Sure I can
root@OpenWrt:~# uci export network
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
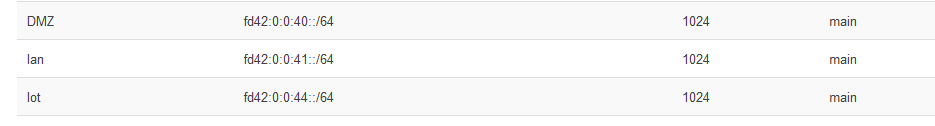
option ula_prefix 'fd42:0:0:0::/56'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6hint '41'
option ipaddr '192.168.41.1'
option ip6assign '64'
option ifname 'eth0.1 eth0.41'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
option peerdns '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '5t 1'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '6t 4'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '5t 0t'
option vid '41'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '5t 2 0t'
option vid '40'
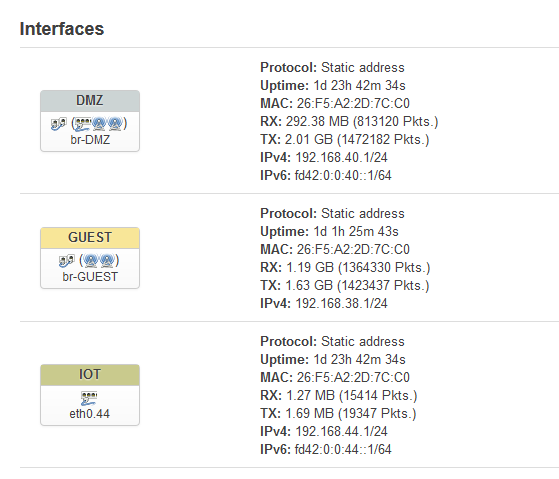
config interface 'DMZ'
option proto 'static'
option ifname 'eth0.40'
option type 'bridge'
option ipaddr '192.168.40.1'
option ip6assign '64'
option ip6hint '40'
option netmask '255.255.255.0'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '44'
option ports '5t 3'
config interface 'Iot'
option ifname 'eth0.44'
option proto 'static'
option ipaddr '192.168.44.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6hint '44'
config switch_vlan
option device 'switch0'
option vlan '6'
option ports '5t 0t'
option vid '47'
config interface 'MAIL'
option ifname 'eth0.47'
option proto 'static'
option netmask '255.255.255.0'
option ip6hint '47'
option ipaddr '192.168.47.1'
option ip6assign '64'
config interface 'GUEST'
option proto 'static'
option netmask '255.255.255.0'
option type 'bridge'
option ipaddr '192.168.38.1'
config interface 'wg0'
option proto 'wireguard'
list addresses '192.168.46.1/24'
list addresses 'fd42:0:0:46::1/64'
config wireguard_wg0
list allowed_ips '192.168.46.201/32'
list allowed_ips 'fd42:0:0:46::201/128'
config wireguard_wg0
list allowed_ips '192.168.46.202/32'
list allowed_ips 'fd42:0:0:46::202/128'
config interface 'wg1'
option proto 'wireguard'
list addresses '192.168.34.1/24'
list addresses 'fd42:0:0:34::1/64'
config wireguard_wg1
list allowed_ips '192.168.34.71/32'
list allowed_ips 'fd42:0:0:34::71/128'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
config interface 'WG2'
option proto 'wireguard'
list addresses '192.168.33.1/24'
list addresses 'fd42:0:0:33::1/64'
config wireguard_WG2
option persistent_keepalive '25'
list allowed_ips '192.168.33.91/32'
list allowed_ips '192.168.10.0/24'
option route_allowed_ips '1'
I removed lines with wireguard keys, endpoints and ports.
root@OpenWrt:~# uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option domain 'lan'
option local 'lan'
list server '127.0.0.1#5053'
option cachesize '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra_management '1'
list dhcp_option '6,192.168.40.2'
list dhcp_option '42,0.0.0.0'
list dns 'fd42:0:0:40::2'
option ndp 'hybrid'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'DMZ'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'DMZ'
list dhcp_option '42,0.0.0.0'
list dhcp_option '6,192.168.40.2'
list dns 'fd42:0:0:40::2'
option ndp 'hybrid'
option dhcpv6 'server'
option ra_management '1'
option ra 'server'
config dhcp 'VOIP'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'VOIP'
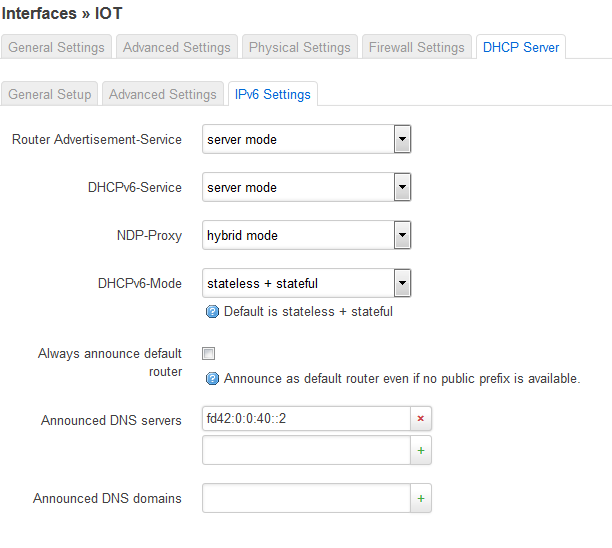
config dhcp 'Iot'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'Iot'
option dhcpv6 'server'
option ra_management '1'
list dhcp_option '6,192.168.40.2'
list dhcp_option '42,0.0.0.0'
list dns 'fd42:0:0:40::2'
option ndp 'hybrid'
option ra 'server'
config dhcp 'MAIL'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'MAIL'
option dhcpv6 'server'
option ra_management '1'
list dhcp_option '6,192.168.40.2'
list dhcp_option '42,0.0.0.0'
list dns 'fd42:0:0:40::2'
option ndp 'hybrid'
option ra 'server'
config dhcp 'GUEST'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'GUEST'
config host
option mac 'B8:27:EB:FD:42:26'
option dns '1'
option name 'pi-hole'
option hostid '2'
option duid '00010001256be1a5b827ebfd4226'
option ip '192.168.40.2'
option leasetime '12h'
config host
option mac 'DC:A6:32:04:C1:8B'
option leasetime '12h'
option dns '1'
option hostid '62'
option name 'pi-nc1'
option ip '192.168.40.62'
config host
option mac 'B8:27:EB:9F:F6:1F'
option leasetime '12h'
option dns '1'
option hostid '30'
option name 'pi-mail'
option ip '192.168.47.30'
config host
option mac 'B8:27:EB:22:20:47'
option leasetime '12h'
option dns '1'
option hostid '20'
option name 'pi-omv'
option ip '192.168.41.20'
config host
option mac '7C:2F:80:FC:B5:2E'
option name 's850a-go'
option dns '1'
option ip '192.168.44.108'
option leasetime '12h'
config host
option mac 'AC:22:0B:52:60:91'
option leasetime '12h'
option dns '1'
option hostid '22'
option name 'u-nas'
option ip '192.168.41.22'
root@OpenWrt:~# uci export firewall
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'DROP'
config zone
option network 'wg1'
option forward 'REJECT'
option name 'cXXXXXX'
option output 'ACCEPT'
option input 'REJECT'
option mtu_fix '1'
option conntrack '1'
config zone
option network 'WG2'
option forward 'REJECT'
option name 'bXXXXXX'
option output 'ACCEPT'
option input 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone
option network 'mobiles wg0'
option name 'mobiles'
option mtu_fix '1'
option forward 'REJECT'
option output 'REJECT'
option input 'REJECT'
config zone
option input 'ACCEPT'
option name 'DMZ'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'DMZ'
config forwarding
option dest 'wan'
option src 'DMZ'
config forwarding
option dest 'DMZ'
option src 'lan'
config zone
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option name 'IoT'
option network 'Iot'
config forwarding
option dest 'wan'
option src 'IoT'
config forwarding
option src 'lan'
option dest 'IoT'
config zone
option network 'MAIL'
option input 'ACCEPT'
option forward 'REJECT'
option name 'MAIL'
option output 'ACCEPT'
option conntrack '1'
config forwarding
option dest 'wan'
option src 'MAIL'
config forwarding
option dest 'MAIL'
option src 'lan'
config zone
option network 'GUEST'
option forward 'REJECT'
option name 'GUEST'
option output 'ACCEPT'
option input 'ACCEPT'
config forwarding
option dest 'wan'
option src 'GUEST'
config redirect
option dest_port '80'
option src 'wan'
option name 'nc1 (http)'
option src_dport '80'
option target 'DNAT'
option dest_ip '192.168.40.62'
option proto 'tcp'
option dest 'DMZ'
config redirect
option dest_port '443'
option src 'wan'
option name 'nc1 (https)'
option src_dport '443'
option target 'DNAT'
option dest_ip '192.168.40.62'
option proto 'tcp'
option dest 'DMZ'
config rule
option dest_port 'XXX5'
option src '*'
option name 'Wireguard for Mobiles'
option target 'ACCEPT'
option proto 'udp'
config rule
option dest_port 'XXX6'
option src 'wan'
option name 'Wireguard from cXXXXXX'
option target 'ACCEPT'
option proto 'udp'
config rule
option dest_port 'XXX7'
option src 'wan'
option name 'Wireguard from bXXXXX'
option target 'ACCEPT'
option proto 'udp'
config rule
option dest_port '53'
option proto 'tcp udp'
option dest 'wan'
option target 'ACCEPT'
option src 'DMZ'
option src_mac 'B8:27:EB:FD:42:26'
option name 'Allow authorized DNS (pi-hole)'
config rule
option dest_port '53'
option src '*'
option name 'Local DNS (pi-hole)'
option dest 'DMZ'
option target 'ACCEPT'
option proto 'tcp udp'
config rule
option dest_port '53'
option src '*'
option name 'Refuse unauthorized DNS'
option dest 'wan'
option target 'REJECT'
option proto 'tcp udp'
config rule
option dest_port '25'
option proto 'tcp'
option name 'Allow access to pi-mail'
option src_ip '192.168.40.0/21'
option dest 'MAIL'
option dest_ip '192.168.47.30'
option target 'ACCEPT'
option src '*'
config rule
option dest_port '25 80 443'
option src 'cXXXXX'
option name 'Expose pi-mail to cXXXXX'
option dest 'MAIL'
option target 'ACCEPT'
option proto 'tcp'
config rule
option dest_port '25'
option src '*'
option name 'Block unauthorized mail'
option dest 'wan'
option target 'REJECT'
option proto 'tcp'
config rule
option dest_port '80 443'
option src 'GUEST'
option name 'Internal Services for Guests'
option dest 'DMZ'
option target 'ACCEPT'
option proto 'tcp udp'
config rule
option dest_port '139 445'
option src '*'
option name 'NetBios-Filter'
option dest 'wan'
option target 'REJECT'
option proto 'tcp udp'
config rule
option dest_port '3544'
option src '*'
option dest 'wan'
option target 'REJECT'
option proto 'udp'
option name 'Teredo-Filter'
option family 'ipv4'
config forwarding
option dest 'DMZ'
option src 'mobiles'
config forwarding
option dest 'wan'
option src 'mobiles'
config forwarding
option dest 'cXXXXXX'
option src 'lan'
config forwarding
option dest 'MAIL'
option src 'mobiles'
config forwarding
option dest 'bXXXXXX'
option src 'DMZ'
config forwarding
option dest 'bXXXXXX'
option src 'lan'
config forwarding
option dest 'cXXXXXX'
option src 'MAIL'
root@OpenWrt:~# ifstatus lan
{
"up": true,
"pending": false,
"available": true,
"autostart": true,
"dynamic": false,
"uptime": 255065,
"l3_device": "br-lan",
"proto": "static",
"device": "br-lan",
"updated": [
"addresses"
],
"metric": 0,
"dns_metric": 0,
"delegation": true,
"ipv4-address": [
{
"address": "192.168.41.1",
"mask": 24
}
],
"ipv6-address": [
],
"ipv6-prefix": [
],
"ipv6-prefix-assignment": [
{
"address": "fd42:0:0:41::",
"mask": 64,
"local-address": {
"address": "fd42:0:0:41::1",
"mask": 64
}
}
],
"route": [
],
"dns-server": [
],
"dns-search": [
],
"neighbors": [
],
"inactive": {
"ipv4-address": [
],
"ipv6-address": [
],
"route": [
],
"dns-server": [
],
"dns-search": [
],
"neighbors": [
]
},
"data": {
}
}
root@OpenWrt:~# ifstatus DMZ
{
"up": true,
"pending": false,
"available": true,
"autostart": true,
"dynamic": false,
"uptime": 255119,
"l3_device": "br-DMZ",
"proto": "static",
"device": "br-DMZ",
"updated": [
"addresses"
],
"metric": 0,
"dns_metric": 0,
"delegation": true,
"ipv4-address": [
{
"address": "192.168.40.1",
"mask": 24
}
],
"ipv6-address": [
],
"ipv6-prefix": [
],
"ipv6-prefix-assignment": [
{
"address": "fd42:0:0:40::",
"mask": 64,
"local-address": {
"address": "fd42:0:0:40::1",
"mask": 64
}
}
],
"route": [
],
"dns-server": [
],
"dns-search": [
],
"neighbors": [
],
"inactive": {
"ipv4-address": [
],
"ipv6-address": [
],
"route": [
],
"dns-server": [
],
"dns-search": [
],
"neighbors": [
]
},
"data": {
}
}
 )
)