This post is a follow up of a previous post (btw now I'm using upstream openwrt).
To go around the 802.11 lack of bridging capabilities, relayd can be used to masquerade the MAC addresses between the interfaces. It acts essentially as a layer 2 NAT: devices on the ethernet side will see every device on the wifi side as having the router's mac, and vice versa.
I'm now trying to get a simpler, full layer 2 forwarder over wireless, i.e. a single-pair bridge where the dst MAC of incoming LAN frames is replaced with the remote device's MAC, and the src MAC of outgoing MAC frames is replaced with the forwarder's MAC.
We must also make some exceptions to allow the forwarder device to be individually addressable; In a real use case, the forwarder can be use to bring a (single) remote device "into the LAN" over wifi, down to layer 2. Layer 2 access is commonly required for network monitoring purposes.
I think I should be able to achieve this with ebtables:
ebtables -t nat -A POSTROUTING -o phy0-sta0 -j snat -p IPv4 --ip-source <device ip> --snat-arp --to-source <forwarder mac> --snat-target ACCEPT
ebtables -t nat -A POSTROUTING -o phy0-sta0 -j snat -p ARP --arp-ip-src <device ip> --snat-arp --to-source <forwarder mac> --snat-target ACCEPT
ebtables -t nat -A PREROUTING -i phy0-sta0 -j dnat -p IPv4 --ip-dst <device ip> --to-dst <device mac> --dnat-target ACCEPT
ebtables -t nat -A PREROUTING -i phy0-sta0 -j dnat -p ARP --arp-ip-dst <device ip> --to-dst <device mac> --dnat-target ACCEPT
This doesn't work. Neither device sees devices across the forwarder.
I wonder if there's some fundamental reason of why this is not working, or other OpenWRT (routing) components interfering in what is basically switching trickery.
I've also toyed around setting up wds as shown here but I suspect the hardware is just not there.
I've also tried setting up a gretap tunnel between the forwarder and another scavenged openWRT device "B" to cross the wifi connection. The device B does the bridging over ethernet (but it cannot do the remote tunneling, it uses an outdated customized build).
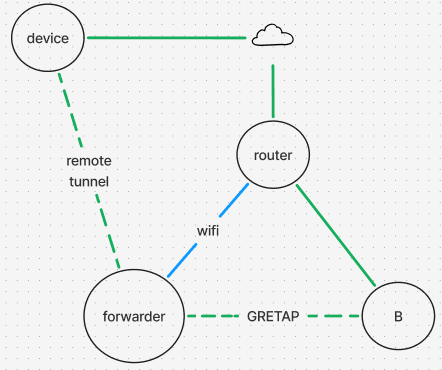
Devices across the forwarder can ping each other and see each other's MAC, but iperf -uR reports traffic only in one direction. Strangely, the device and the forwarder can't ping eachother.
Note that the device, forwarder, and B are all in the same network, but the forwarder's remote tunnel port has an IP of another network. This is analogous to a relayd setup:
