Hello. I have a device using MQTT to send data to an external server. I'd like to redirect all those traffic (to a specific external IP with port 1883) to my local MQTT server so I can use my HomeAssistant to work with it. I've tried this post but doesn't work. From tcpdump it seems traffics are redirected to the router itself. I think it is supposed to be a DNAT rule which should reside in the port forwarding section. Could anybody help me with this? Great thanks.
That's right, you need a DNAT rule to forward the traffic to the local server.
Depending on the encryption/authentication the client does with the server, this may or may not work as you expect eventually.
Thank you for the confirmation. It is a clear credential without SSL from the dump so I think it's OK to do the redirection. May I ask for a way to configure it in the luci GUI or do I have to do a iptables in the custom init script? Thanks.
It's a simple redirect, you can do it in Luci.
Could you please give me an example config? I tried several combinations but none of them worked. I should configure it in the port warding section, right?
uci add firewall redirect
uci set firewall.@redirect[-1].dest='lan'
uci set firewall.@redirect[-1].target='DNAT'
uci set firewall.@redirect[-1].name='test'
uci set firewall.@redirect[-1].src='lan'
uci set firewall.@redirect[-1].src_dport='1883'
uci set firewall.@redirect[-1].dest_ip='10.0.2.250'
uci set firewall.@redirect[-1].dest_port='1883'
uci set firewall.@redirect[-1].reflection='0'
uci commit firewall
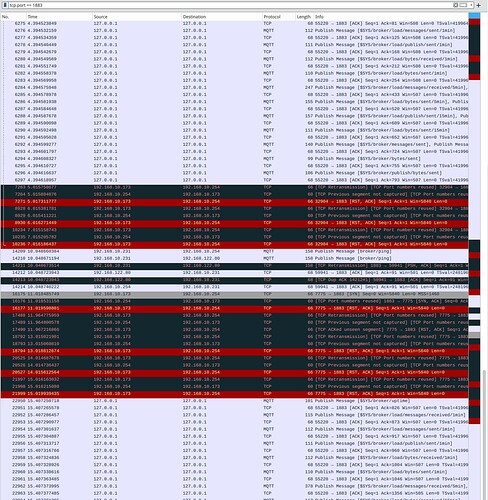
I tried with the config but seems to have some issues with TCP retransmission. The config is as follow
config redirect
option dest 'lan'
option target 'DNAT'
option name 'test'
option src 'lan'
option src_dport '1883'
option dest_port '1883'
option reflection '0'
option dest_ip '192.168.10.254'
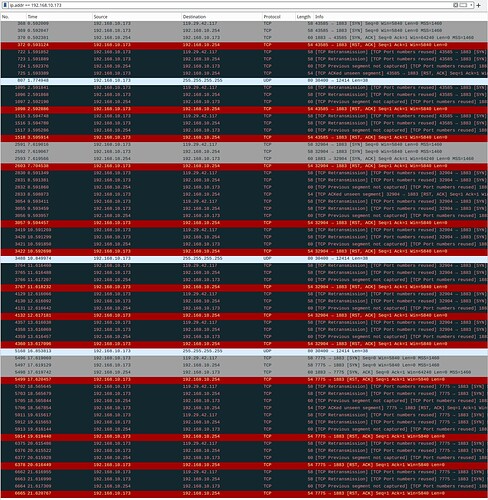
The first image is from Wireshark sshdump to the router
The second image is from my local machine running my hack mqtt server
I made sure 1883 is open to 0.0.0.0 and I used a local client to confirm the mqtt server is running
╰─$ sudo netstat -apn|grep 1883
tcp 0 0 0.0.0.0:1883 0.0.0.0:* LISTEN 237905/mosquitto
tcp 0 0 127.0.0.1:55220 127.0.0.1:1883 ESTABLISHED 235316/mqtt-explore
tcp 0 0 127.0.0.1:1883 127.0.0.1:55220 ESTABLISHED 237905/mosquitto
Any clue on how this happening? I saw from the first image the 173 (IoT MQTT pusher) tried to send packets to both 254 (my local MQTT server also my desktop) and 119.29.42.117 (remote server MQTT to be intercepted). Thanks.
Make a SNAT rule to change the source IP of the intercepted packet to the one of OpenWrt.
Since the local server and the IoT device are under the same subnet, I assume the packet will go through the openwrt internal switch directly instead of being re-routed. Should I give IoT device another subnet, or is there a way to force go through NAT rules? It does not work for now.
Both ways of different subnet or SNAT can do the trick.
In the end I went for the isolated subnet. Thank you very much for your help.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.