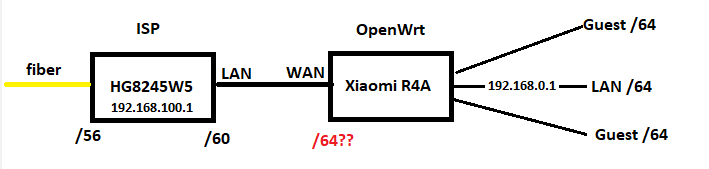
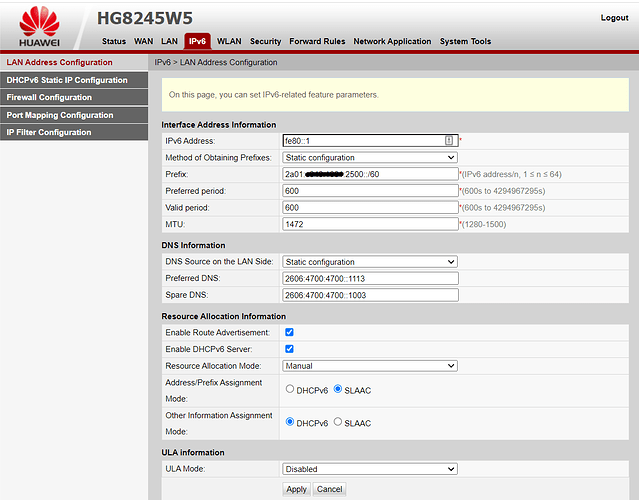
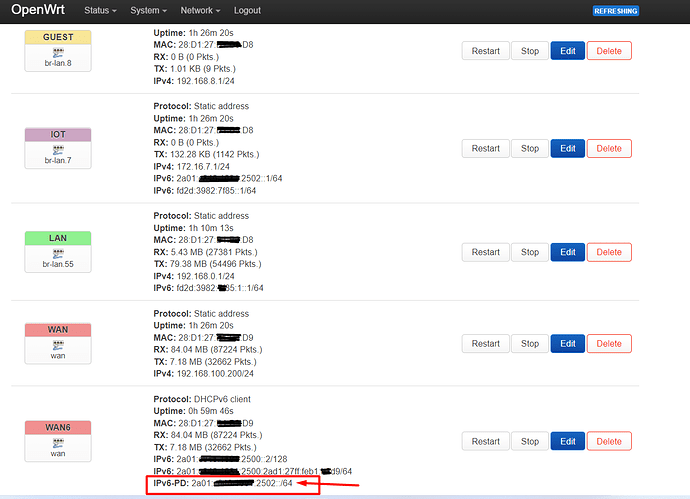
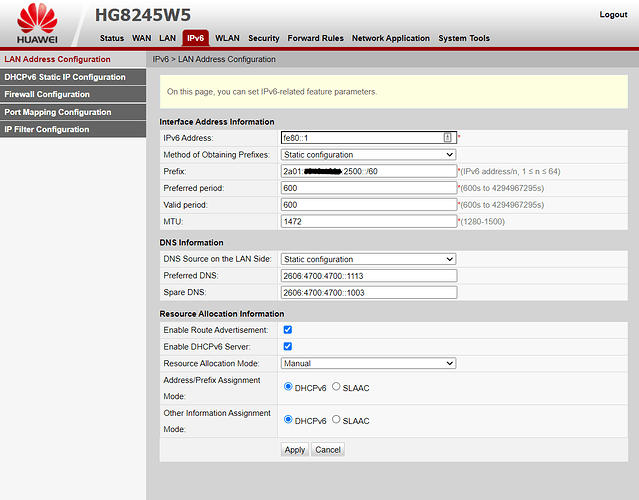
ubus call system board;
uci export network;
uci export dhcp; ip6tables-save -c; ifstatus wan6
BusyBox v1.35.0 (2022-06-10 07:20:21 UTC) built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 22.03.0-rc4, r19426-2b1941e47d
-----------------------------------------------------
root@OpenWrt:~# ubus call system board; \
> uci export network; \
> uci export dhcp; ip6tables-save -c; ifstatus wan6
{
"kernel": "5.10.120",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "Xiaomi Mi Router 4A Gigabit Edition",
"board_name": "xiaomi,mi-router-4a-gigabit",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.0-rc4",
"revision": "r19426-2b1941e47d",
"target": "ramips/mt7621",
"description": "OpenWrt 22.03.0-rc4 r19426-2b1941e47d"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fd2d:3982:7f85::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '64'
option device 'br-lan.55'
option ipaddr '192.168.0.1'
config interface 'wan'
option device 'wan'
option proto 'static'
option ipaddr '192.168.100.200'
option netmask '255.255.255.0'
option gateway '192.168.100.1'
list dns '1.1.1.3'
list dns '1.0.0.3'
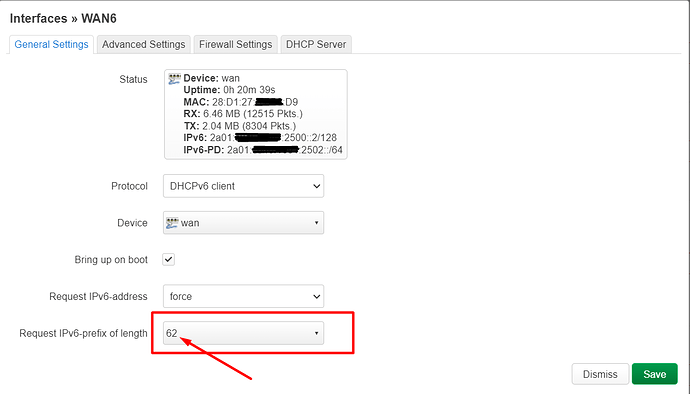
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'force'
option reqprefix '60'
config bridge-vlan
option device 'br-lan'
option vlan '8'
config bridge-vlan
option device 'br-lan'
list ports 'lan1:u*'
list ports 'lan2:u*'
option vlan '55'
config bridge-vlan
option device 'br-lan'
option vlan '7'
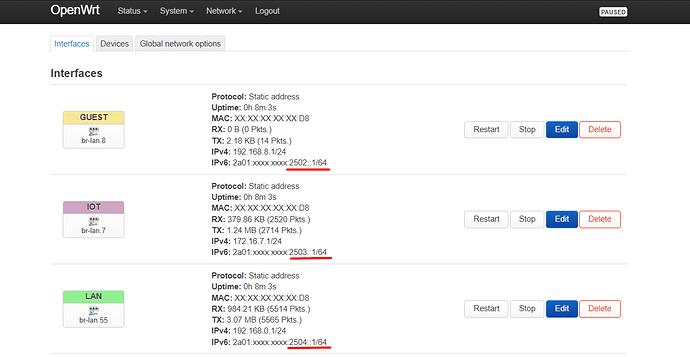
config interface 'IOT'
option proto 'static'
option device 'br-lan.7'
option ipaddr '172.16.7.1'
option netmask '255.255.255.0'
option ip6assign '64'
config interface 'GUEST'
option proto 'static'
option device 'br-lan.8'
option ipaddr '192.168.8.1'
option netmask '255.255.255.0'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
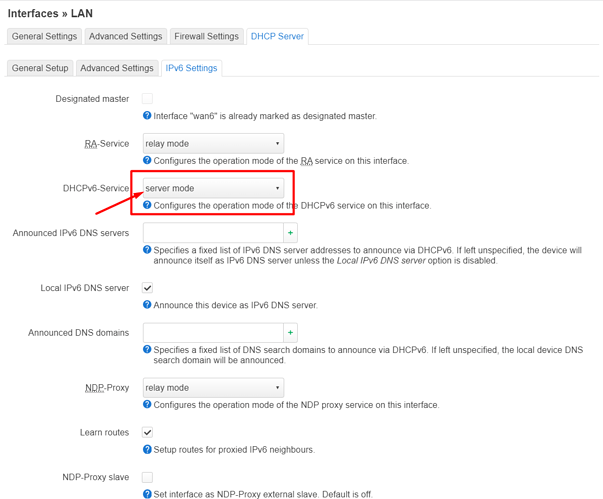
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv4 'server'
option start '2'
option limit '50'
list dhcp_option ' 6,1.1.1.3,1.0.0.3'
option ra 'relay'
option dhcpv6 'relay'
option ndp 'relay'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option start '100'
option limit '10'
option leasetime '12h'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'IOT'
option interface 'IOT'
option leasetime '12h'
option start '2'
option limit '10'
list dhcp_option '6,1.1.1.3,1.0.0.3'
option ra 'relay'
option dhcpv6 'relay'
option ndp 'relay'
config dhcp 'GUEST'
option interface 'GUEST'
option leasetime '12h'
option start '2'
list dhcp_option '6,1.1.1.3,1.0.0.3'
option limit '20'
list ra_flags 'none'
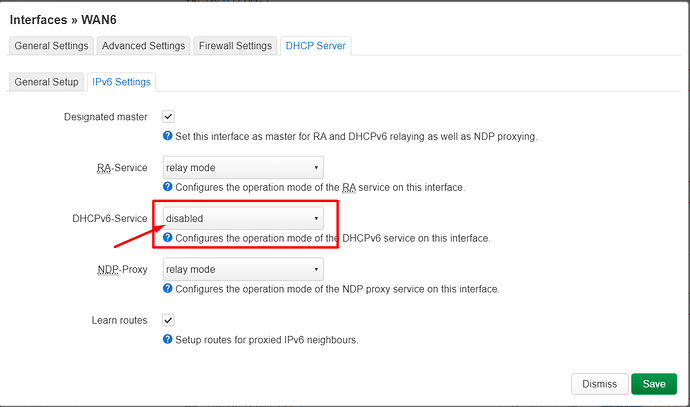
config dhcp 'wan6'
option interface 'wan6'
option ignore '1'
option master '1'
option ra 'relay'
option dhcpv6 'relay'
option ndp 'relay'
-ash: ip6tables-save: not found
{
"up": true,
"pending": false,
"available": true,
"autostart": true,
"dynamic": false,
"uptime": 27,
"l3_device": "wan",
"proto": "dhcpv6",
"device": "wan",
"metric": 0,
"dns_metric": 0,
"delegation": true,
"ipv4-address": [
],
"ipv6-address": [
{
"address": "2a01:xxxx:xxxx:2500::2",
"mask": 128,
"preferred": 571,
"valid": 571
},
{
"address": "2a01:xxxx:xxxx:2500:2ad1:27ff:feb1:xxd9",
"mask": 64,
"preferred": 577,
"valid": 577
}
],
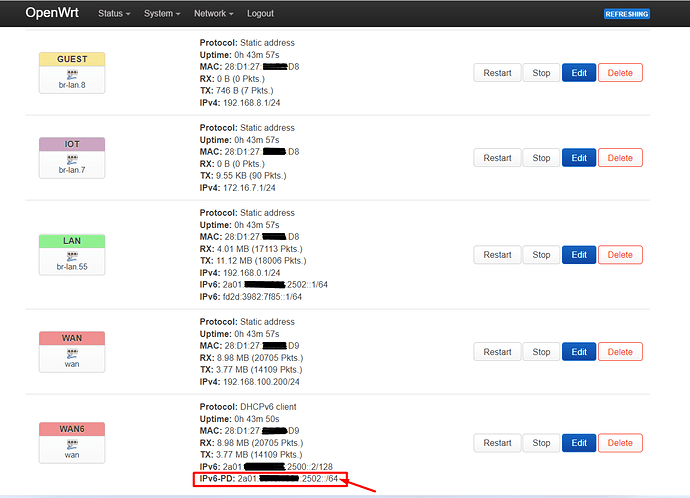
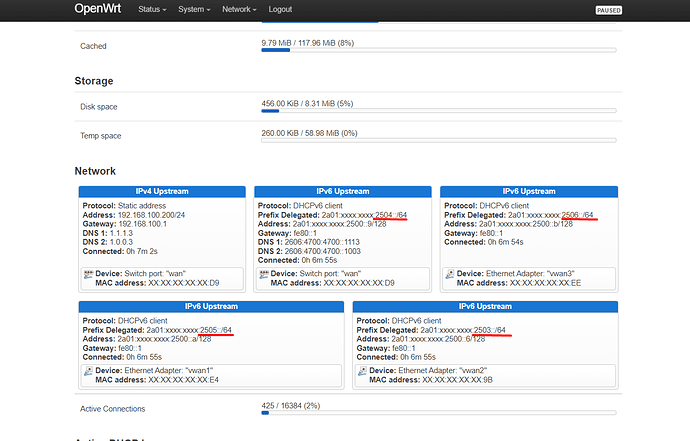
"ipv6-prefix": [
{
"address": "2a01:xxxx:xxxx:2502::",
"mask": 64,
"preferred": 571,
"valid": 571,
"class": "wan6",
"assigned": {
"IOT": {
"address": "2a01:xxxx:xxxx:2502::",
"mask": 64
}
}
}
],
"ipv6-prefix-assignment": [
],
"route": [
{
"target": "2a01:xxxx:xxxx:2500::",
"mask": 64,
"nexthop": "::",
"metric": 256,
"valid": 577,
"source": "::/0"
},
{
"target": "::",
"mask": 0,
"nexthop": "fe80::1",
"metric": 512,
"valid": 1777,
"source": "2a01:xxxx:xxxx:2500:2ad1:27ff:feb1:xxd9/64"
},
{
"target": "::",
"mask": 0,
"nexthop": "fe80::1",
"metric": 512,
"valid": 1777,
"source": "2a01:xxxx:xxxx:2502::/64"
},
{
"target": "::",
"mask": 0,
"nexthop": "fe80::1",
"metric": 512,
"valid": 1777,
"source": "2a01:xxxx:xxxx:2500::2/128"
}
],
"dns-server": [
"2606:4700:4700::1113",
"2606:4700:4700::1003"
],
"dns-search": [
],
"neighbors": [
],
"inactive": {
"ipv4-address": [
],
"ipv6-address": [
],
"route": [
],
"dns-server": [
],
"dns-search": [
],
"neighbors": [
]
},
"data": {
"passthru": "001700202606470047000000000000000000111326064700470000000000000000001003"
}
}
root@OpenWrt:~#