TL;DR; -- Trying to set my router up to forward UDP packets sent from internal hosts to an external ip address where the external port being targeted is in active use between an internal host and external host to the appropriate internal host. Or, to simplify the concept even more, I want NAT Reflection for any UDP port mapping between lan <-> wan whether hand-edited or dynamic.
I'm working on an implementation of the ICE protocol, and have been having trouble with the forwarding rules on my home router when testing my implementation.
The ICE protocol is one of the underlying protocols for the recent WebRTC standard that a lot of webbrowsers have been supporting.
Roughly speaking, the ICE protocol allows two computers to discover a communication path that works for bidirectional communication between them.
This is accomplished through a series of UDP messages sent between the two peers, and zero to many servers implementing the STUN or TURN protocols.
If a peer communicates with a STUN/TURN server, it'll discover the external ip address and port that was used to communicate with that server. This is useful if one of the peers is behind a NAT. Thanks to the semantics of the UDP protocol, the other peer can then send a message directly to that external ipaddress and port and the router will forward that message to the internal host appropriately, so long as the message was sent before the translation rule expired.
Anyway, I'm testing this software inside my own network, so both peers are inside the same network.
Lets say the router's internal ipaddress is 10.0.0.1, and external address is 73.0.0.0
Lets say the two hosts are 10.0.0.2 and 10.0.0.3
Host one and two both talk to some STUN server, for example the Google hosted STUN server.
They get told that their external addresses are 73.0.0.0:some port unique to each internal host
The two peers trade their internal and external addresses via some other mechanism, and then they each try to reach each other.
from 10.0.0.2 -> 10.0.0.3 works, obviously
from 10.0.0.2 -> 73.0.0.0(the port in use) results in an ICMP message saying destination unreachable.
from any external ip address -> 73.0.0.0:(the port in use) -- works exactly as expected, even if not the first external ip address to communicate on this port.
I've been able to use the firewall / port forwarding editor to set up conventional port forwards, with the nice built-in nat reflection rules, like such:
-A zone_lan_postrouting -m comment --comment "!fw3: user chain for postrouting" -j postrouting_lan_rule
-A zone_lan_postrouting -s 10.0.0.0/8 -d 10.1.0.1/32 -p tcp -m tcp --dport 22 -m comment --comment "!fw3: Mimir (reflection)" -j SNAT --to-source 10.0.0.1
-A zone_lan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_lan_prerouting -m comment --comment "!fw3: user chain for prerouting" -j prerouting_lan_rule
-A zone_lan_prerouting -s 10.0.0.0/8 -d 73.210.170.180/32 -p tcp -m tcp --dport 22 -m comment --comment "!fw3: Mimir (reflection)" -j DNAT --to-destination 10.1.0.1:22
-A zone_wan_postrouting -m comment --comment "!fw3: user chain for postrouting" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: user chain for prerouting" -j prerouting_wan_rule
-A zone_wan_prerouting -p tcp -m tcp --dport 22 -m comment --comment "!fw3: Mimir" -j DNAT --to-destination 10.1.0.1:22
How do I hook into this such that when an external UDP port is bound to an internal ipaddress/port, that packets from the LAN->external IP on the bound port gets forwarded to the internal host?
In case it's an important distinction, it's also important that the port that the forwarded packet appears to come from the external IP Address, and the port that would be used to communicate with an external server.
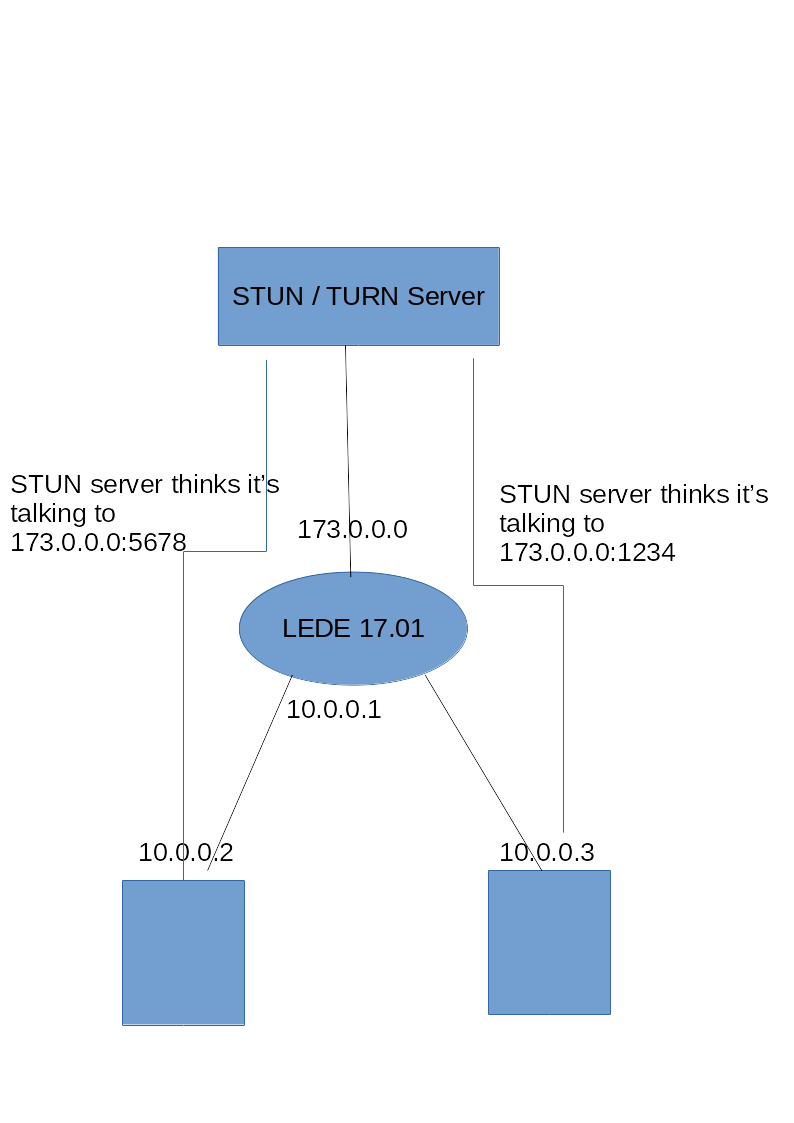
In the above diagram, I want messages from 10.0.0.2 sent to 173.0.0.0:1234 to show up at 10.0.0.3, appearing as if they were sent from 173.0.0.0:5678
My firewall configuration follows.
Note: The only two things that are different from the default (as far as I know) is that I enabled option masq '1' on the LAN zone, thinking it would enable the behavior I wanted, and I've added a rule for port 22 to the internal host Mimir.
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '547'
option dest_ip 'fe80::/10'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option dest_ip '10.1.0.1'
option dest_port '22'
option name 'Mimir'
option src_dport '22'