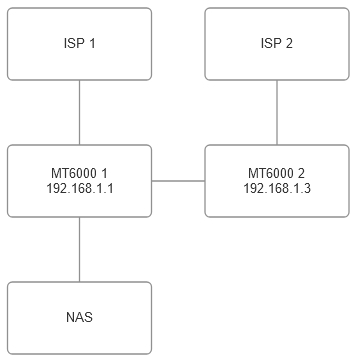
With two ISPs, two MT6000 and one NAS. Is it possible to share the NAS with both networks if I connect an ethernet cable between the two routers and if it's technically possible how would I configure them?
Thanks for any help.
With two ISPs, two MT6000 and one NAS. Is it possible to share the NAS with both networks if I connect an ethernet cable between the two routers and if it's technically possible how would I configure them?

Thanks for any help.
same subnet, you don't need to configure anything, assumed all ports used are LAN ports.
You mean the two routers are not connected now?
LAN ports between router -> NAS and router -> Router. WAN ports between ISP -> Router.
No, the diagram is what I propose. Currently there is no cable between the two routers. Tomorrow I will plug one in though and see what happens.
as long as your MT6000s and the NAS are on the same LAN, you're good to go.
They both have their own, different, ISP and DHCP is turned on.
you should only have one DHCP on a LAN, so how does it work ?
No, don't do this. You'll end up with unexpected behaviors because the two lans will have their own DHCP servers which will conflict.
Is it possible/desirable to connect both ISPs into the same physical router?
They are two seperate networks, the only thing connecting them would be the LAN cable between the routers.
OK, I thought there would be more to it.
Logistically not possible and also not desirable. Would rather keep them seperate and just share the NAS if it's possible. I'd probably need a different router as well with more ports on or a switch.
You can do this with VLANs. You need the two networks to be on different subnets. Are both routers running official openwrt? (or are they on the gl-inet vendor firmware?)
ok thanks. Both are on official OpenWRT 23.05.4.
Is this going to be more trouble than it's worth though? I could just stick a USB stick in the second router and swap network adaptors when I need to copy something to it instead.
It's not that complicated, but depends on your use case. Great opportunity to learn a bit more advanced networking ![]()
Basically, one network needs to be set to a different subnet. Then one physical port split will be off from the regular lan to use as the connection to the other router. A static route will be added to the other router and you'll be all set with the ability to connect between the two routers.
I'm all for learning more ![]()
I've set the first router to 192.168.2.1 and attatched a cable between LAN 3 on each router. How do I do the rest?
Also I notice when I changed the subnet in the luci GUI this line was removed from etc\config\dhcp
option ra_slaac '1'
Does that matter? I didn't change that, I couldn't even tell you where it is in the GUI.
Normally you would use one (and only one) router with MWAN: One rj45 port connected to ISP1 and another rj45 port connected to ISP2.
In MWAN you can define how to use the two ISP's (load balancing, failover, etc.).
Disconnect that cable.... we're not ready for it yet.
Let's see the configuration of that first router:
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/dhcp
cat /etc/config/firewall
Yep I agree.
The two lines come in in different rooms, I have existing CAT5e between the rooms I can use to connect the routers together.
ISP 1 is is 2/1 Gbps FTTP
ISP 2 is 70/19 Mbps FTTC with IPTV
They need to operate seperatly. Only 2 multigig ports as well so I'd be without mutigig LAN and wouldn't have enough total ports so would need switches.
Cable disconnected. ![]()
R1 config
ubus call system board
{
"kernel": "5.15.162",
"hostname": "OpenWrt",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT6000",
"board_name": "glinet,gl-mt6000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.4",
"revision": "r24012-d8dd03c46f",
"target": "mediatek/filogic",
"description": "OpenWrt 23.05.4 r24012-d8dd03c46f"
}
}
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd2e:c093:653b::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config device
option name 'lan1'
option macaddr '-'
config device
option name 'lan2'
option macaddr '-'
config device
option name 'lan3'
option macaddr '-'
config device
option name 'lan4'
option macaddr '-'
config device
option name 'lan5'
option macaddr '-'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth1'
option macaddr '-'
config interface 'wan'
option device 'eth1.911'
option proto 'pppoe'
option username '-'
option password '-'
option ipv6 'auto'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
list dns '2606:4700:4700::1111'
list dns '2606:4700:4700::1001'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2606:4700:4700::1111'
list dns '2606:4700:4700::1001'
config device
option type '8021q'
option ifname 'eth1'
option vid '911'
option name 'eth1.911'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Ok... so now we're going to remove port lan3 from br-lan and assign it to a new network interface. br-lan should look like this:
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan4'
list ports 'lan5'
Next, we'll create a new network interface using port lan3. I'm going to aassume that the address 192.168.1.2 is available and does not conflict with anything on your other network.
config interface 'lan2'
option device 'lan3'
option proto 'static'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
option netmask '255.255.255.0'
Add this network lan2 to the lan firewall zone.
Next, we'll add a route on your other router (this gets added to the /etc/config/network file):
config route
option interface 'lan'
option target '192.168.2.0/24'
option gateway '192.168.1.2'
Restart both routers, connect them together, and that should allow you to reach the NAS (by IP address) from the 192.168.2.0/24 network. If it doesn't work, check that the NAS doesn't have any host-level firewalls or other settings that would restrict connections from other subnets.