Greetings,
posting for the first time here but I've been reading around for a long time. I am going to try to list as much details from my build and problems along the way as possible, as it might help newbies like me.
Finally got around to try and build a replacement for my tp-link AC1750 that's been running on openwrt for a couple of years now.
The replacement as the title suggests is a Lenovo m920q mini pc (i5-8500T + 8GB RAM) with a pcie 4port 2.5Gig (intel) expansion cart from aliexpress.
So far so good, managed to install 23.05.02 on the nvme and expand the disk space.
I want to tackle the problems one by one and hopefully this will generate a guide on for other enthusiasts.
First objective now is to set up a second network for my two IP PoE cameras. How should I set this up so that the cameras can only be accessed from my NAS/LAN using a VPN to tunnel back in when I am not home.
So far i wend to network>interfaces and created a new interface with a static address (that is not on the same subnet as my lan, i don't know if that right or not?). Under device i set up eth2 (this is port 2 of my 4port nic)
Haven't set up any DNS as the cameras aren't going to go out to the internet (hope that the right choice)
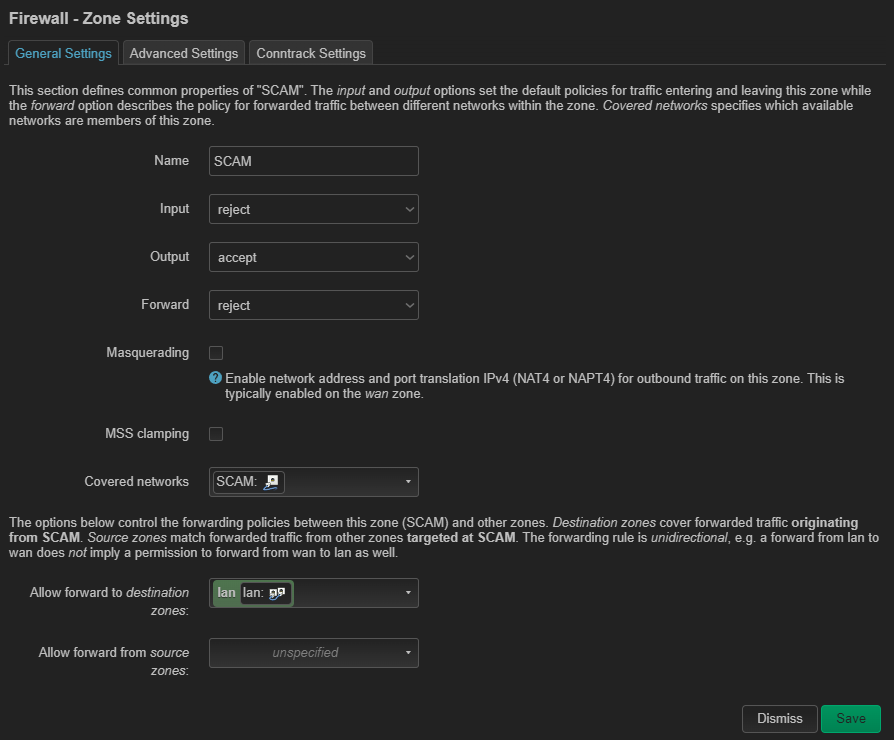
I created a custom firewall:
For covered devices I have selected eth2.
And since there are only two devices and the unmanaged PoE switch that are going to return to this port (not even sure if the switch needs an IP 'prolly not') I set up the DHCP server as start=100/limit=103.
Now the plan is that in this port (eth2) i will connect an unmanaged PoE switch that will power two PoE IP cameras.
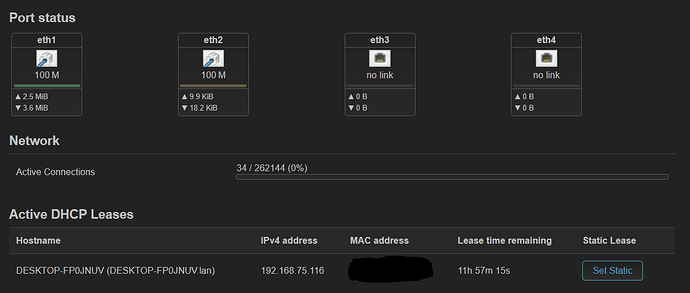
After set up I tried connecting the switch to the port and one camera to the switch but nothing happened.
So I suppose I am doing something wrong, but not sure what?
Also tried to plug the PoE switch with the camera to my lan and it immediately got recognized by my router as it issued an IP for the camera.
Any idea what am I doing wrong with setting up this camera interface?