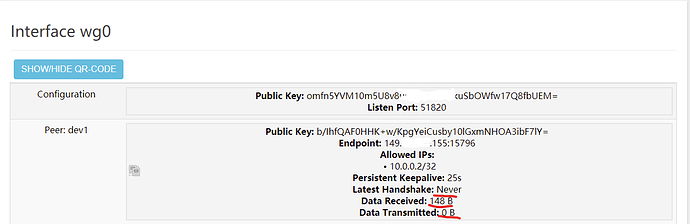
Hello, I have read almost all topics regarding WireGuard and the problem of no handshake but couldn't resolve my own problem, so I decided to start a a new one. So my device is Xiaomi Mi Router 4A Gigabit, flashed with OpenWrt 19.07.7 r11306-c4a6851c72 / LuCI openwrt-19.07 branch git-21.044.30835-34e0d65. I have attached my network, firewall and peer configs. I have tried to connect from different types of internet - LTE and Broadband - but there is no difference. I can see that the peer is connecting to the router but there is no handshake or data transmitted from the router to the peer, according to the WireGuard status page:
I used tcpdump to monitor the traffic and saw that my peer is sending data to the router but there is no reply. I have tried to create new keys multiple times with no changes. As a last resort I used www.wireguardconfig.com to automatically create the private and public keys, so I cannot mess anything up. My port forwarding rule is the same as the 2-3 tutorials I have found. I have the UPnP service installed and tried disabling it, because I read that it can interfere, but that did not make a difference.
I cannot think of a reason why my setup shouldn't work.
network config
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6f:5c13:28d9::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '64:66:b3:43:c5:3b'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
config interface 'wg0'
option proto 'wireguard'
option private_key 'cDpWd75TIkml4---------------PMKVXqbWg/tZcVQ='
option listen_port '51820'
list addresses '10.0.0.1/24'
option mtu '1280'
config wireguard_wg0
option route_allowed_ips '1'
option public_key 'b/IhfQAF0HHK---------------0lGxmNHOA3ibF7lY='
option description 'dev1'
list allowed_ips '10.0.0.2/32'
option persistent_keepalive '25'
config wireguard_wg0
option public_key 'qYijWpaGtEXhF---------------jYv99UzVV/1ZOXU='
option description 'dev2'
list allowed_ips '10.0.0.3/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
firewall config
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg0'
option masq '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config redirect
option dest_port '51820'
option src 'wan'
option name 'Allow-WireGuard'
option src_dport '51820'
option target 'DNAT'
option dest_ip '192.168.1.1'
option dest 'lan'
list proto 'udp'
wireguard peer config
[Interface]
Address = 10.0.0.2/24
PrivateKey = 6Knl5TIhKe4---------------4nD0YM7UIMWKWYmmQ=
[Peer]
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = *****.duckdns.org:51820
PersistentKeepalive = 25
PublicKey = omfn5YVM10m---------------kuSbOWfw17Q8fbUEM=