Hey everyone,
I have been working on this for a while. I wanted to create a wireguard tunnel to nordvpn servers. I will provide two ways to achieve the result. Option number two is optimal because I am able to create a private wireguard server that allows me to connect to the local subnet that is behind nordvpn. This will allow me to create a subnet that is protected by nordvpn. I can then access this subnet through my own private wireguard server anywhere in the world. So here is the process:
Setup (The setup will be the same for both option 1 and option 2)
- Install packages
sudo apt install wireguard curl jq net-tools
- Install nordvpn on linux machine
sh <(curl -sSf https://downloads.nordcdn.com/apps/linux/install.sh)
- Login into nordvpn
sudo nordvpn login
- Change connection protocol to nordlynx
sudo nordvpn set technology nordlynx
- connect to your preferred server
`sudo nordvpn c nl #to connect Nederland as an example`
- Obtain ip address of nordlynx interface (should be similar to 10.5.0.2)
ifconfig nordlynx
- Obtain nordlynx configuration public-key and private-key
sudo wg show nordlynx private-key
sudo wg show nordlynx public-key
- Enter this command to obtain the peers (nordvpn servers) public key
curl -s "https://api.nordvpn.com/v1/servers/recommendations?&filters\[servers_technologies\]\[identifier\]=wireguard_udp&limit=1"|jq -r '.[]|.hostname, .station, (.locations|.[]|.country|.city.name), (.locations|.[]|.country|.name), (.technologies|.[].metadata|.[].value), .load'
- Install these software packages on Openwrt
kmod-wireguard luci-app-wireguard luci-proto-wireguard wireguard wireguard-tools
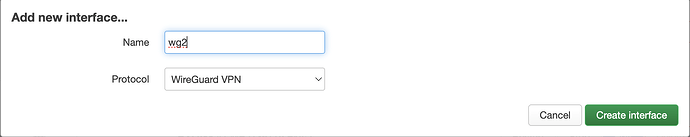
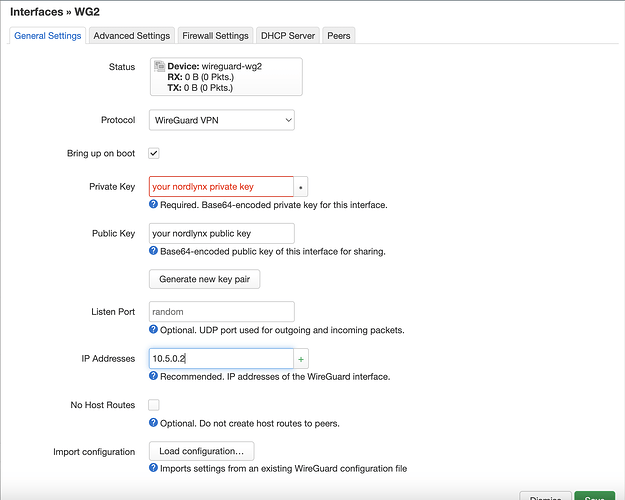
- Create network interface that connects to nordlynx wireguard server
- Add your nordlynx public and private key
- Allowed ip (10.5.0.2 - found earlier)
- Route allowed ips checked
- Persistent keep alive 25s
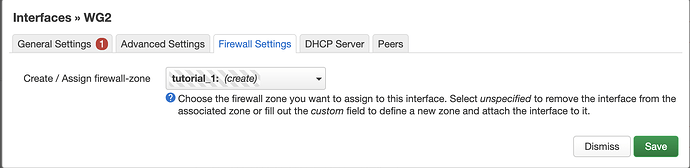
- Create a firewall zone to assign the interface to
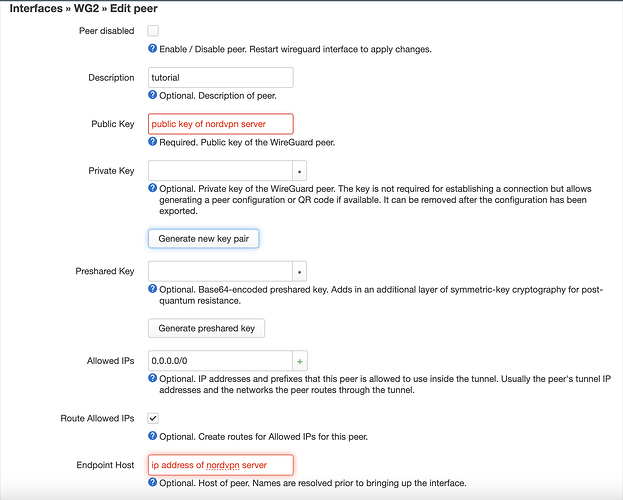
- Create peer with the public key of the nordvpn server you connected to and set allowed ips to 0.0.0.0/0
- Set endpoint host to external ip address of nordvpn server
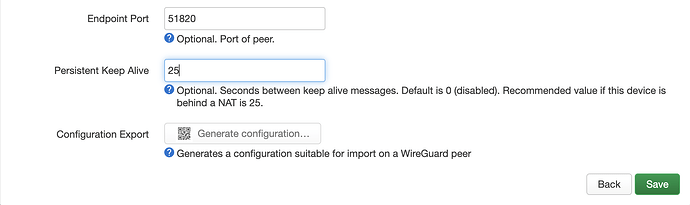
- Set endpoint port to 51820
- Persistent keep alive to 25 seconds
- Create a new interface with static ip address range
- Create a new firewall zone to attach the new interface to
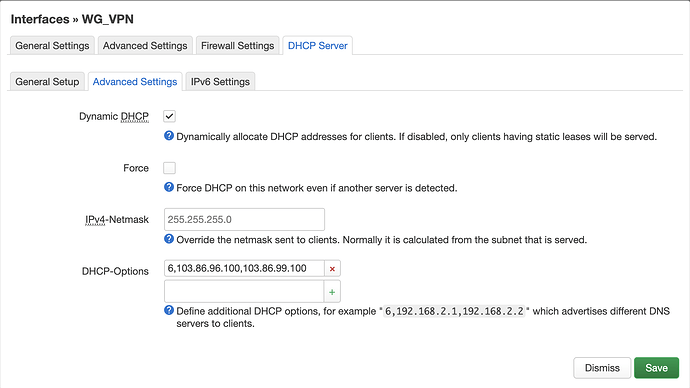
- Create advanced DHCP settings to make sure DNS is through nordvpn
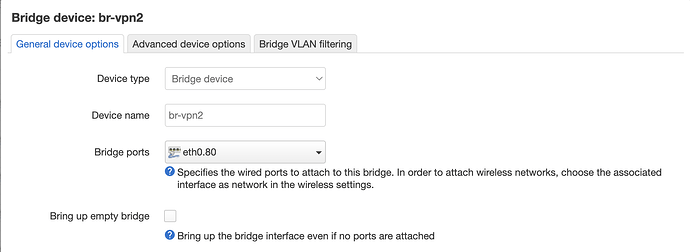
- Create device that is attached to a vlan or ethernet port and then assign this device to your subnets interface
*I will now propose two options on how to route traffic from the interface with the static ip address (i.e. 10.20.40.1/24) to the wireguard vpn tunnel. Option 1 is used in case option 2 does not work. Option 1 forces the traffic from interface subnet 10.20.40.1/24 to be routed through the tunnel. Correct firewall rules should allow the traffic to pass through the zones but it does not always work. I think option 1 did not work with similar firewall settings becasue I did not click "route allowed ips" in the peers section of the wireguard interface.
Option 1
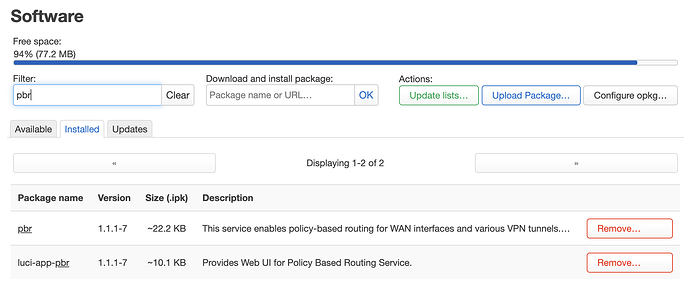
- Install pbr and luci-app-pbr in openwrt packages
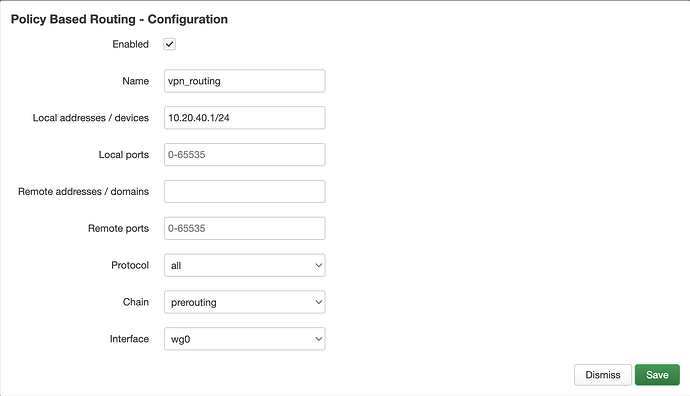
- Create a new policy that routes your static ip address 10.20.40.1/24 to wg0 (wireguard tunnel)
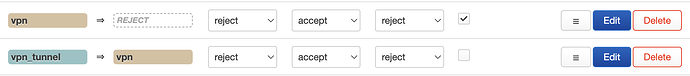
- Create firewall settings that reflects below:
- Enjoy traffic through the wireguard tunnel
Option 2
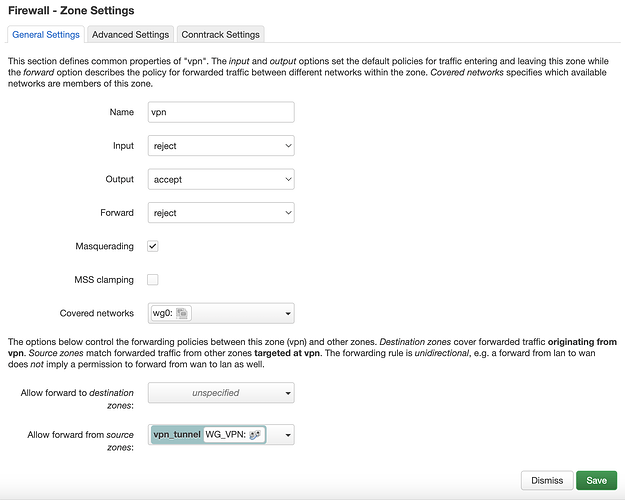
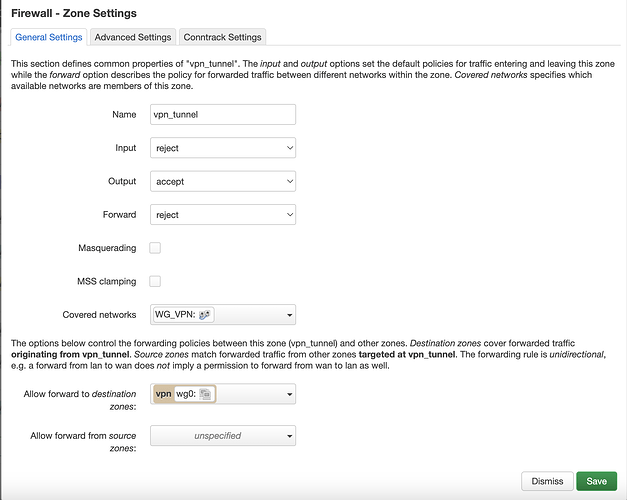
- The firewall zone with the subnet interface should have 'covered networks' as the interface. It should then forward to the wireguard tunnel destination zone
- The firewall zone should have allow forward from source zone (subnet interface). Then it should not have to forward anywhere else. Covered networks is the wireguard tunnel interface. Masquerading and MSS clamping should be enabled.
Please provide revisions in the comments
Sources:
- https://gist.github.com/bluewalk/7b3db071c488c82c604baf76a42eaad3 (how to obtain wireguard credentials)
- [Instruction] Config NordVPN wireguard (Nordlynx) on OpenWrt (configure nordvpn wireguard on openwrt - my tutorial goes into more depth on how to setup the wireguard rules)