Hi,
I've been building a home network for over a year, everything has been going more or less smoothly so far. I went through laying ducts and cables, choosing a rack cabinet, configuring switches, router and APs. I don't know how, but somehow I managed to put it all together.
Schematic diagram of the network:
LTE#1 LTE#2 (2x ZTE MC801A LTE in bridge mode)
| |
| |
Switch #3: (Netgear GS308T /Openwrt/)
|
|
| Router: (HP T430 /OpenWrt/ + UE300 USB dongle)
| |
| | PC1 PC2
| | | |
| | | |
Switch #1: (TP-Link SX3008F)
| |
| |
LAG1 (LACP) LAG1
| |
| |
Switch #2: (TP-Link SX3008F)
| | | |
| | | |
AP1 AP2 AP3 AP4 (All Dumb AP + FT: Redmi AX6000, Xiaomi AX3200 /Openwrt/)
|
|
Print Server (Nexx WT3020 /Openwrt/)
Cables: SM fiber, SFP and SFP+ modules + several TP-Link MC220L media converters to connect everything together.
VLANs:
ID 2 = Management
ID 3 = Home
ID 5 = IoT
ID 7 = Guest
ID 51 = LTE ISP #1
ID 52 = LTE ISP #2
ID 53 = LTE ISP #3 (unused)
ID 54 = LTE ISP #4 (unused)
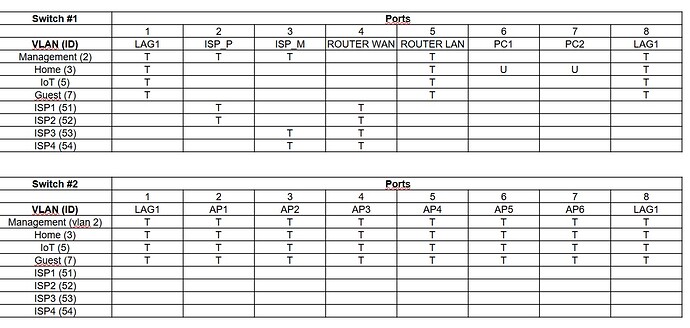
VLANs and Tagged and Untagged Ports:
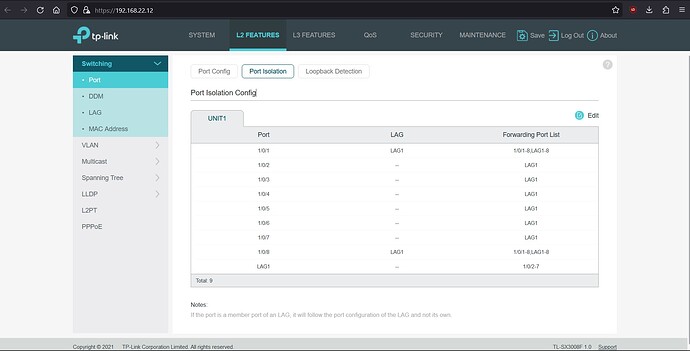
Switch #1 Config:
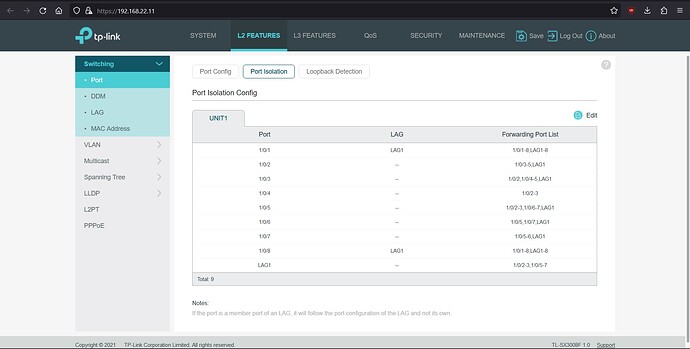
Switch #2 Config:
The network has been working quite well for a month, but a few days ago I did a scan on the guest network out of curiosity and it turned out that guest network clients are not isolated ![]()
In the configuration of the router and APs, I used one bridge and vlan_filtering, I don't know if it was a mistake because now it's hard for me solve the insulation problem.
I have read many topics on how to solve this problem:
- ebtables on router (ebtables is slow and outdated??? ebtables-nft is better???)
- ebtables on each AP
- kmod-br-netfilter + firewall rules
- separate vlans for each AP
- vlan_filtering (???)
- port isolation on Switch #2
- private vlans on Switch #2
I don't know which method would be the least invasive in my case, I prefer to configure Openwrt than a tp-link switches, but if there is no choice, I will do it too.Thank you in advance for your help.
Router /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd88:4a02:539a::/48'
option packet_steering '1'
config device
option name 'br0'
option type 'bridge'
option igmp_snooping '1'
option vlan_filtering '1'
list ports 'eth0'
config bridge-vlan
option device 'br0'
option vlan '2'
option alias 'mgmt'
list ports 'eth0:t'
config bridge-vlan
option device 'br0'
option vlan '3'
option alias 'home'
list ports 'eth0:t'
config bridge-vlan
option device 'br0'
option vlan '5'
option alias 'iot'
list ports 'eth0:t'
config bridge-vlan
option device 'br0'
option vlan '7'
option alias 'guest'
list ports 'eth0:t'
config interface 'mgmt'
option device 'br0.mgmt'
option proto 'static'
option ipaddr '192.168.22.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'home'
option device 'br0.home'
option proto 'static'
option ipaddr '192.168.33.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'iot'
option device 'br0.iot'
option proto 'static'
option ipaddr '192.168.55.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'guest'
option device 'br0.guest'
option proto 'static'
option ipaddr '192.168.77.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1.51'
option proto 'dhcp'
option metric '10'
option ipv6 '0'
option peerdns '0'
option dns '1.1.1.1 8.8.8.8 9.9.9.9 8.8.4.4'
config interface 'wanb'
option device 'eth1.52'
option proto 'dhcp'
option metric '12'
option ipv6 '0'
option peerdns '0'
option dns '1.1.1.1 8.8.8.8 9.9.9.9 8.8.4.4'
#config interface 'wanc'
# option device 'eth1.53'
# option proto 'dhcp'
# option metric '14'
# option ipv6 '0'
# option peerdns '0'
# option dns '1.1.1.1 8.8.8.8 9.9.9.9 8.8.4.4'
#config interface 'wand'
# option device 'eth1.54'
# option proto 'dhcp'
# option metric '16'
# option ipv6 '0'
# option peerdns '0'
# option dns '1.1.1.1 8.8.8.8 9.9.9.9 8.8.4.4'
Router /etc/config/firewall:
config defaults
option syn_flood 1
option input REJECT
option output ACCEPT
option forward REJECT
# option flow_offloading 1
# option flow_offloading_hw 0
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'home'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wanb'
# list network 'wanc'
# list network 'wand'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://github.com/openwrt/openwrt/issues/5066
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
# --- Management Zone ---
config zone
option name 'mgmt'
list network 'mgmt'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
config forwarding
option src 'mgmt'
option dest 'wan'
config rule
option src 'mgmt'
option proto 'udp'
option family 'ipv4'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule
option src 'mgmt'
option proto 'tcpudp'
option family 'ipv4'
option dest_port '53'
option target 'ACCEPT'
# --- IoT Zone ---
config zone
option name 'iot'
list network 'iot'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
config forwarding
option src 'iot'
option dest 'wan'
config rule
option src 'iot'
option proto 'udp'
option family 'ipv4'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule
option src 'iot'
option proto 'tcpudp'
option family 'ipv4'
option dest_port '53'
option target 'ACCEPT'
# --- GUEST Zone ---
config zone
option name 'guest'
list network 'guest'
option input 'REJECT'
option forward 'REJECT'
option output 'ACCEPT'
config forwarding
option src 'guest'
option dest 'wan'
config rule
option src 'guest'
option proto 'udp'
option family 'ipv4'
option src_port '67-68'
option dest_port '67-68'
option target 'ACCEPT'
config rule
option src 'guest'
option proto 'tcpudp'
option family 'ipv4'
option dest_port '53'
option target 'ACCEPT'
Router /etc/config/dhcp:
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
option confdir '/tmp/dnsmasq.d'
option noresolv '1'
option localuse '1'
list server '127.0.0.1#5453'
list server '0::1#5453'
config dhcp 'mgmt'
option interface 'mgmt'
option start '101'
option limit '50'
option leasetime '8h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'home'
option interface 'home'
option start '101'
option limit '100'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'iot'
option interface 'iot'
option start '101'
option limit '100'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'guest'
option interface 'guest'
option start '101'
option limit '100'
option leasetime '8h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config dhcp 'wanb'
option interface 'wanb'
option ignore '1'
#config dhcp 'wanc'
# option interface 'wanc'
# option ignore '1'
#config dhcp 'wand'
# option interface 'wand'
# option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Router iproute2:
BusyBox v1.36.1 (2023-06-16 07:48:53 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SNAPSHOT, r23401-a860e439ed
-----------------------------------------------------
root@router:~# ip -c -br l
lo UNKNOWN 00:00:00:00:00:00 <LOOPBACK,UP,LOWER_UP>
eth0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
eth1 UP 22:22:22:22:22:22 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.2@br0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.3@br0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.5@br0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.7@br0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
eth1.51@eth1 UP 44:44:44:44:44:44 <BROADCAST,MULTICAST,UP,LOWER_UP>
eth1.52@eth1 UP 44:44:44:44:44:44 <BROADCAST,MULTICAST,UP,LOWER_UP>
root@router:~#
root@router:~#
root@router:~# brctl show
bridge name bridge id STP enabled interfaces
br0 7fff.333333333333 no eth0
root@router:~#
root@router:~#
root@router:~# bridge vlan show
port vlan-id
eth0 2
3
5
7
br0 2
3
5
7
root@router:~#
AP /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd3d:6b1c:ba49::/48'
option packet_steering '1'
#config device
# option name 'wan'
# option macaddr 'xx:xx:xx:xx:xx:xx'
config device
option name 'br0'
option type 'bridge'
option igmp_snooping '1'
option vlan_filtering '1'
config bridge-vlan
option device 'br0'
option vlan '2'
option alias 'mgmt'
list ports 'wan:t'
list ports 'lan2:u*'
config bridge-vlan
option device 'br0'
option vlan '3'
option alias 'home'
list ports 'wan:t'
list ports 'lan3:u*'
config bridge-vlan
option device 'br0'
option vlan '5'
option alias 'iot'
list ports 'wan:t'
list ports 'lan4:u*'
config bridge-vlan
option device 'br0'
option vlan '7'
option alias 'guest'
list ports 'wan:t'
config interface 'mgmt'
option device 'br0.mgmt'
option proto 'static'
option ipaddr '192.168.22.31'
option netmask '255.255.255.0'
option gateway '192.168.22.1'
option dns '192.168.22.1'
option ip6assign '60'
config interface 'home'
option device 'br0.home'
option proto 'none'
config interface 'iot'
option device 'br0.iot'
option proto 'none'
config interface 'guest'
option device 'br0.guest'
option proto 'none'
AP /etc/config/wireless:
config wifi-device 'radio2g'
option disabled '0'
option type 'mac80211'
option path 'platform/soc/18000000.wifi'
option channel '5'
option band '2g'
option htmode 'HE20'
option country 'PL'
option he_bss_color '1'
config wifi-iface 'radio2g_home'
option disabled '1'
option device 'radio2g'
option network 'home'
option mode 'ap'
option ssid 'HOME'
option encryption 'sae'
option key 'home password'
option isolate '0'
option disassoc_low_ack '1'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option reassociation_deadline '20000'
option ieee80211k '1'
config wifi-iface 'radio2g_iot'
option disabled '1'
option device 'radio2g'
option network 'iot'
option mode 'ap'
option ssid 'IoT'
option encryption 'psk2'
option key 'iot password'
option isolate '0'
option hidden '1'
option disassoc_low_ack '1'
option wpa_disable_eapol_key_retries '1'
option tdls_prohibit '1'
option ieee80211w '1'
option ieee80211w_max_timeout '500'
option ieee80211w_retry_timeout '100'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option reassociation_deadline '20000'
option ieee80211k '1'
config wifi-iface 'radio2g_guest'
option disabled '0'
option device 'radio2g'
option network 'guest'
option mode 'ap'
option ssid 'GUEST'
option encryption 'psk2'
option key 'guest password'
option isolate '1'
option disassoc_low_ack '1'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option reassociation_deadline '20000'
option bss_transition '1'
option ieee80211k '1'
config wifi-device 'radio5g'
option disabled '0'
option type 'mac80211'
option path 'platform/soc/18000000.wifi+1'
option channel '36'
option band '5g'
option htmode 'HE40'
option country 'PL'
option he_bss_color '1'
config wifi-iface 'radio5g_guest'
option disabled '0'
option device 'radio5g'
option network 'guest'
option mode 'ap'
option ssid 'GUEST'
option encryption 'psk2'
option key 'guest password'
option isolate '1'
option doth '1'
option disassoc_low_ack '1'
option ieee80211r '1'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option reassociation_deadline '20000'
option bss_transition '1'
option ieee80211k '1'
AP iproute2:
BusyBox v1.36.1 (2023-06-14 13:16:15 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SNAPSHOT, r23401-a860e439ed
-----------------------------------------------------
root@ap1:~# ip -c -br l
lo UNKNOWN 00:00:00:00:00:00 <LOOPBACK,UP,LOWER_UP>
eth0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
lan4@eth0 LOWERLAYERDOWN 11:11:11:11:11:11 <NO-CARRIER,BROADCAST,MULTICAST,UP>
lan3@eth0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
lan2@eth0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
wan@eth0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.2@br0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.3@br0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.5@br0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
br0.7@br0 UP 11:11:11:11:11:11 <BROADCAST,MULTICAST,UP,LOWER_UP>
phy0-ap0 UP 22:22:22:22:22:22 <BROADCAST,MULTICAST,UP,LOWER_UP>
phy1-ap0 UP 33:33:33:33:33:33 <BROADCAST,MULTICAST,UP,LOWER_UP>
root@ap1:~#
root@ap1:~#
root@ap1:~# brctl show
bridge name bridge id STP enabled interfaces
br0 7fff.111111111111 no phy1-ap0
lan4
lan2
wan
lan3
phy0-ap0
root@ap1:~#
root@ap1:~#
root@ap1:~# bridge vlan show
port vlan-id
lan4 5 PVID Egress Untagged
lan3 2
3
lan2 2 PVID Egress Untagged
wan 2
3
5
7
br0 2
3
5
7
phy0-ap0 7 PVID Egress Untagged
phy1-ap0 7 PVID Egress Untagged
root@ap1:~#