Yeah, I've wrote an email to my ISP's support team about a single /64 prefix delegated from their customer-CPE, and still waiting for a response.
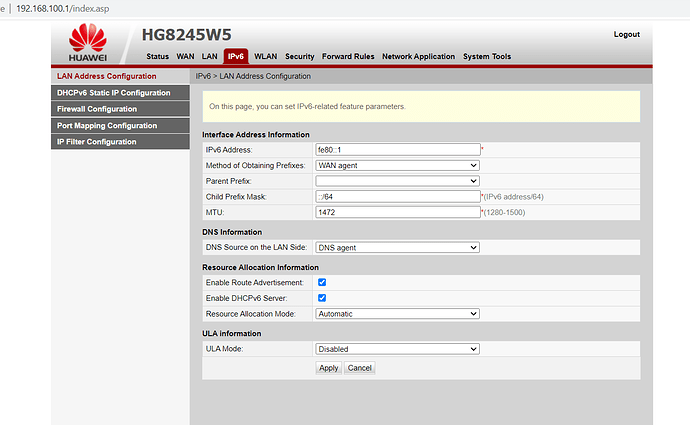
UPD: ISP Orange Slovensko has officially confirmed to me that currently their customer-CPE devices do not support (and therefore cannot provide) an IPv6 Prefix Delegation greater than /64 to the LAN port of the Huawei fiber router.
At the same time, I made pretty good progress on my side.
I found the article Configure DHCPv6c on WAN for multiple PD requests for AT&T fiber? and.... it seems that Orange Slovensko ISP uses the same IPv6 /64 prefix delegation method as AT&T does. ![]()
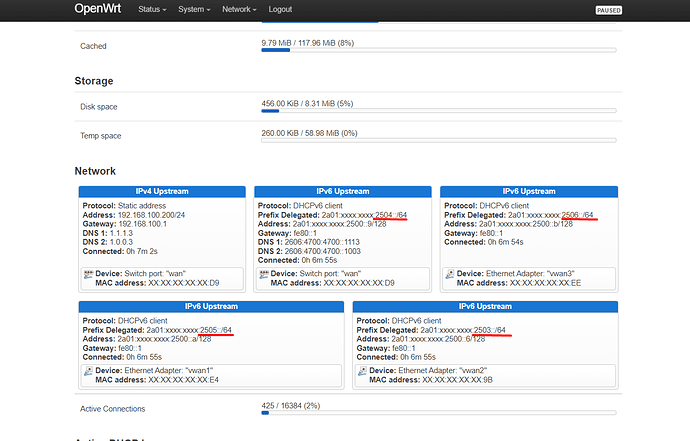
See my test results:
So, I was able to get 4 different IPv6-PD /64 delegated prefixes (didn't try more):
IPv6-PD: 2a01:xxxx:xxxx:2503::/64
IPv6-PD: 2a01:xxxx:xxxx:2504::/64
IPv6-PD: 2a01:xxxx:xxxx:2505::/64
IPv6-PD: 2a01:xxxx:xxxx:2506::/64
For those who want to do the same, here is an example of my working /etc/config/network file for OpenWrt 22.03.x: (config. idea has been taken from here and here):
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
config interface 'lan'
option proto 'static'
option device 'br-lan.55'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid '::1'
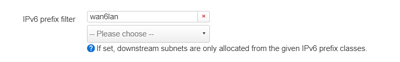
list ip6class 'wan6lan'
config interface 'wan'
option device 'wan'
option proto 'static'
option ipaddr '192.168.100.200'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
option peerdns '0'
list dns '1.1.1.2'
list dns '1.0.0.2'
config interface 'wan6'
option proto 'dhcpv6'
option device 'wan'
option peerdns '0'
list dns '2606:4700:4700::1112'
list dns '2606:4700:4700::1002'
option reqaddress 'try'
option reqprefix 'no'
config bridge-vlan
option device 'br-lan'
option vlan '8'
config bridge-vlan
option device 'br-lan'
list ports 'lan1:u*'
list ports 'lan2:u*'
option vlan '55'
config bridge-vlan
option device 'br-lan'
option vlan '7'
config interface 'IOT'
option proto 'static'
option device 'br-lan.7'
option ipaddr '172.16.7.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid '::1'
list ip6class 'wan6iot'
config interface 'GUEST'
option proto 'static'
option device 'br-lan.8'
option ipaddr '192.168.8.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid '::1'
list ip6class 'wan6guest'
config device 'vwan1'
option name 'vwan1'
option type 'macvlan'
option ifname 'wan'
config device 'vwan2'
option name 'vwan2'
option type 'macvlan'
option ifname 'wan'
config device 'vwan3'
option name 'vwan3'
option type 'macvlan'
option ifname 'wan'
config interface 'wan6lan'
option proto 'dhcpv6'
option peerdns '0'
option reqaddress 'none'
option reqprefix 'auto'
option device 'vwan1'
config interface 'wan6iot'
option proto 'dhcpv6'
option peerdns '0'
option reqaddress 'none'
option reqprefix 'auto'
option device 'vwan2'
config interface 'wan6guest'
option proto 'dhcpv6'
option peerdns '0'
option reqaddress 'none'
option reqprefix 'auto'
option device 'vwan3'
Install kmod-macvlan module: opkg update && opkg install kmod-macvlan. So, all the 'magic' will be achieved by the kmod-macvlan that allows to create multiple wan6 virtual interfaces (hence to request and obtain multiple IPv6 /64 blocks), and to assign these virtual wan6 interfaces into appropriate DHCPv6 clients via ip6class and ip6assign '64' settings.
Please note that Luci will be available by the
192.168.0.1 address after that (you can change it later).
- Check the DHCPv6 settings for the
LAN,IOTandGuestinterfaces, it should be the following:RA-Service = Server Mode,DHCPv6-Service = Server Mode,NDP-Proxy = disabled,RA Flags = Other Config,Enable SLAAC = True. - Meanwhile, the DHCPv6 settings for the
wan6interface should be:Designated master = disabled,RA-Service = disabled,DHCPv6-Service = disabled,NDP-Proxy = disabled. - DHCP Server should not be configured for
wan6lan,wan6iotandwan6guestinterfaces.
![]() Also, make sure that firewall rules allow ipv6 traffic for your new interfaces:
Also, make sure that firewall rules allow ipv6 traffic for your new interfaces:
# Restore firewall rules to default
cp /rom/etc/config/firewall /etc/config/firewall
uci delete firewall.@zone[2]
uci delete firewall.@zone[1]
uci delete firewall.@zone[0]
uci delete firewall.@forwarding[0]
uci commit firewall
# Adding new firewall zones
uci add firewall zone
uci set firewall.@zone[-1].name='lan'
uci set firewall.@zone[-1].input='ACCEPT'
uci set firewall.@zone[-1].output='ACCEPT'
uci set firewall.@zone[-1].forward='ACCEPT'
uci add_list firewall.@zone[-1].network='lan'
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='lan'
uci set firewall.@forwarding[-1].dest='wan'
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='lan'
uci set firewall.@forwarding[-1].dest='IOT'
uci commit firewall
uci add firewall zone
uci set firewall.@zone[-1].name='wan'
uci set firewall.@zone[-1].input='REJECT'
uci set firewall.@zone[-1].output='ACCEPT'
uci set firewall.@zone[-1].forward='REJECT'
uci set firewall.@zone[-1].masq='1'
uci set firewall.@zone[-1].mtu_fix='1'
uci add_list firewall.@zone[-1].network='wan'
uci add_list firewall.@zone[-1].network='wan6'
uci add_list firewall.@zone[-1].network='wan6guest'
uci add_list firewall.@zone[-1].network='wan6iot'
uci add_list firewall.@zone[-1].network='wan6lan'
uci commit firewall
uci add firewall zone
uci set firewall.@zone[-1].name='GUEST'
uci set firewall.@zone[-1].input='REJECT'
uci set firewall.@zone[-1].output='ACCEPT'
uci set firewall.@zone[-1].forward='REJECT'
uci add_list firewall.@zone[-1].network='GUEST'
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='GUEST'
uci set firewall.@forwarding[-1].dest='wan'
uci commit firewall
uci add firewall zone
uci set firewall.@zone[-1].name='IOT'
uci set firewall.@zone[-1].input='REJECT'
uci set firewall.@zone[-1].output='ACCEPT'
uci set firewall.@zone[-1].forward='REJECT'
uci add_list firewall.@zone[-1].network='IOT'
uci add firewall forwarding
uci set firewall.@forwarding[-1].src='IOT'
uci set firewall.@forwarding[-1].dest='wan'
uci commit firewall
service firewall restart
# Adding custom Traffic Rules
# Allow Guest DHCP for ipv6
uci add firewall rule
uci set firewall.@rule[-1].name='Allow Guest_DHCPv6'
uci set firewall.@rule[-1].family='ipv6'
uci set firewall.@rule[-1].proto='udp'
uci set firewall.@rule[-1].src='GUEST'
uci set firewall.@rule[-1].src_port='546'
uci set firewall.@rule[-1].dest_port='547'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow Guest DHCP for ipv4
uci add firewall rule
uci set firewall.@rule[-1].name='Allow Guest_DHCP'
uci set firewall.@rule[-1].family='ipv4'
uci set firewall.@rule[-1].proto='udp'
uci set firewall.@rule[-1].src='GUEST'
uci set firewall.@rule[-1].dest_port='67-68'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow Guest DNS for ipv4 and ipv6
uci add firewall rule
uci set firewall.@rule[-1].name='Allow Guest_DNS'
uci set firewall.@rule[-1].src='GUEST'
uci set firewall.@rule[-1].dest_port='53'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow ipv6 traffic to Guest
uci add firewall rule
uci set firewall.@rule[-1].name='Allow IPv6_Guest'
uci set firewall.@rule[-1].family='ipv6'
uci set firewall.@rule[-1].proto='icmp'
uci add_list firewall.@rule[-1].icmp_type='echo-reply'
uci add_list firewall.@rule[-1].icmp_type='echo-request'
uci add_list firewall.@rule[-1].icmp_type='neighbour-advertisement'
uci add_list firewall.@rule[-1].icmp_type='neighbour-solicitation'
uci add_list firewall.@rule[-1].icmp_type='port-unreachable'
uci add_list firewall.@rule[-1].icmp_type='protocol-unreachable'
uci add_list firewall.@rule[-1].icmp_type='router-advertisement'
uci add_list firewall.@rule[-1].icmp_type='router-solicitation'
uci add_list firewall.@rule[-1].icmp_type='time-exceeded'
uci set firewall.@rule[-1].src='GUEST'
uci set firewall.@rule[-1].target='ACCEPT'
uci set firewall.@rule[-1].limit='1000/sec'
uci set firewall.@rule[-1].limit_burst='100'
uci commit firewall
# Block Guest access to all networks
uci add firewall rule
uci set firewall.@rule[-1].name='Block Guest-to-All networks'
uci set firewall.@rule[-1].proto='all'
uci set firewall.@rule[-1].src='GUEST'
uci set firewall.@rule[-1].dest='*'
uci add_list firewall.@rule[-1].dest_ip='192.168.100.0/24'
uci add_list firewall.@rule[-1].dest_ip='192.168.0.0/24'
uci add_list firewall.@rule[-1].dest_ip='fc00::/7'
uci add_list firewall.@rule[-1].dest_ip='fe80::/10'
uci set firewall.@rule[-1].target='DROP'
uci commit firewall
# Allow IOT DHCP for ipv6
uci add firewall rule
uci set firewall.@rule[-1].name='Allow IOT_DHCPv6'
uci set firewall.@rule[-1].family='ipv6'
uci set firewall.@rule[-1].proto='udp'
uci set firewall.@rule[-1].src='IOT'
uci set firewall.@rule[-1].src_port='546'
uci set firewall.@rule[-1].dest_port='547'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow IOT DHCP for ipv4
uci add firewall rule
uci set firewall.@rule[-1].name='Allow IOT_DHCP'
uci set firewall.@rule[-1].family='ipv4'
uci set firewall.@rule[-1].proto='udp'
uci set firewall.@rule[-1].src='IOT'
uci set firewall.@rule[-1].dest_port='67-68'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow IOT DNS for ipv4 and ipv6
uci add firewall rule
uci set firewall.@rule[-1].name='Allow IOT_DNS'
uci set firewall.@rule[-1].src='IOT'
uci set firewall.@rule[-1].dest_port='53'
uci set firewall.@rule[-1].target='ACCEPT'
uci commit firewall
# Allow ipv6 traffic to IOT
uci add firewall rule
uci set firewall.@rule[-1].name='Allow IPv6_IOT'
uci set firewall.@rule[-1].family='ipv6'
uci set firewall.@rule[-1].proto='icmp'
uci add_list firewall.@rule[-1].icmp_type='echo-reply'
uci add_list firewall.@rule[-1].icmp_type='echo-request'
uci add_list firewall.@rule[-1].icmp_type='neighbour-advertisement'
uci add_list firewall.@rule[-1].icmp_type='neighbour-solicitation'
uci add_list firewall.@rule[-1].icmp_type='port-unreachable'
uci add_list firewall.@rule[-1].icmp_type='protocol-unreachable'
uci add_list firewall.@rule[-1].icmp_type='router-advertisement'
uci add_list firewall.@rule[-1].icmp_type='router-solicitation'
uci add_list firewall.@rule[-1].icmp_type='time-exceeded'
uci set firewall.@rule[-1].src='IOT'
uci set firewall.@rule[-1].target='ACCEPT'
uci set firewall.@rule[-1].limit='1000/sec'
uci set firewall.@rule[-1].limit_burst='100'
uci commit firewall
# Block IOT access to all networks
uci add firewall rule
uci set firewall.@rule[-1].name='Block IOT-to-All networks'
uci set firewall.@rule[-1].proto='all'
uci set firewall.@rule[-1].src='IOT'
uci set firewall.@rule[-1].dest='*'
uci add_list firewall.@rule[-1].dest_ip='192.168.100.0/24'
uci add_list firewall.@rule[-1].dest_ip='192.168.0.0/24'
uci add_list firewall.@rule[-1].dest_ip='fc00::/7'
uci add_list firewall.@rule[-1].dest_ip='fe80::/10'
uci set firewall.@rule[-1].target='DROP'
uci commit firewall
service firewall restart
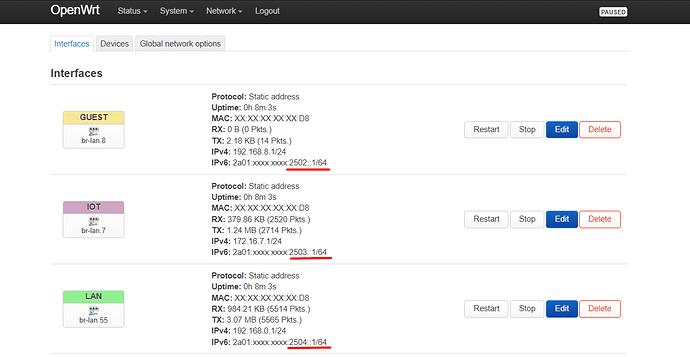
As a result of this configuration, three (3) ipv6 /64 blocks should be assigned to the LAN, IOT and Guest interfaces accordingly (see "Interfaces" tab in Luci):