Hi guys,
Thanks a lot for all these replies.
It starts to be too hard for me to understand all of that (my English is not so good, I do my best)
IPv6 @home still doesn't work with the he.net tunnel.
So I decided to make another test, from scratch, stop working on my new router (Fritz!box 4040 with OpenWRT 19.07.3 with a custom build: see here => VLAN tagging on ipq40xx (GL-B1300) no longer works and use my old one (Western Digital My Net N750) also running 19.07.3.
So there is the DETAIL of all what I have done:
- went to tunnelbroker.net and get a /48 to conform with the tunnelbroker.sh
- reset Western Digital router
- Leave it unconnected from WAN/LAN (ISP box in bridge mode - fixed IPv4), only connected to my laptop
- Log on OpenWrt 19.07.3 r11063-85e04e9f46
- System : set hostname/timezone/NTP server => Save and apply
- Administration: password / allow ssh from LAN => Save and apply
- Network/Interfaces:
- WAN: change LAN settings (IP .. so scope) to match my home LAN
- WAN:
IPv6 assignment lengthto 64 - WAN: change DHCPv4 settings to:
Start address: 150; limit: 50, lease time 1h - WAN: save / save and apply ...
=> on my computer ipconfig/renew - WAN6: uncheck
Bring up on boot
Note: this time I didn't change the IPv6 ULA-Prefix (as I used to do before with one generated on https://cd34.com/rfc4193/ )
-
DNS:
- Set Local domain on DNS Server settings => Save and apply
-
SSH on the router:
- on /etc/config/dhcp add my static leases (without any "option duid" or "option hostid" ... just to have my IPv4 hosts IPs correct as soon as possible)
=> /etc/init.d/dnsmasq restart - on /etc/config/firewall add my very basic FW rules (DNAT for my mail server on TCP 25/80/143/443/587)
=> /etc/init.d/firewall restart
- on /etc/config/dhcp add my static leases (without any "option duid" or "option hostid" ... just to have my IPv4 hosts IPs correct as soon as possible)
-
Plug the router in place of the Fritz!box 4040
- quick check for the mail server (send/receive mail) => Ok
- install 6in4 : opkg update && opkg install 6in4 (oops, saw later than the script will do that alone)
- copy / edit tunnelbroker.sh, put in on the router, run it.
- run Ok
- quick check on the router Ok
- reboot router, quick check again (HENET on WAN firewall zone, tunnel up and running ...)
- ping4 and ping6 from Luci Diagnostics works fine
- => ... but not from the LAN
From my LAN:
- IPv4 DNS resolution => OK
- ping4 => Ok
- IPv6 resolution => OK
- ping6 => KO (100% packet loss)
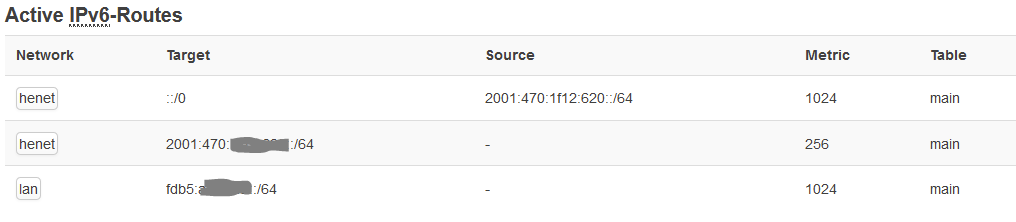
I see I have no gateway on the HE link:

Any idea ??
And also, my Linux clients only retain the IPv6 information on /etc/resolv.conf
So I only have an IPv6 nameserver on this file (instead on 3 lines, the "domain" search, one IPv4 nameserver, one IPv6 name server)
I can add the search domain in the DHCPv6 configuration, but not the IPv4 name server to use ... a Debian behaviour ???
Thanks in advance for any help
I just see the last @jow reply ... with read this later, my children also need a bit of attention !!
but still problems with leases time (without the ra_useleasetime set)
Regards
Herve