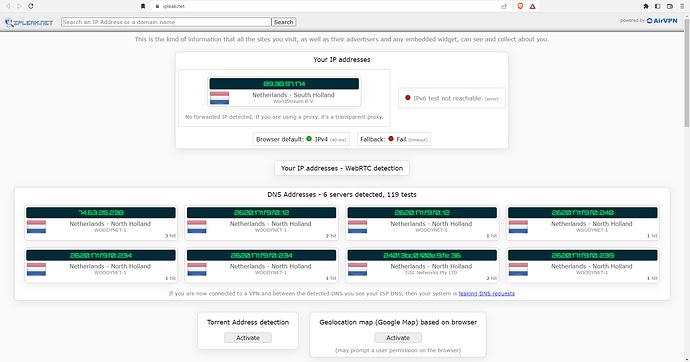
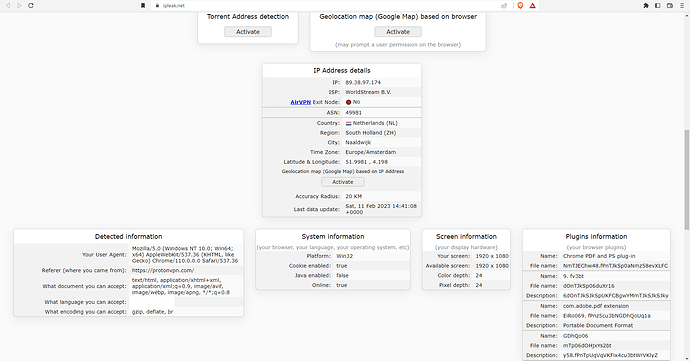
A few other results:
Same here, the leaked DNS servers are not my ISP's servers and are related to my VPN IP address.
re
With that being sorted out I do have one more question regarding the custom DNS
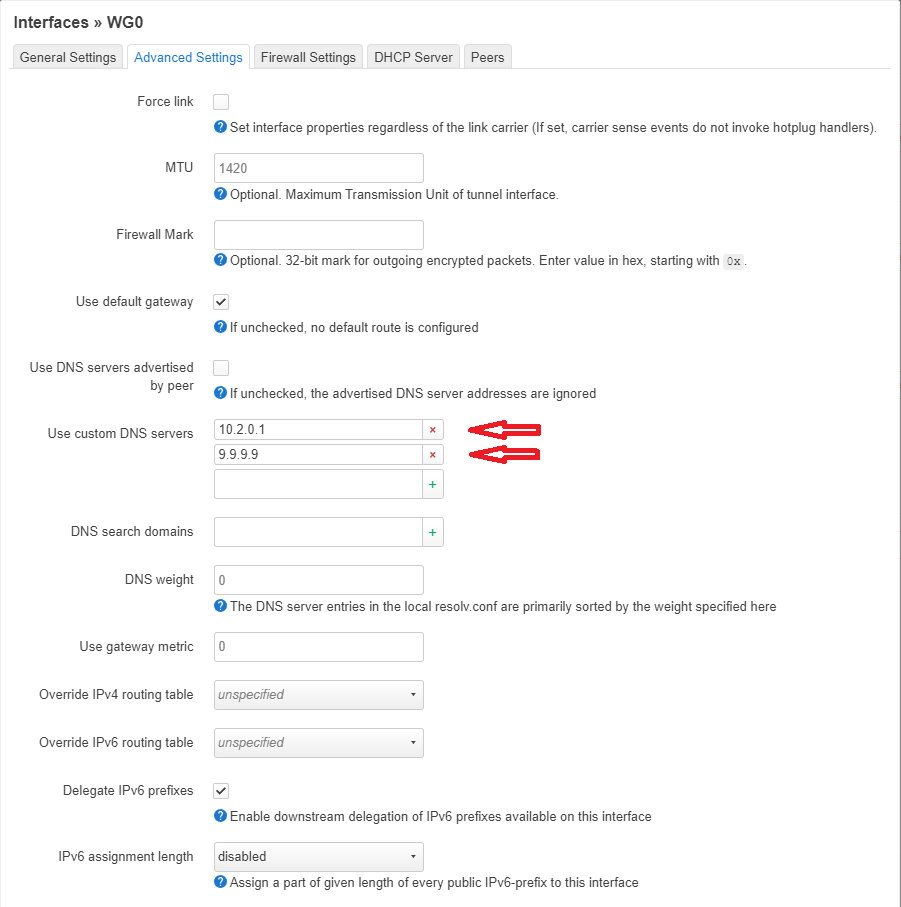
servers. Later when making Wireguard interface I decided to add an additional custom DNS server to it as well to the WAN interface:
My question would be..... If my VPN provider's server (10.2.0.1) would shut down for some reason, would my connection automatically be routed through the 2nd custom DNS server (9.9.9.9)? Or in other words, what is the benefit of having the 2nd custom DNS server listed if the VPN provider's server shuts down and with that (I assume) the Wireguard connection to the internet?
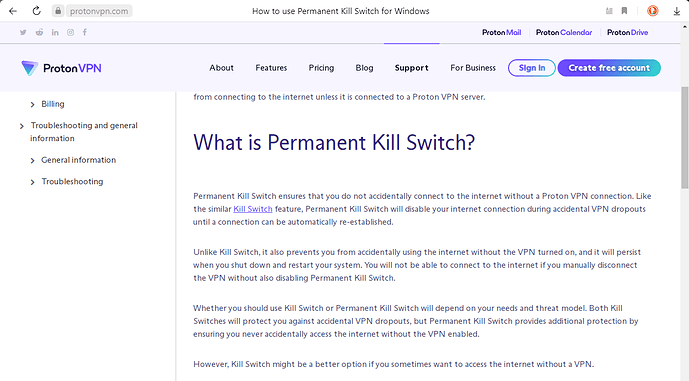
This brings me to another feature that I am interested in activating which is the "kill switch" function.
I have a free VPN account at "protonvpn.com" and they claim to have the "kill switch" and even a "permanent kill switch" function (which I prefer over the first one) but they are features built in their apps which need to be installed depending on what kind of OS one is running. The main reason I wanted the VPN on the router instead of on each device separately is the assurance that any device routed through the VPN tunnel would be behind the VPN network. No headache and no constant adjustment of settings when wanting to go private or accidentally forgetting to turn on the VPN.
This is from the protonvpn website:
Basically I would like the connection to "drop dead" as soon as the connection with the VPN server fails and would like to have the connection re-established ONLY when the VPN server is up and running again. So under no circumstances would I want any device connected to this secondary ZTE MF283+ OpenWrt router to accidentally access the internet without a VPN.
I reckon that's what they mean by a "permanent kill switch".
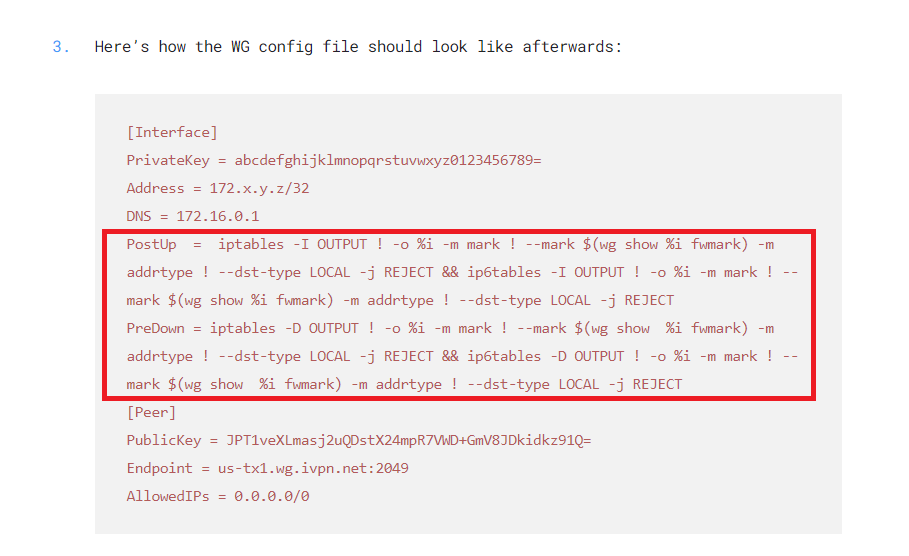
I have found this website which has a script that can be implemented in the Wireguard configuration file, like the one that I have downloaded from my VPN provider:
The linux command is outlined:
My question would be......
Is this the way to secure the "permanent kill switch" I am looking for?
Unlike with OpenVPN configuration file that needs to be uploaded the VPN provider's Wireguard configuration file just serves to copy/ paste things like public keys, IP address, DNS server, endpoint IP address, port and such. As this is all done manually I fail to see how adding these commands in the Wireguard configuration file would activate the kill switch. I believe that this might work on a machine with Linux OS but not on the OpenWrt router even though it is running on Linux. Someone please correct me if I am wrong.
Let me elaborate on how I've set up my Wireguard Interface so it is clear for everyone and also it might serve as a tutorial some day for anyone reading this thread:
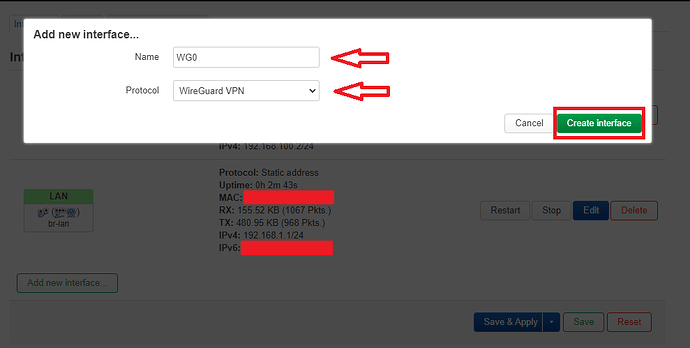
I went to "Network" tab and Clicked on "Interfaces" where I clicked on "Add new interface".
I named the Wireguard interface "WG0" and as Protocol I selected "Wireguard VPN"
Then I clicked on "Create Interface" which brought me to the next screen:
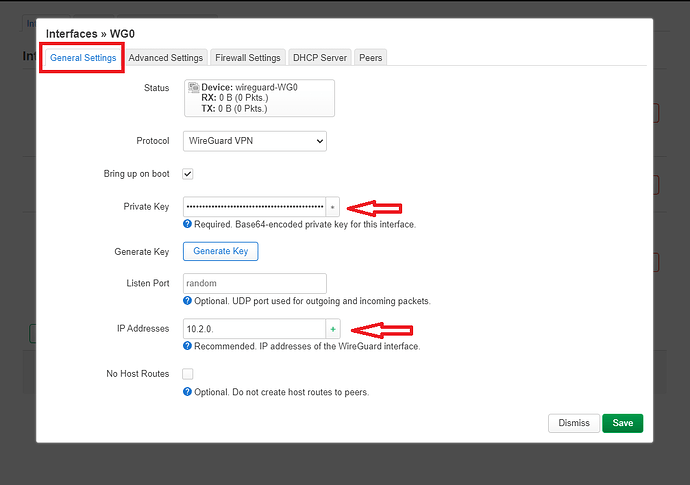
From the Wireguard configuration file that I've obtained from my VPN provider I filled in the "Private Key" & "IP Addresses" fields.
*NOTE - When copy/ pasting the public key leave out the first "=" sign
"=" GvTwYlaHjneUjksnKbMeSr/Ty345kl/abGus/=
Copy/ paste only the part in bold letters style.
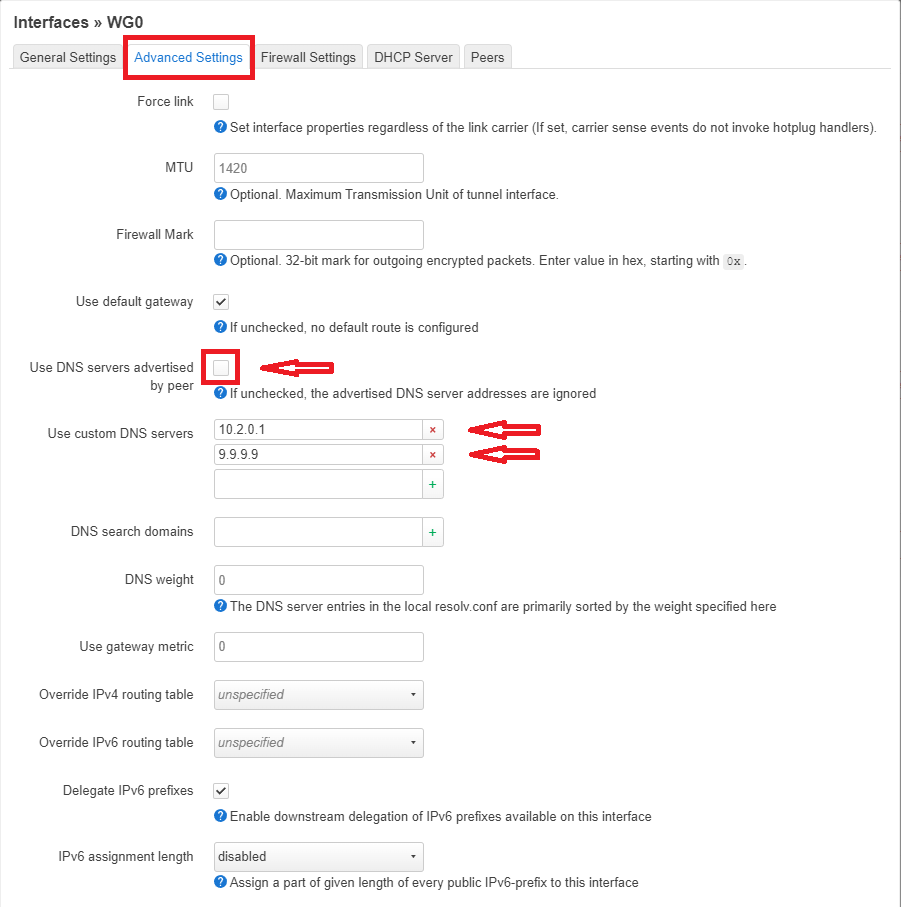
After that I moved on to the "Advanced Settings" tab:
Here I have uncheked the "Use DNS advertised by peer" check box and added 2 custom DNS server adressess "10.2.0.1" (from my Wireguard configuration file" & "9.9.9.9" as a back-up server.
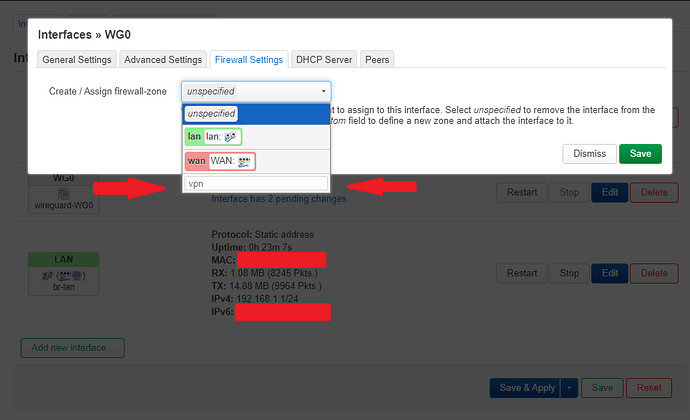
From here I moved on to the "Firewall Settings" tab:
Here I created a new firewall zone called "vpn".
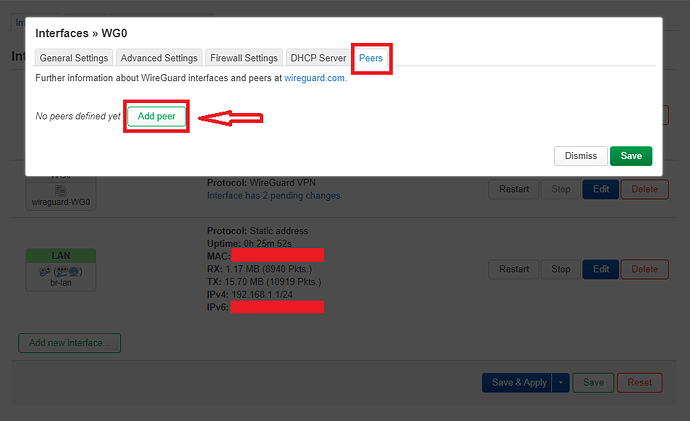
Then I went to the last tab which is the "Peers" tab.
Here I clicked on "Add peer"
Once opened, I performed the next steps:
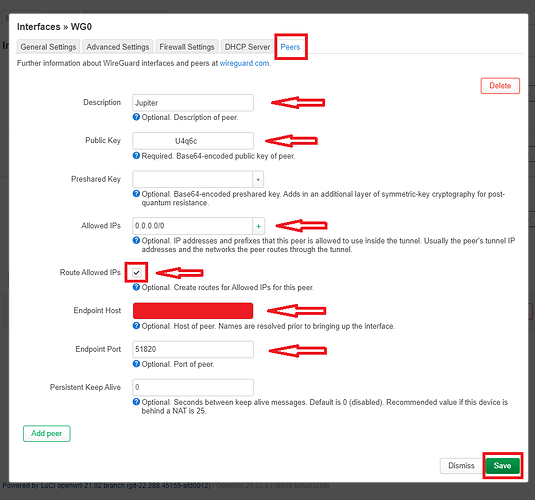
- In the "Description" field, I entered "Juppiter" (can be any random name)
- In the "Public Key"field I copy/ pasted the public key under the peer section from my VPN provider's configuration file
- In the Allowed IPs I copy/ pasted the allowed IPs also from the peer section of my VPN provider's configuration file (0.0.0.0/0)
- Next I checked off the "Route Allowed IPs" check box
- After that I once more copy/ pasted the details provided by my VPN provider to the "Endpoint Host" field
- And the same I did for the "Endpoint port" (51820)
- Finally I tapped on the "Save" button
*NOTE - When copy/ pasting the public key leave out the first "=" sign
"=" GvTwYlaHjneUjksnKbMeSr/Ty345kl/abGus/=
Copy/ paste only the part in bold letters style.
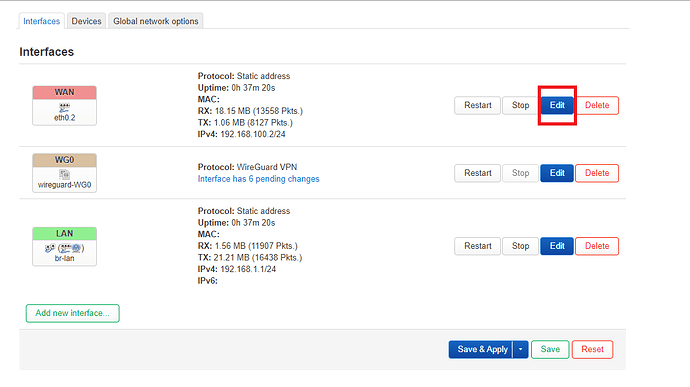
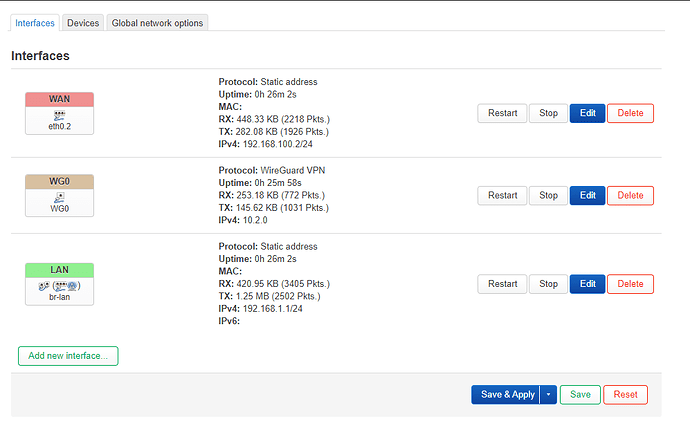
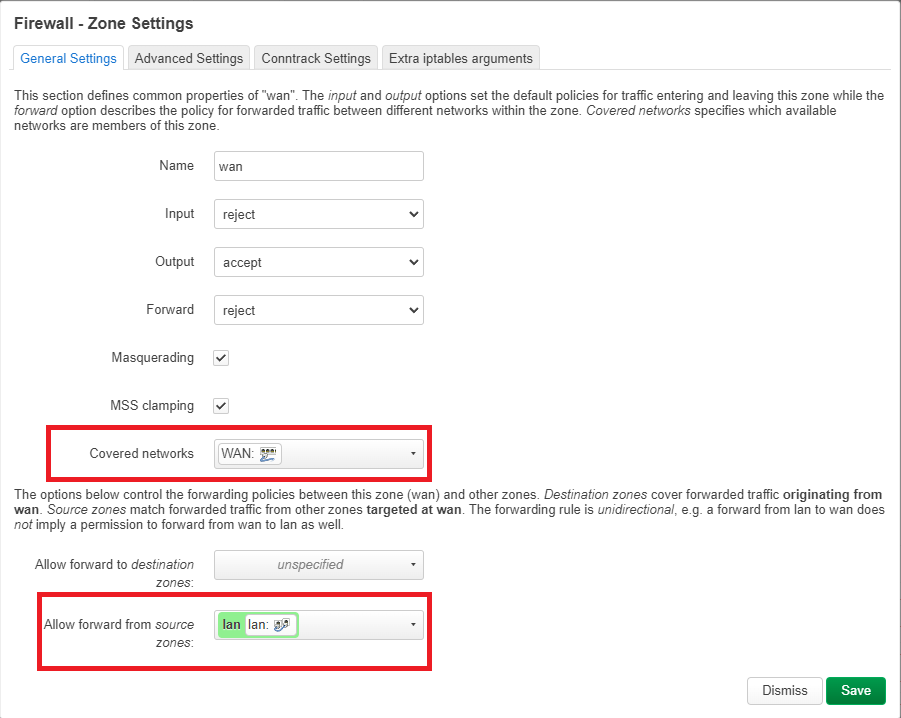
In the interfaces section I clicked on the "edit" button of the WAN interface so that the WAN interface also uses the DNS server provided by my VPN provider in order to prevent DNS leaking.
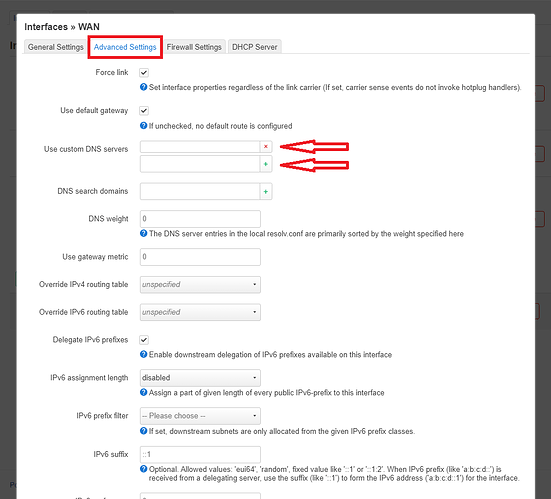
Here I entered the "10.2.0.1" (provided in the Wireguard configuration file by my VPN provider and "9.9.9.9" (provided by IIeachii ![]() ) custom DNS servers:
) custom DNS servers:
After that I clicked on "Save"
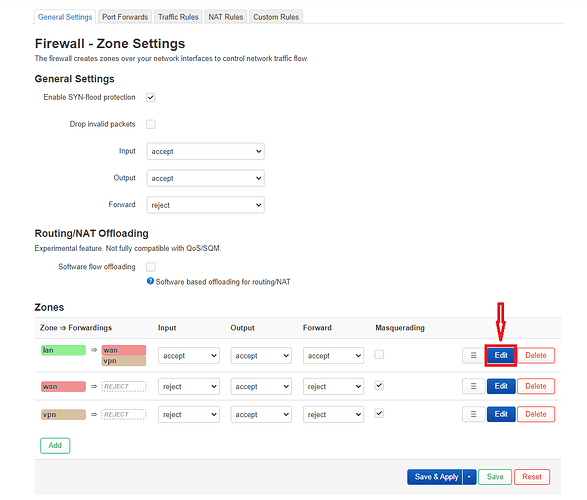
From there on I went to configure the VPN zone that I have just added.
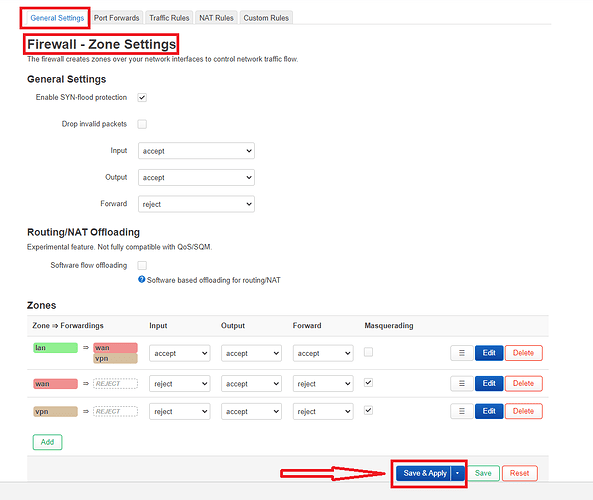
I clicked on "Network" tab and then selected the "Firewall" which brought me to "Firewall - Zone Settings".
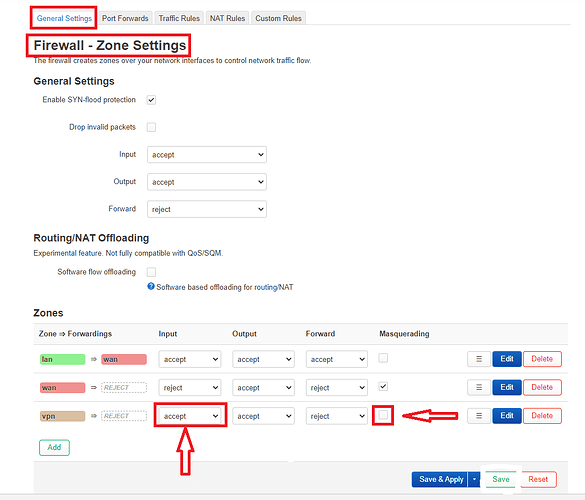
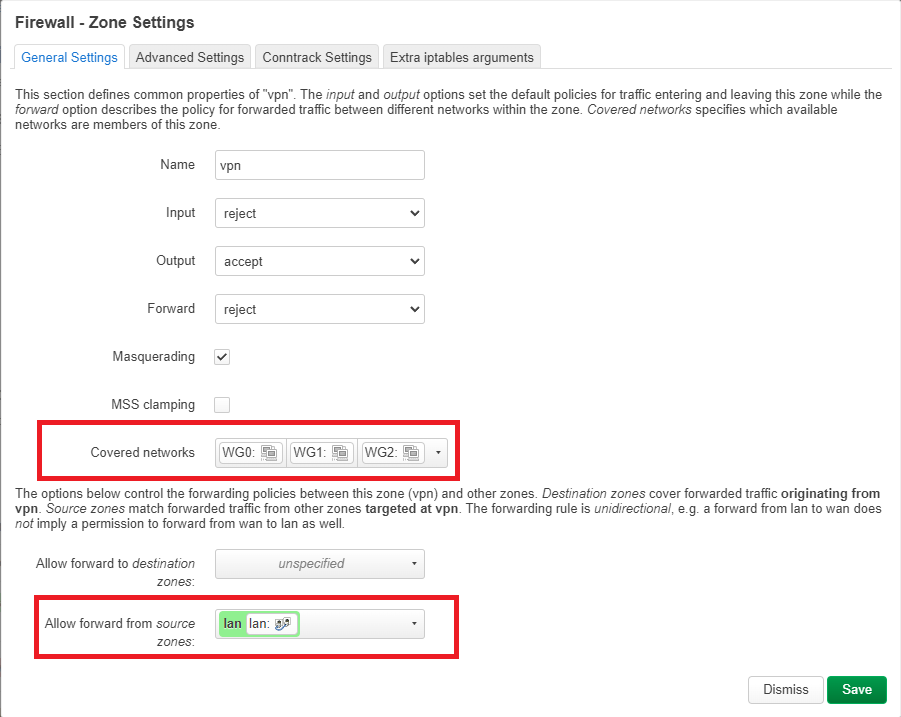
Here I made sure that the "vpn"zone would be the same as the "wan" zone.
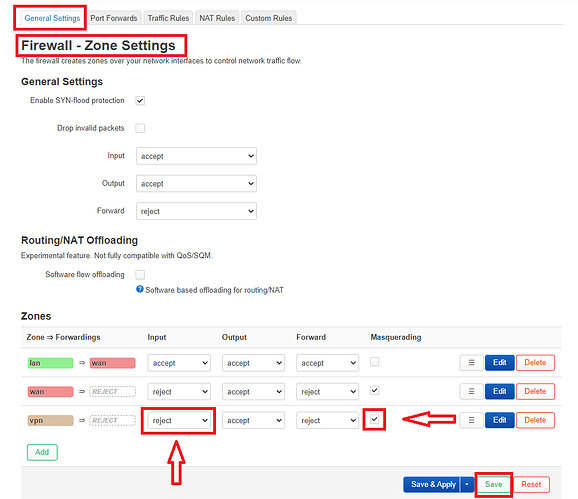
I did that by changing the "input" from "accept" to "reject" and then checking off the "Masquerading" check box. After that I tapped on the "Save" button.
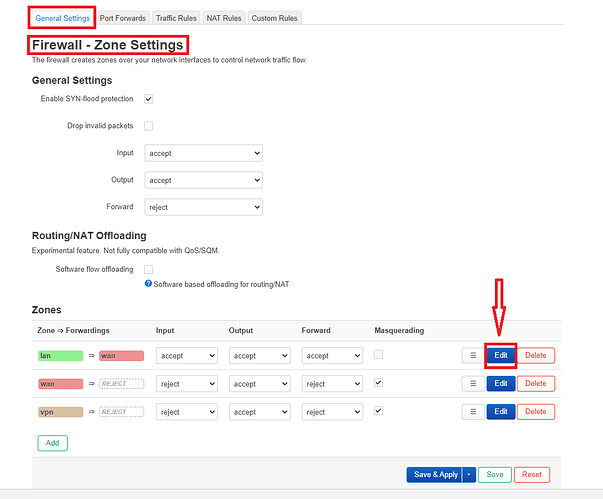
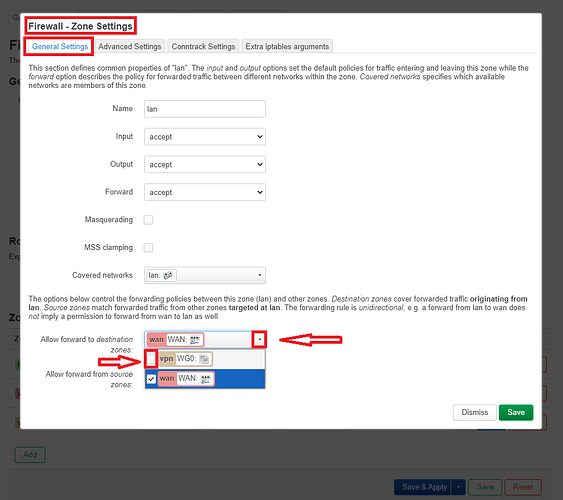
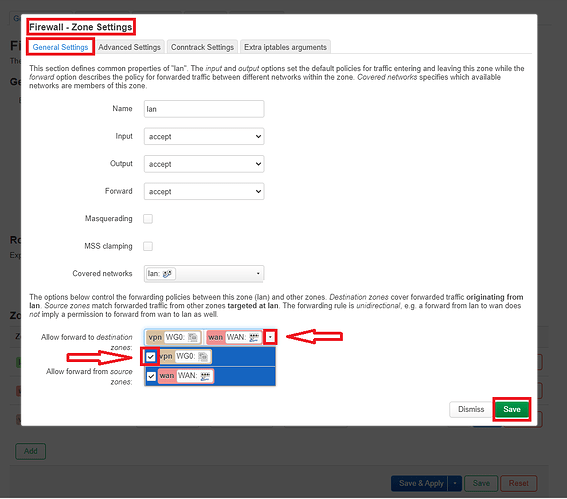
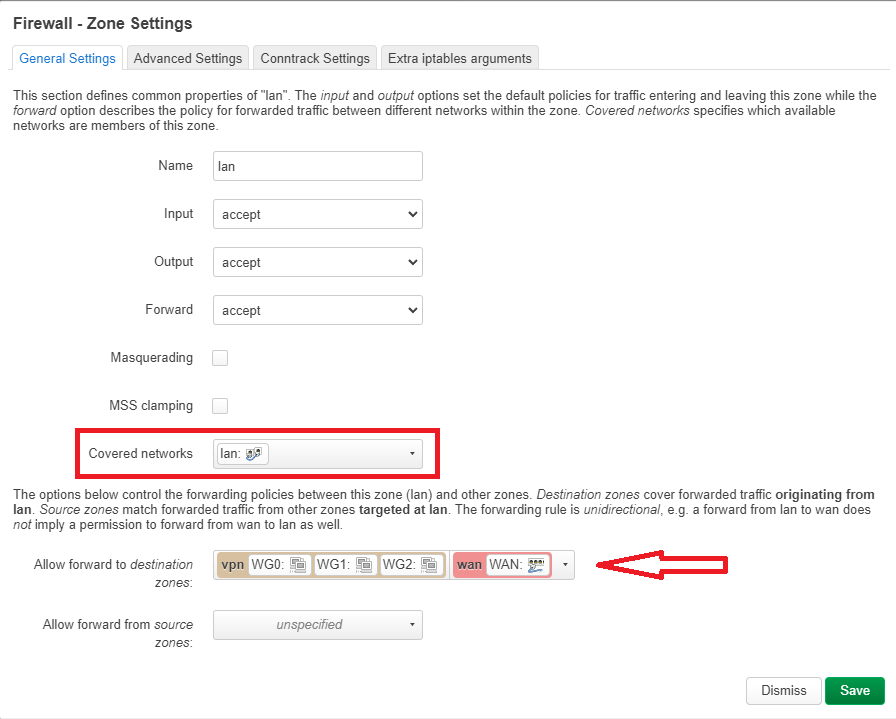
After that I went ahead to edit the zone forwarding from "lan"to "wan":
Here I have checked off the "vpn" check box under the "Allow forward to destination zones" field and then clicked on "Save'.
After that I went back to the "Firewall - Zone Settings" and clicked on "Save & Apply"
Finally I had my WG0 (Wireguard 0) inteface working:
My question would still be......
How do I create a permanent kill switch that does not allow any internet connections unless it is routed through the Wireguard interface?
While surfing on the net for possible solutions I ran into this thread on the OpenWrt forum: Luci-app-openvpn kill switch - #7 by nlx6
Although the topic here is creating a kill switch in OpenVPN, I believe that the same principle would apply for the Wireguard as the kill switch rule is created in the "Firewall - Zone Settings". @psherman
I believe my firewall configuration is the same as described above by Peter.
I am having problems with understanding the last part: "Now, you can remove the LAN > WAN forwarding......."
Where do I exactly remove that forwarding?
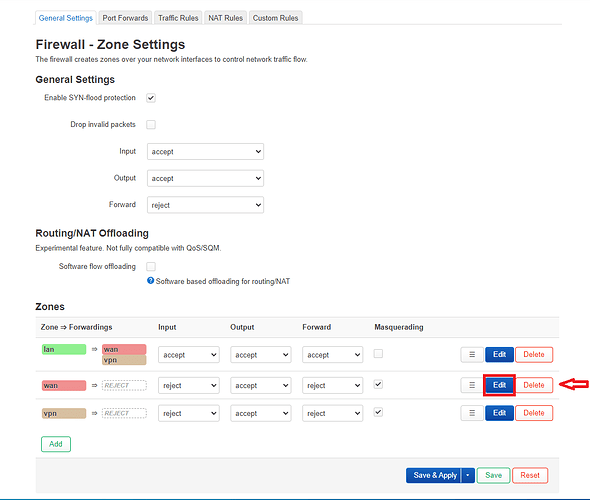
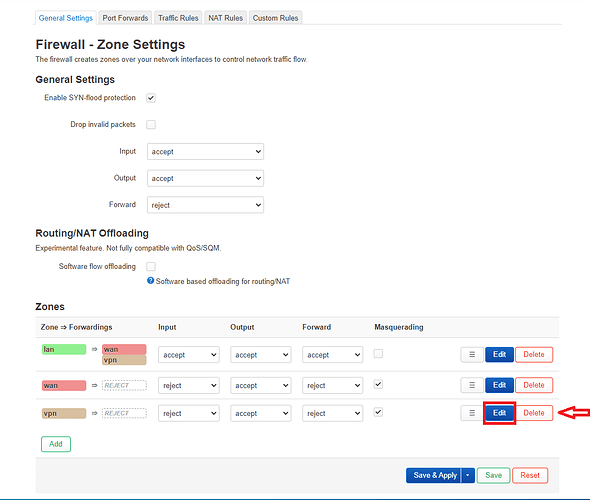
My firewall configuration:
lan>wan zone:
wan zone:
vpn zone:
When I turn off the WG0 (Wireguard) interface and try to access any website on the internet I get a "DNS address could not be found" error but I believe that is because of the custom DNS servers in the WAN interface. In the network center in Windows it says that I have the internet connectivity all the time.
I really need to implement that kill switch.
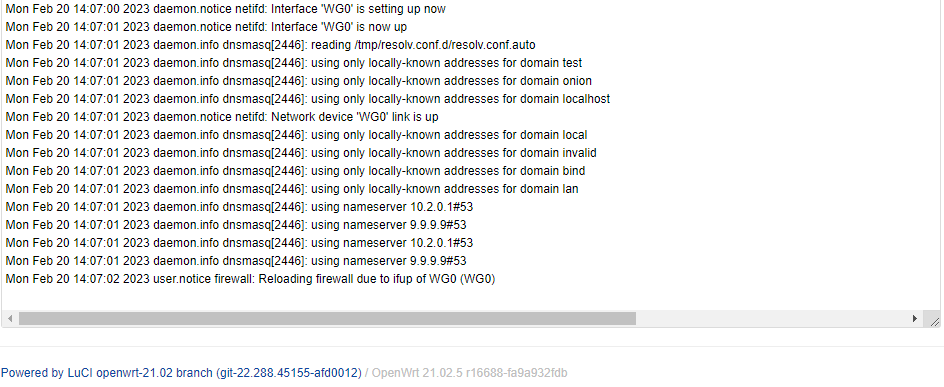
This is from the system log file and I do not see anywhere that the internet goes down when switching off the Wireguard interfaces:
And when turning one of them back on:
There's one more issue that I am struggling with.
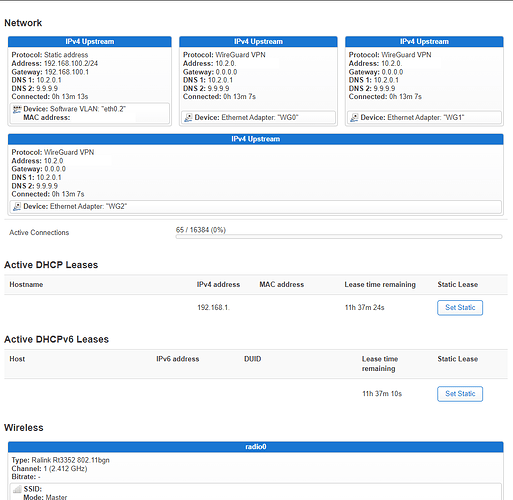
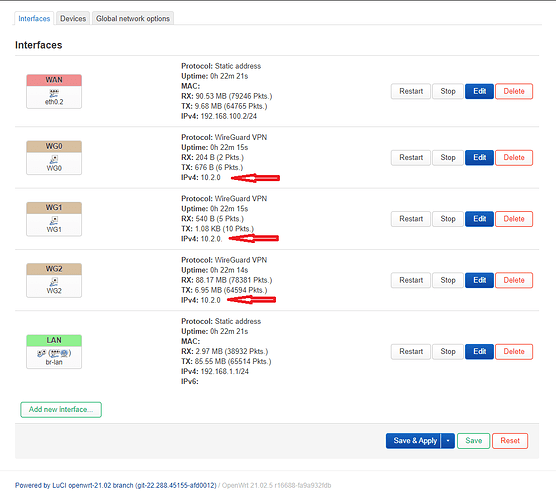
As I mentioned I have a free VPN service at ProtonVPN and I can use servers from 3 different countries. So what I did is create 3 separate Wireguard interfaces (WG0, WG1 & WG2). I have created the 2 extra interfaces the same way I did the first one on which I've elaborated above.
After I had created them, I switched them off except for the first Interface which is WG0 and everything was working fine. I created them so in case the 1st server goes down or I need a server in a different country to be able to switch to any other server desired at a given time. When I had OpenVPN I could also upload different servers and switch between them just by checking off the check box and starting or stopping the service with the selected server. That's where my idea came from to make 3 different Wireguard interfaces.
The problem I am facing is that when I turn on the router next time, all 3 of the servers become active and it slows down the internet or it breaks the connection totally.
This means that I have to log into the router each time when I turn it on and switch off all of the Wireguard interfaces and restart the one I would like to use at that time.
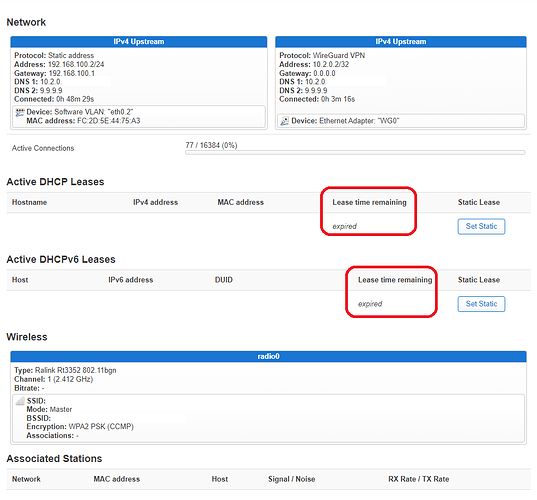
Not sure why the Lease time remaining for the NIC of my PC says "expired".
So my question would be........
Is there a way to prevent all 3 Wireguard interfaces (connections) to start at the same time? Like have only one of the servers start? Maybe with Policy Based Routing (just wild guessing here)? I would like to have a main server (WG0) start each time when I turn on the router and if possible, in case that the main server is down for some reason to automatically switch to the next server in queue (WG1) and if that one is offline to switch to the next one (WG2). It is kind of cumbersome having to log into OpenWrt each time and to switch all of them off and then to restart one of them in order to be able to use the internet.
Or is the only solution to delete the 2 other routers and when I wish to use another server to edit/ update the Wireguard configuration data in the WG0 interface?
I really like the ease of uploading multiple OpenVPN configuration files and being able to switch between them.
And now the last but not least.....
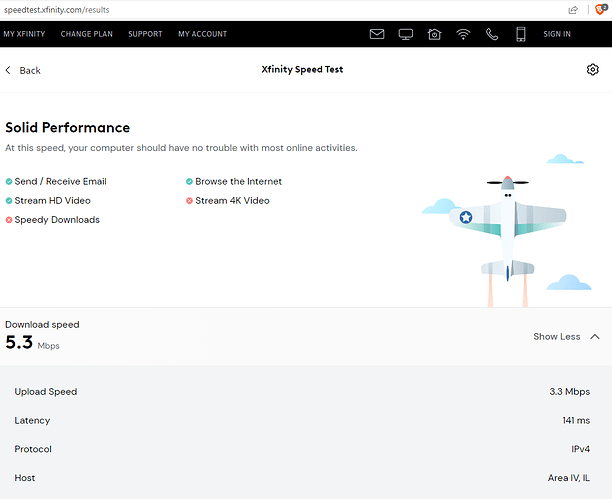
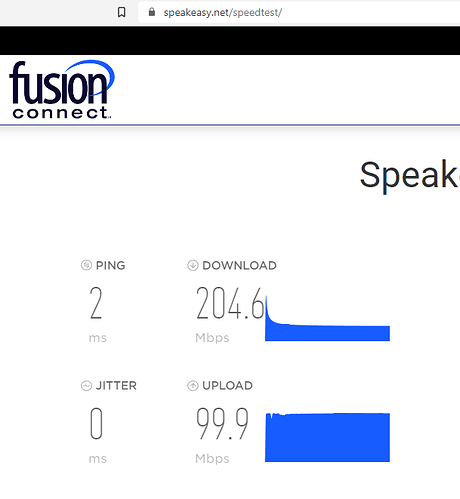
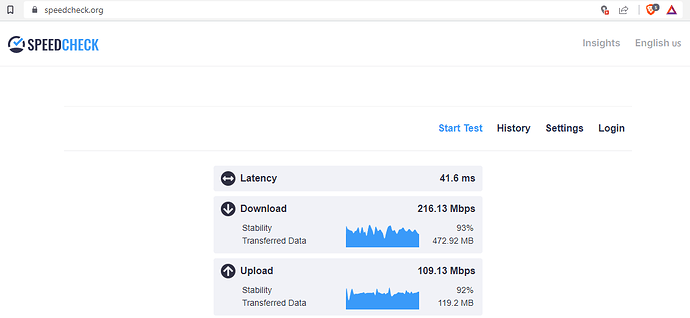
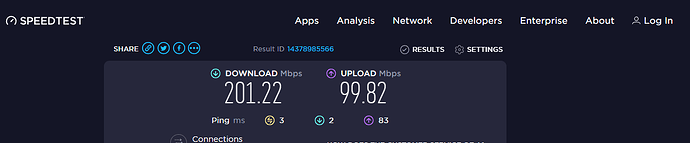
The internet speed issue which was already kind of discussed previously in this thread... The speed is horrendously low...
With OpenVPN protocol it is 40 times slower then the internet speed on the primary Huawei Echolife HG8145V5 router with fibre optic, and with Wireguard ONLY 20 times slower.

I will post several tests done on various sites:
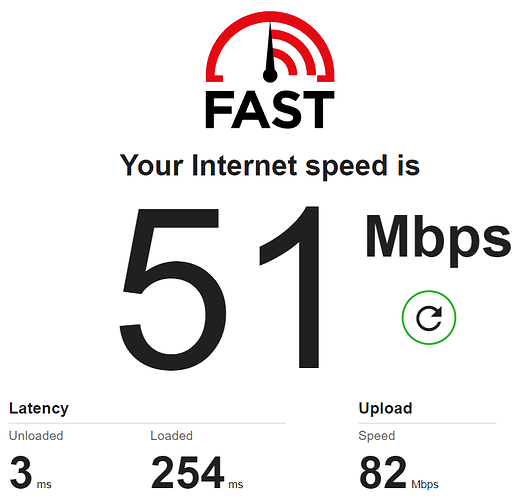
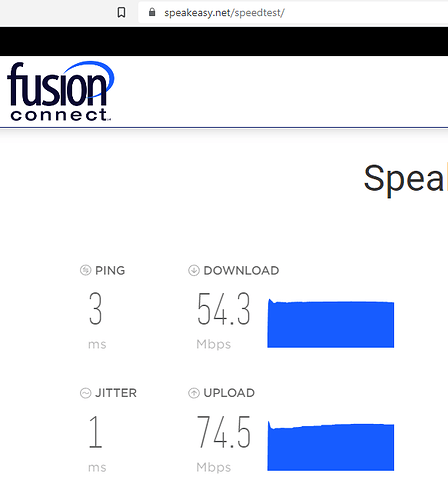
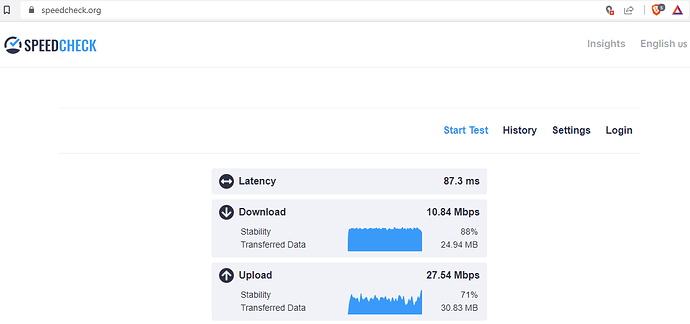
No VPN:
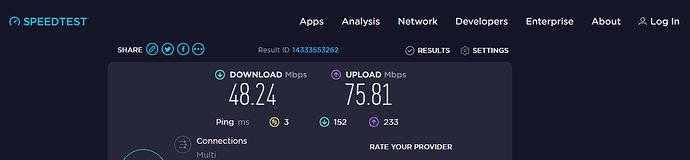
OpenVPN:
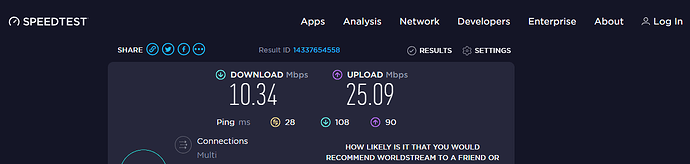
Wireguard:
No VPN:
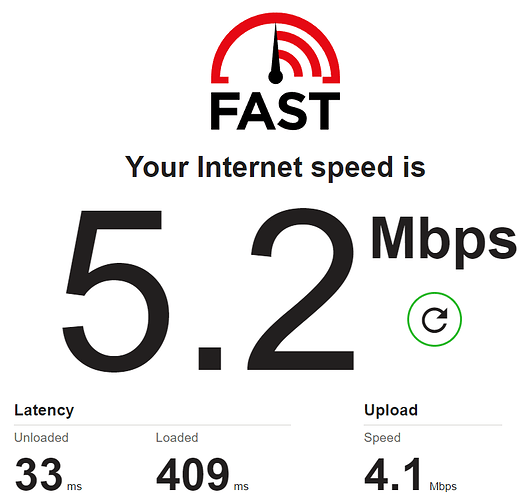
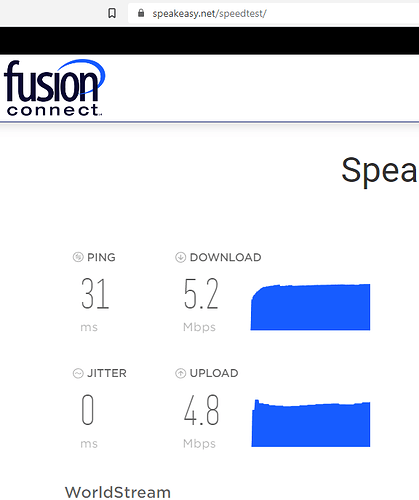
OpenVPN:
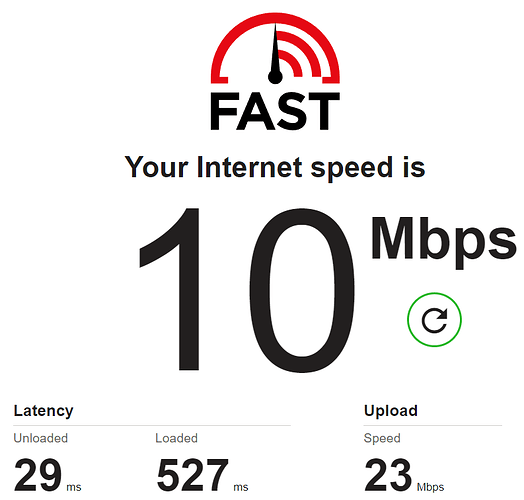
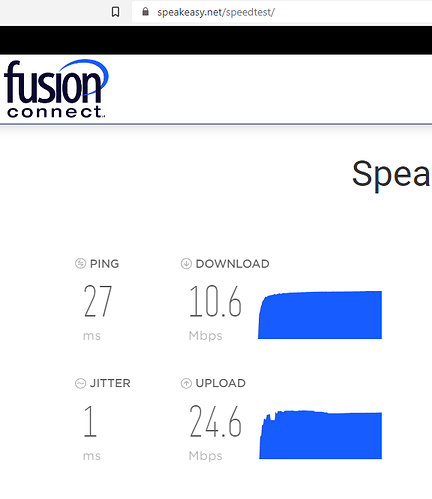
Wireguard:
No VPN:
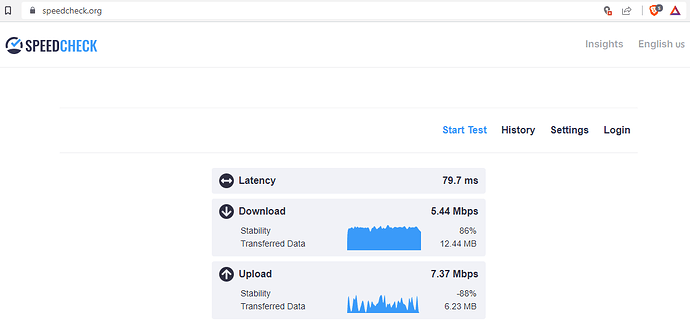
OpenVPN:
Wireguard:
No VPN:
OpenVPN:
Wireguard:
No VPN:
OpenVPN:
Wireguard:
So we can say that the internet speed on the secondary ZTE MF283+ router is around 50 Mbps without VPN, around 5 Mbps with OpenVPN and around 10 Mbps with Wireguard (twice as much as the OpenVPN).
Wireguard ended up with the........

.... eye watering 10 Mbps. Very dissapointing actually......
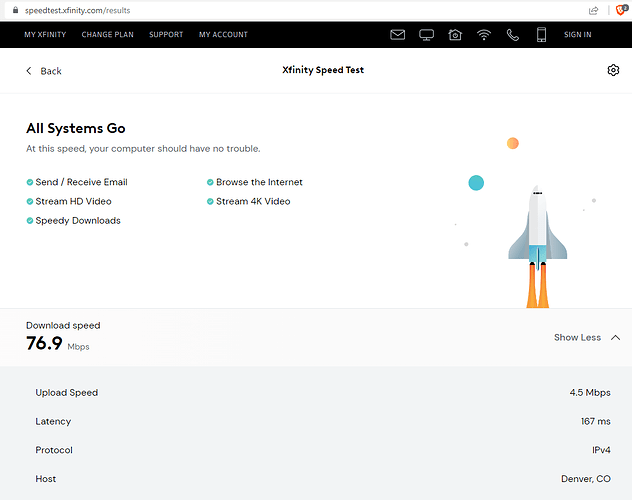
to go from 200 Mbps on the primary Huawei Echolife HG8145V5 router to ample 10 Mbps on the secondary ZTE MF283+ router.
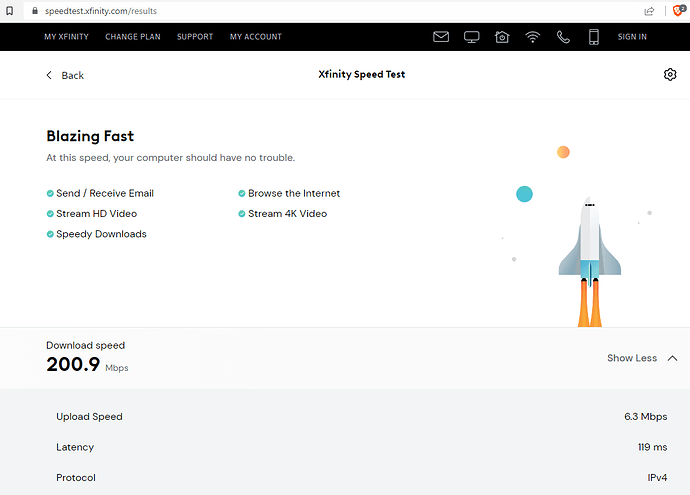
Huawei HG8145V5 primary router speeds:
I understand that having a free VPN plan comes at a cost of speed but 10 Mbps is on the very bottom side of the speed scale.
What confuses me is that the secondary ZTE MF+ router has a theoretical speed of 100-150 Mbps and the Lan ports are all 100 Mbps, but still the speed is ample 1/4 of the speed of the primary router. I believe that if the throughput was 100 Mbps that the internet speed with Wireguard would at least be some 20 Mbps. That would be much more satisfying.
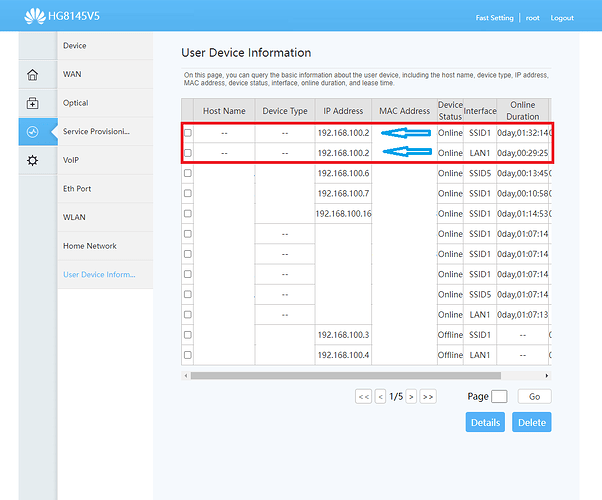
I have tried to connect to the primary router's interface through the secondary router and I have succeeded but it was a very laggy experience and when clicking on a tab it took forever to open. After a while I noticed that the secondary router was sharing the 192.168.100.2 IP address with a D-link range extender:
So I changed the static address of the WAN interface to 192.168.100.253 instead.
What happened next is that the primary router's web interface became much more snappier and much more responsive so it made me secretly hope that the internet speed would change for better too but that was a false hope as the internet speed remained the same (10 Mbps).
My last question would be.........
Is there a way to gain those 100 Mbps on the secondary router to improve the speed a little bit? Maybe through load balancing or such?
Is there any other way to get closer to those 100 Mbps throughput?
Just to be clear, I was connected to the secondary router through an Ethernet cable and the PC's NIC is a 1Gbps one, so no wi-fi connection was involved when doing the speed tests.
Any as all help would be much appreciated in answering my questions and helping me sort out these few last issues so that I can close off this topic as "Solved".