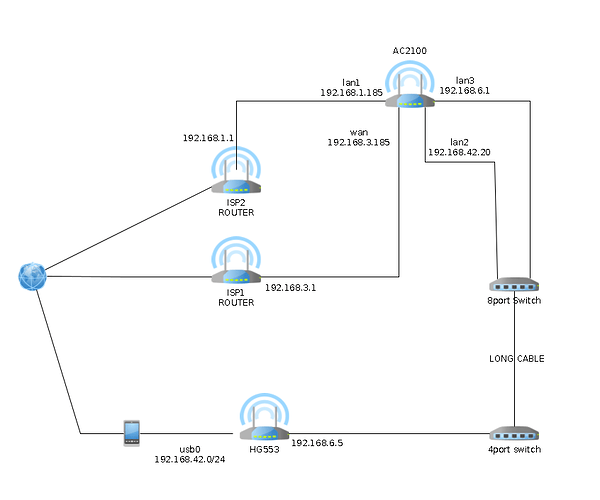
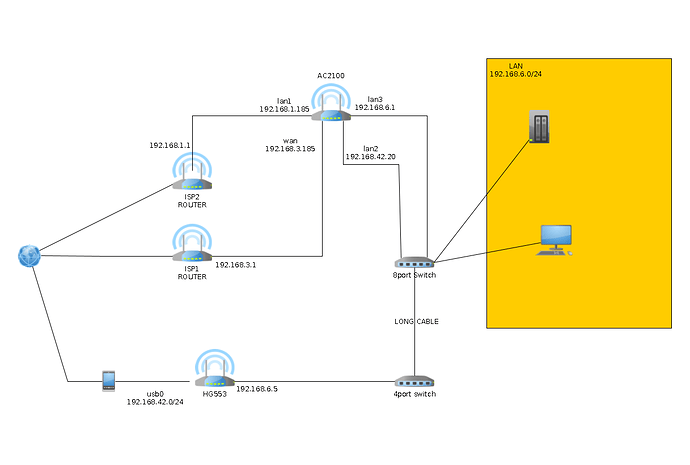
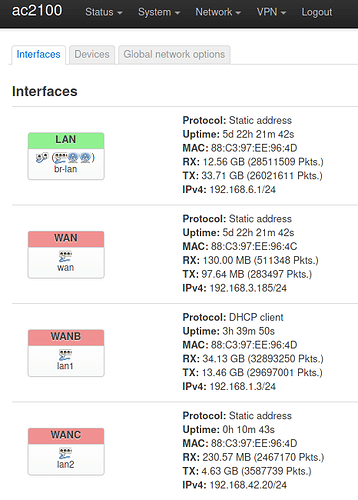
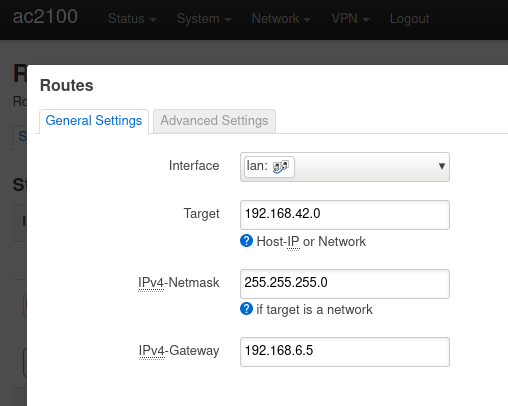
Thank you for your detailed answer.
Ok, this make sense but how do I do it "in practice"  ? I mean, I've freed a lan port to be the "wan link" but the two router are linked with a "common cable" through two switches. As you said, macvlan is the answer in this case?
? I mean, I've freed a lan port to be the "wan link" but the two router are linked with a "common cable" through two switches. As you said, macvlan is the answer in this case?
I've rolled back to my working configuration (without the new wan) and here is the redacted output of the commands (I've removed some hosts in the network block as well). So this is my "starting point"
root@ac2100:~# ubus call system board; \
> uci export network; uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; uci export mwan3; mwan3 status; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
> ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "5.4.124",
"hostname": "ac2100",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "Xiaomi Mi Router AC2100",
"board_name": "xiaomi,mi-router-ac2100",
"release": {
"distribution": "OpenWrt",
"version": "21.02.0-rc3",
"revision": "r16172-2aba3e9784",
"target": "ramips/mt7621",
"description": "OpenWrt 21.02.0-rc3 r16172-2aba3e9784"
}
}
package network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option local_source 'lan'
option mmx_mask '0x3F00'
option packet_steering '1'
option ula_prefix '****:****:****::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option stp '1'
option ipaddr '192.168.6.1'
option device 'br-lan'
config interface 'wan'
option proto 'static'
option ipaddr '192.168.3.185'
option netmask '255.255.255.0'
option gateway '192.168.3.1'
option broadcast '192.168.3.255'
option device 'wan'
option metric '40'
config interface 'wanb'
option proto 'dhcp'
option metric '20'
option hostname '*'
option device 'lan1'
option delegate '0'
config interface 'wanvpn'
option proto 'none'
option metric '30'
option device 'tun0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan3'
config route
option interface 'lan'
option target '10.9.0.0'
option netmask '255.255.255.0'
option gateway '192.168.6.111'
config device
option name 'lan2'
option macaddr '**:**:**:**:50'
config route
option interface 'lan'
option target '192.168.42.0'
option netmask '255.255.255.0'
option gateway '192.168.6.5'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
list server '208.67.222.222'
list server '208.67.220.220'
list server '8.8.8.8'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,192.168.6.111,192.168.6.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'fastgate'
option dns '1'
option mac '**:**:**:**:CF'
option ip '192.168.6.254'
config host
option dns '1'
option mac '**:**:**:**:B3'
option ip '192.168.6.111'
option name 'msi'
config domain
option name 'tplink'
option ip '192.168.6.3'
config host
option name 'tplink'
option dns '1'
option mac '**:**:**:**:DA'
option ip '192.168.6.3'
config host
option ip '192.168.6.226'
option mac '**:**:**:**:F5'
option name 'nas'
option dns '1'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option family 'ipv4'
list network 'wan'
list network 'wanb'
list network 'WAND'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '443'
option dest_ip '192.168.6.111'
option dest_port '443'
option name 'VPN/Home assistant'
list src_mac '**:**:**:**:D0'
list src_mac '**:**:**:**:F0'
list src_mac '**:**:**:**:CF'
list src_mac '**:**:**:**:10'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '4277'
option dest_ip '192.168.6.111'
option dest_port '4277'
option name 'Bitwarden'
list src_mac '**:**:**:**:F0'
list src_mac '**:**:**:**:D0'
list src_mac '**:**:**:**:CF'
list src_mac '**:**:**:**:10'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp udp'
option src_dport '41554'
option dest_ip '192.168.6.170'
option dest_port '554'
option name 'RSTPCAM'
list src_mac '**:**:**:**:F0'
list src_mac '**:**:**:**:D0'
list src_mac '**:**:**:**:CF'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '4180'
option dest_ip '192.168.6.170'
option dest_port '8080'
option name 'HTTP_CAM'
list src_mac '**:**:**:**:F0'
list src_mac '**:**:**:**:D0'
list src_mac '**:**:**:**:CF'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '80'
option dest_ip '192.168.6.111'
option dest_port '80'
option name 'letsencrypt'
list src_mac '**:**:**:**:F0'
list src_mac '**:**:**:**:D0'
list src_mac '**:**:**:**:CF'
list src_mac '**:**:**:**:10'
config zone
option name 'vpnfirewall'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'vpntun'
list network 'wan_vpn'
list network 'wanvpn'
config forwarding
option src 'lan'
option dest 'vpnfirewall'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
package mwan3
config rule 'pi4'
option family 'ipv4'
option src_ip '192.168.6.247'
option proto 'all'
option sticky '1'
option use_policy 'wanvpn_only'
config rule 'work'
option proto 'all'
option sticky '1'
option use_policy 'wanb_only'
option src_ip '192.168.6.150'
config rule 'https'
option sticky '1'
option dest_port '443'
option proto 'tcp'
option family 'ipv4'
option use_policy 'wanb_only'
config rule 'default_rule_v4'
option dest_ip '0.0.0.0/0'
option family 'ipv4'
option proto 'all'
option sticky '0'
option use_policy 'wanb_only'
config rule 'nas'
option src_ip '192.168.6.226'
option proto 'all'
option sticky '0'
option use_policy 'wanb_only'
config policy 'wan_only'
list use_member 'wan_m1_w3'
option last_resort 'unreachable'
config policy 'wanb_only'
list use_member 'wanb_m1_w2'
option last_resort 'unreachable'
config policy 'wanvpn_only'
list use_member 'wanvpn_m1_w1'
option last_resort 'unreachable'
config policy 'balanced'
list use_member 'wan_m1_w3'
list use_member 'wanb_m1_w2'
option last_resort 'unreachable'
config policy 'wan_wanb'
list use_member 'wan_m1_w3'
list use_member 'wanb_m2_w2'
option last_resort 'unreachable'
config policy 'wanb_wan'
list use_member 'wan_m2_w3'
list use_member 'wanb_m1_w2'
option last_resort 'unreachable'
config globals 'globals'
option local_source 'lan'
option mmx_mask '0x3F00'
config interface 'wan'
option family 'ipv4'
option initial_state 'online'
option track_method 'ping'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '4'
option interval '10'
option failure_interval '5'
option recovery_interval '5'
option down '5'
option up '5'
list track_ip '8.8.8.8'
option reliability '1'
option enabled '1'
list flush_conntrack 'connected'
list flush_conntrack 'disconnected'
config interface 'wanb'
option family 'ipv4'
option reliability '1'
option initial_state 'online'
option track_method 'ping'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '4'
option interval '10'
option failure_interval '5'
option recovery_interval '5'
option down '5'
option up '5'
option enabled '1'
list track_ip '192.168.1.1'
config member 'wan_m1_w3'
option interface 'wan'
option metric '1'
option weight '3'
config member 'wan_m2_w3'
option interface 'wan'
option metric '2'
option weight '3'
config member 'wanb_m1_w2'
option interface 'wanb'
option metric '1'
option weight '2'
config member 'wanb_m2_w2'
option interface 'wanb'
option metric '2'
option weight '2'
config interface 'wanvpn'
option enabled '1'
option initial_state 'online'
option family 'ipv4'
option track_method 'ping'
option reliability '1'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '4'
option interval '10'
option failure_interval '5'
option recovery_interval '5'
option down '5'
option up '5'
config member 'wanvpn_m1_w1'
option interface 'wanvpn'
option metric '1'
option weight '1'
config interface 'wand'
option initial_state 'online'
option family 'ipv4'
option track_method 'ping'
option reliability '1'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '4'
option interval '10'
option failure_interval '5'
option recovery_interval '5'
option down '5'
option up '5'
list track_ip '192.168.42.129'
option enabled '0'
config member 'wand_m1_w2'
option interface 'wand'
option metric '1'
option weight '2'
config policy 'wand_only'
list use_member 'wand_m1_w2'
option last_resort 'default'
Interface status:
interface wan is online 16h:12m:14s, uptime 16h:21m:27s and tracking is active
interface wanb is online 16h:09m:54s, uptime 16h:10m:11s and tracking is active
interface wanvpn is online 00h:00m:00s, uptime 16h:10m:01s and tracking is not enabled
interface wand is offline and tracking is down
Current ipv4 policies:
balanced:
wanb (40%)
wan (60%)
wan_only:
wan (100%)
wan_wanb:
wan (100%)
wanb_only:
wanb (100%)
wanb_wan:
wanb (100%)
wand_only:
default
wanvpn_only:
wanvpn (100%)
Current ipv6 policies:
balanced:
unreachable
wan_only:
unreachable
wan_wanb:
unreachable
wanb_only:
unreachable
wanb_wan:
unreachable
wand_only:
default
wanvpn_only:
unreachable
Directly connected ipv4 networks:
192.168.3.0/24
224.0.0.0/3
127.0.0.0/8
192.168.42.0/24
10.9.0.0/24
192.168.6.0/24
192.168.1.0/24
10.8.3.0/24
Directly connected ipv6 networks:
fe80::/64
Active ipv4 user rules:
222K 19M S pi4 all -- * * 192.168.6.247 0.0.0.0/0
147 7644 S work all -- * * 192.168.6.150 0.0.0.0/0
2475 563K - wanb_only all -- * * 192.168.6.122 0.0.0.0/0
0 0 - wanb_only all -- * * 192.168.6.123 0.0.0.0/0
4045 250K S https tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 443
45221 5616K - wanb_only all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 - wanb_only all -- * * 192.168.6.157 0.0.0.0/0
0 0 - wanb_only all -- * * 192.168.6.226 0.0.0.0/0
Active ipv6 user rules:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: wan@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.3.185/24 brd 192.168.3.255 scope global wan
valid_lft forever preferred_lft forever
4: lan1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.3/24 brd 192.168.1.255 scope global lan1
valid_lft forever preferred_lft forever
9: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.6.1/24 brd 192.168.6.255 scope global br-lan
valid_lft forever preferred_lft forever
15: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 500
inet 10.8.3.4/24 scope global tun0
valid_lft forever preferred_lft forever
default via 192.168.3.1 dev wan table 1 proto static metric 40
10.9.0.0/24 via 192.168.6.111 dev br-lan table 1 proto static
192.168.3.0/24 dev wan table 1 proto static scope link metric 40
192.168.6.0/24 dev br-lan table 1 proto kernel scope link src 192.168.6.1
192.168.42.0/24 via 192.168.6.5 dev br-lan table 1 proto static
default via 192.168.1.1 dev lan1 table 2 proto static metric 10
default via 192.168.1.1 dev lan1 table 2 proto static src 192.168.1.3 metric 20
10.9.0.0/24 via 192.168.6.111 dev br-lan table 2 proto static
192.168.1.0/24 dev lan1 table 2 proto static scope link metric 20
192.168.6.0/24 dev br-lan table 2 proto kernel scope link src 192.168.6.1
192.168.42.0/24 via 192.168.6.5 dev br-lan table 2 proto static
default via 10.8.3.1 dev tun0 table 3 metric 20
10.8.3.0/24 dev tun0 table 3 proto kernel scope link src 10.8.3.4
10.9.0.0/24 via 192.168.6.111 dev br-lan table 3 proto static
192.168.6.0/24 dev br-lan table 3 proto kernel scope link src 192.168.6.1
192.168.42.0/24 via 192.168.6.5 dev br-lan table 3 proto static
default via 192.168.1.1 dev lan1 proto static metric 10
default via 10.8.3.1 dev tun0 metric 20
default via 192.168.3.1 dev wan proto static metric 40
10.8.3.0/24 dev tun0 proto kernel scope link src 10.8.3.4
10.9.0.0/24 via 192.168.6.111 dev br-lan proto static
192.168.1.0/24 dev lan1 proto static scope link metric 20
192.168.3.0/24 dev wan proto static scope link metric 40
192.168.6.0/24 dev br-lan proto kernel scope link src 192.168.6.1
192.168.42.0/24 via 192.168.6.5 dev br-lan proto static
broadcast 10.8.3.0 dev tun0 table local proto kernel scope link src 10.8.3.4
local 10.8.3.4 dev tun0 table local proto kernel scope host src 10.8.3.4
broadcast 10.8.3.255 dev tun0 table local proto kernel scope link src 10.8.3.4
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev lan1 table local proto kernel scope link src 192.168.1.3
local 192.168.1.3 dev lan1 table local proto kernel scope host src 192.168.1.3
broadcast 192.168.1.255 dev lan1 table local proto kernel scope link src 192.168.1.3
broadcast 192.168.3.0 dev wan table local proto kernel scope link src 192.168.3.185
local 192.168.3.185 dev wan table local proto kernel scope host src 192.168.3.185
broadcast 192.168.3.255 dev wan table local proto kernel scope link src 192.168.3.185
broadcast 192.168.6.0 dev br-lan table local proto kernel scope link src 192.168.6.1
local 192.168.6.1 dev br-lan table local proto kernel scope host src 192.168.6.1
broadcast 192.168.6.255 dev br-lan table local proto kernel scope link src 192.168.6.1
0: from all lookup local
1001: from all iif wan lookup 1
1002: from all iif lan1 lookup 2
1003: from all iif tun0 lookup 3
2001: from all fwmark 0x100/0x3f00 lookup 1
2002: from all fwmark 0x200/0x3f00 lookup 2
2003: from all fwmark 0x300/0x3f00 lookup 3
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
3001: from all fwmark 0x100/0x3f00 unreachable
3002: from all fwmark 0x200/0x3f00 unreachable
3003: from all fwmark 0x300/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Jun 14 00:02 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 47 Jun 30 18:53 /tmp/resolv.conf
-rw-r--r-- 1 root root 74 Jun 30 19:05 /tmp/resolv.conf.d/resolv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 74 Jun 30 19:05 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wanb
nameserver 192.168.1.1
nameserver 8.8.8.8
search station
 )? I have the usb port on another router (but I want to use that specific router for other reason also), not the main one with mwan3 (AC2100 in the picture).
)? I have the usb port on another router (but I want to use that specific router for other reason also), not the main one with mwan3 (AC2100 in the picture).