I currently have a setup with Ethersoft VPN which have been running for quite a few years for a bit of special usecase where I need a L2 tunnel. The PCs I run this on are getting quite old, and is also a bit unpractical in terms of space and heat.
There was a new release now of Softether VPN, but in terms of at least official releases, seems like the previous release was in 2023, so maybe also a bit worries about the development status of that project.
The security for traffic "in flight" is not that important - performance is. On the current setup I'm able to get 600-700 Mbps throughput over the VPN on my 750 Mbps line (the "server side" is 1Gbps. It would be "just internet traffic" that goes over this tunnel, but of course, the authentication security needs to be OK. Currently just running MD5 on the SoftEther VPN-setup to get the performance that I need for this (don't think there was an option to just completely run a tunnel).
Today the setup run with a old Core i7-2600 with two NICs on the "server side" and a i7-3770 on the "client side" here at home. The plan was to use two MTK MT7986 4-core A53 2GHz routers to replace this setup.
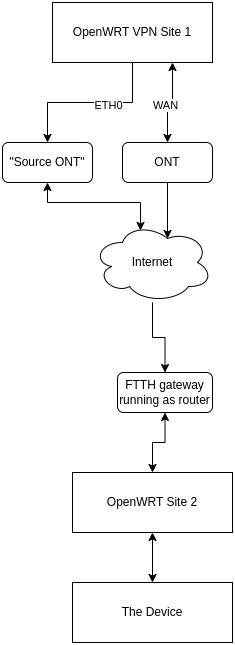
Illustration:
The goal here is that "The Device" will get a public IP-address (4&6) from "Source ONT", acting as the "The Device" was directly connected to this ONT. The "Open WRT site 2" device will be behind my ISPs FTTH-gateway.
So the VPN/tunnel setup needs to bridge an interface on the devices to the tunnel directly.
So: Recommended tunnel/VPN setup and thoughts about if the MT7986-devices will be powerfull enough to give equal performance as I have today?