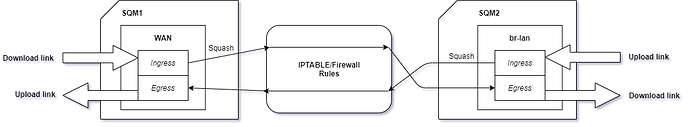
Router: TP-Link TL-WR841N/ND v8 4MB ROM with 32 MB RAM (Using as a switch)
Firmware Version: OpenWrt 18.06.5
Kernel Version: 4.9.198
I play games on both LAN & Wi-Fi. I've set up SQM with respect to ipset.
I followed this guide: Ultimate SQM settings: Layer_cake + DSCP marks
My current configs are:
dnsmasq.conf:
ipset=/igamecj.com/gcloudcs.com/qos.gcloud.qq.com/tencentgames.helpshift.com/latsens
ipset=/.googlevideo.com/youtube.com/streaming
ipset=/live.mp3quran.net/tiktokv.com/media-imdb.com/v.redd.it/last.fm/sndcdn.com/deezer.com/audio-fa.scdn.cot/vevo.com/ttvnw.net/s3.ll.dash.row.aiv-cdn.net/d25xi40x97liuc.cloudfront.net/aiv-delivery.net/nflxvideo.net/av.alarabiya.net/streaming
ipset=/.fbcdn.net/.whatsapp.net/.whatsapp.com/usrcdn
ipset=/lol.secure.dyn.riotcdn.net/lol.dyn.riotcdn.net/lol-promos.s3.amazonaws.com/.amazonaws.com/l3cdn.riotgames.com/.akamaihd.net/ucy.ac.cy/hwcdn.net/windowsupdate.com/update.microsoft.com/share.box/akamaized.net/usrcdn
ipset=/.google.com/googletagmanager.com/.googleusercontent.com/google.com/.googleapis.com/1e100.net/usrcdn
ipset=/dropbox.com/dropboxstatic.com/dropbox-dns.com/log.getdropbox.com/gs2.ww.prod.dl.playstation.net/steamcontent.com/download.qq.com/bulk
firewall.user:
#!/bin/sh
IPT="iptables"
WANIF="pppoe-wan" #wan interface
##ipset for streming sites, etc; they are bening filled by dnsmasq
ipset create streaming hash:ip
ipset create usrcdn hash:ip
ipset create bulk hash:ip
ipset create latsens hash:ip
$IPT -t mangle -N dscp_mark > /dev/null 2>&1
$IPT -t mangle -F dscp_mark
## check if POSTROUTING already exits then jumps to our tables if not, add them
$IPT -t mangle -L POSTROUTING -n | grep dscp_mark || $IPT -t mangle -A POSTROUTING -j dscp_mark
iptmark(){
$IPT -t mangle -A dscp_mark "$@"
}
## start by washing the dscp to CS0
iptmark -j DSCP --set-dscp 0
#A robust 2 rules to detect realtime traffic
# mark connections that go over 115 packets per second, not prioritized
iptmark -p udp -m hashlimit --hashlimit-name udp_high_prio --hashlimit-above 115/sec --hashlimit-burst 50 --hashlimit-mode srcip,srcport,dstip,dstport -j CONNMARK --set-mark 0x55 -m comment --comment "connmark for udp"
# unmarked UDP streams with small packets get CS6
iptmark -p udp -m connmark ! --mark 0x55 -m multiport ! --ports 22,25,53,67,68,123,143,161,162,514,5353,80,443,8080,60001 -m connbytes --connbytes 0:940 --connbytes-dir both --connbytes-mode avgpkt -j DSCP --set-dscp-class CS6 -m comment --comment "small udp connection gets CS6"
#large udp streams like video call get AF41
iptmark -p udp -m connmark ! --mark 0x55 -m multiport ! --ports 22,25,53,67,68,123,143,161,162,514,5353,80,443,8080,60001 -m connbytes --connbytes 940:1500 --connbytes-dir both --connbytes-mode avgpkt -j DSCP --set-dscp-class AF41 -m comment --comment "large udp connection gets AF41"
########
##Browsing
########
## medium priority for browsing
iptmark -p tcp -m multiport --ports 80,443,8080 -j DSCP --set-dscp-class CS3 -m comment --comment "Browsing at CS3"
##################
#TCP SYN,ACK flows
##################
#Make sure ACK,SYN packets get priority (to avoid upload speed limiting our download speed)
iptmark -p tcp --tcp-flags ALL ACK -m length --length :128 -j DSCP --set-dscp-class CS3
iptmark -p tcp --tcp-flags ALL SYN -m length --length :666 -j DSCP --set-dscp-class CS3
#Small packet is probably interactive or flow control
iptmark -m dscp ! --dscp 24 -m dscp ! --dscp 18 -m dscp ! --dscp 34 -m dscp ! --dscp 40 -m dscp ! --dscp 48 -m length --length 0:500 -j DSCP --set-dscp-class CS3
#Small packet connections: multi purpose (don't harm since not maxed out)
iptmark -m dscp ! --dscp 24 -m dscp ! --dscp 18 -m dscp ! --dscp 34 -m dscp ! --dscp 40 -m dscp ! --dscp 48 -m connbytes --connbytes 0:250 --connbytes-dir both --connbytes-mode avgpkt -j DSCP --set-dscp-class CS3
########################################
# Streaming Media (videos/audios)
########################################
#Known video streams sites like netflix
iptmark -m set --match-set streaming src,dst -j DSCP --set-dscp-class AF41 -m comment --comment "video audio stream ipset"
# some iptv provider's use this port
iptmark -p tcp -m multiport --ports 1935,9982 -j DSCP --set-dscp-class AF41 -m comment --comment "some iptv streaming service"
#known usrcdn like google or akamai
iptmark -m set --match-set usrcdn src,dst -j DSCP --set-dscp-class AF21 -m comment --comment "usrcdn ipset"
#########################################
# Background Traffic (Bulk/file transfer)
#########################################
#bulk traffic ipset, like windows udates and steam updates/downloads
iptmark -p tcp -m set --match-set bulk src,dst -j DSCP --set-dscp-class CS1 -m comment --comment "bulk traffic ipset"
iptmark -p udp -m set --match-set bulk src,dst -j DSCP --set-dscp-class CS1 -m comment --comment "bulk traffic ipset"
iptmark -p tcp -m connbytes --connbytes 350000: --connbytes-dir both --connbytes-mode bytes -m dscp --dscp-class CS0 -j DSCP --set-dscp-class CS1 -m comment --comment "Downgrade CS0 to CS1 for bulk tcp traffic"
iptmark -p tcp -m connbytes --connbytes 350000: --connbytes-dir both --connbytes-mode bytes -m dscp --dscp-class CS3 -j DSCP --set-dscp-class CS1 -m comment --comment "Downgrade CS3 to CS1 for bulk tcp traffic"
iptmark -p udp -m multiport --port 60001 -j DSCP --set-dscp-class CS1 -m comment --comment "bulk torrent port UDP"
########################################
# Latency Sensitive (gaming/voip)
########################################
##ICMP, to prioritize pings
iptmark -p icmp -j DSCP --set-dscp-class CS5 -m comment --comment "ICMP-pings"
#DNS traffic both udp and tcp
iptmark -p udp -m multiport --port 53,5353,8888 -j DSCP --set-dscp-class CS5 -m comment --comment "DNS udp"
iptmark -p tcp -m multiport --port 53,5353,8888 -j DSCP --set-dscp-class CS5 -m comment --comment "DNS tcp"
#NTP
iptmark -p udp -m multiport --port 123 -j DSCP --set-dscp-class CS6 -m comment --comment "NTP udp"
#High priority ipset
iptmark ! -p tcp -m set --match-set latsens src,dst -j DSCP --set-dscp-class CS6 -m comment --comment "latency sensitive ipset" ## set dscp tag for Latency Sensitive (latsens) ipset,udp
iptmark -p tcp -m set --match-set latsens src,dst -j DSCP --set-dscp-class CS5 -m comment --comment "latency sensitive ipset" ## set dscp tag for Latency Sensitive (latsens) ipset
#########################################
# Rainbow Six Siege
#########################################
iptmark -p udp -m multiport --port 3074,6015,10000:10099 -j DSCP --set-dscp-class EF -m comment --comment "Rainbow Six Siege UDP"
#########################################
# COD Mobile
#########################################
#iptmark -p udp -m multiport --port 88,500,3074,3544,3478:3479,4380,4500,27000-27036 -j DSCP --set-dscp-class CS6 -m comment --comment "COD"
iptmark -p udp -m multiport --port 7500:7700 -j DSCP --set-dscp-class CS7 -m comment --comment "COD Ports"
#iptmark -p udp -m iprange --src-range 124.156.50.0-124.156.70.0 -j DSCP --set-dscp-class CS7 -m comment --comment "TEST"
#iptmark -p udp -m iprange --dst-range 124.156.50.0-124.156.70.0 -j DSCP --set-dscp-class CS7 -m comment --comment "TEST"
SQM:
config queue 'eth1'
option linklayer 'none'
option debug_logging '0'
option verbosity '5'
option qdisc_advanced '1'
option egress_ecn 'NOECN'
option qdisc 'cake'
option qdisc_really_really_advanced '1'
option upload '4900'
option enabled '1'
option interface 'pppoe-wan'
option download '0'
option squash_dscp '1'
option squash_ingress '1'
option iqdisc_opts 'diffserv8 nat ack-filter datacentre'
option eqdisc_opts 'diffserv8 nat ack-filter datacentre'
option ingress_ecn 'NOECN'
option script 'layer_cake.qos'
config queue
option debug_logging '0'
option verbosity '5'
option linklayer 'none'
option qdisc 'cake'
option script 'layer_cake.qos'
option qdisc_advanced '1'
option qdisc_really_really_advanced '1'
option ingress_ecn 'NOECN'
option egress_ecn 'ECN'
option enabled '1'
option interface 'br-lan'
option download '0'
option upload '9800'
option squash_dscp '1'
option squash_ingress '1'
option iqdisc_opts 'diffserv8 nat ack-filter datacentre'
option eqdisc_opts 'diffserv8 ingress nat ack-filter datacentre'
I've passed "datacentre" string in both ingress & egress advanced options. It gives me be better & faster peek/hitreg while playing FPS games.
So I got few questions/doubts.
- How this SQM can further be optimized theoretically in terms of least latency for playing games both on LAN & Wi-Fi. (I don't mind creating two separate optimized SQM files enabled one at a time specifically for either LAN or Wi-Fi).
- Does the following mean it disables SQM & it's advance parameters completely for ingress?
Download speed (kbit/s) (ingress) set to 0 to selectively disable ingress shaping
That means I don't have to pass any advanced option string in ingress although SQM will avoid it right?
3. I put upload speed in WAN egress. For this instance only, which queue setup script is better? layer_cake.qos OR piece_of_cake.qos
4. For both PPPOE-WAN & br-lan SQM instances what should I put?
Squash DSCP on inbound packets (ingress) = ?
Ignore DSCP on ingress = ?
Explicit congestion notification (ECN) status on inbound packets (ingress) = ?
Explicit congestion notification (ECN) status on outbound packets (egress) = ?
- Could someone explain me about this field called Hard limit on ingress/egress queues how can this affect packets in gaming? Will setting these fields to 18 result in better hitreg theoretically? (Does lower value affect wireless UDP connections?)
- Does changing RTT affect UDP traffic? is 200ms RTT too much? When I set it to 200 it gives me horrible peek/hitreg lag in LAN games. Not sure about Wi-Fi.
- In the guide I mentioned, will tagging gaming packets to CS7 work for the highest packet prioritization? OR It should be CS6 only? I mean 802.11 standard does specify CS7.
Thanks in advance & Merry Christmas to everyone!