Hi everyone,
since five days I'm pretty much stuck with a couple of problems. My goal is to add a second gateway to my local network that features VPN encryption via a hoster like Cyberghost, ProtonVPN, ExpressVPN or anyone else.
For most clients I want to keep the standard gateway as i don't need the encryption for my TV and most smarthome components for example. For my PCs i want to change the gateway manually so their traffic is being encrypted.
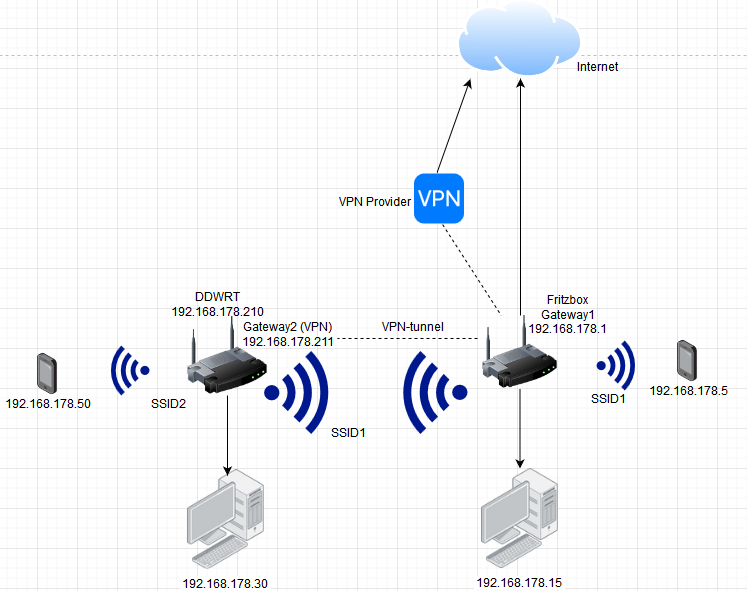
Currently my network consists of a Fritzbox(Gateway1) and an Archer C7 running OpenWrts latest RC 19.07.0. The networks of both devices are connected wireless via relayd. All client IPs are part of the same subnet. Nothing special so far.
That is what i would like to achive. The secondary gateway is running on OpenWrt and accessing the Internet via Fritzbox and VPN hoster.
The problems start with openvpn. The *.ovpn config seems to run fine. I checked by using it with a openvpn client for windows. Testing the config on OpenWrt returns "Initialization Sequence Completed". After uploading the *.ovpn (love the new ovpn upload functionality btw), enabling and activating the instance it shows up as active but when trying to ping any IP from tun0 (local or internet) I won't get any response.
root@OpenWrt:~# ifconfig tun0
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.12.0.78 P-t-P:10.12.0.77 Mask:255.255.255.255
inet6 addr: fe80::29ab:255:5df1:ba8a/64 Scope:Link
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:1 errors:0 dropped:0 overruns:0 frame:0
TX packets:25 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:105 (105.0 B) TX bytes:1864 (1.8 KiB)
root@OpenWrt:~# traceroute -i tun0 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 38 byte packets
1 10.12.0.1 (10.12.0.1) 1046.900 ms 58.149 ms 57.790 ms
2 * * *
There are many howtos available that all follow the same basic steps and claim tun0 would be able to ping any address at this point. The only difference I see is most openvpn applications are running on a device, which is directly connected to internet. What am I missing out here?
Firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wwan LANrelayd BRIDGErelayd tun0'
config include
option path '/etc/firewall.user'
config zone
option network 'vpn tun0'
option name 'vpn'
option mtu_fix '1'
option masq '1'
option output 'ACCEPT'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option dest 'vpn'
option src 'lan'
Interfaces
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb2:2f58:2cb6::/48'
config interface 'lan'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'wan_dev'
option name 'eth0.2'
option macaddr 'b0:be:76:77:a6:0c'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 2 3 4 5'
config interface 'wwan'
option proto 'dhcp'
config interface 'LANrelayd'
option proto 'static'
option ifname 'eth0.2'
option type 'bridge'
config interface 'BRIDGErelayd'
option proto 'relay'
list network 'LANrelayd'
list network 'wwan'
config interface 'tun0'
option ifname 'tun0'
option proto 'none'
Thanks for reading this far. I would really appreciate any kind of help.