d-cubed
February 24, 2021, 5:01pm
1
I see a ticket from May 2020 where this also happened. I was living my life with OpenWRT and IPv6 worked fine out of the box. Then it just disappeared one day.here , the output of ifstatus wan6
ifstatus wan6
{
"up": false,
"pending": true,
"available": true,
"autostart": true,
"dynamic": false,
"proto": "dhcpv6",
"device": "br-wan6",
"data": {
}
}
ifconfig wan6 ifconfig: wan6: error fetching interface information: Device not found
ifup wan6 doesn't return anything.
uci -q delete network.wan.type
uci -q delete network.wan6.type
uci set network.wan6.ifname="@wan"
uci commit network
/etc/init.d/network restart
trendy
February 24, 2021, 5:20pm
4
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user
1 Like
d-cubed
February 24, 2021, 6:01pm
5
Thanks. I didn't see any MAC addresses, public IP addresses, or wireless info.
{
"kernel": "4.14.171",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT1900ACv2",
"board_name": "linksys,cobra",
"release": {
"distribution": "OpenWrt",
"version": "19.07.2",
"revision": "r10947-65030d81f3",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.2 r10947-65030d81f3"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdde:1376:5a15::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option type 'bridge'
config interface 'wan6'
option proto 'dhcpv6'
option type 'bridge'
option reqprefix 'auto'
option reqaddress 'try'
option ifname '@wan'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
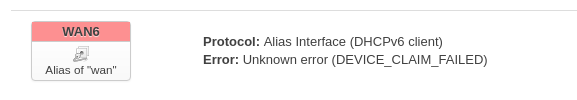
The GUI shows this.
trendy
February 24, 2021, 8:13pm
6
d-cubed:
option type 'bridge'
Remove the bridge from wan and wan6. Also have a look here, he had the same issue with you.
Okay, something is very strange here. As a test, I temporarily set the protocol on WAN (eth0.2) to 'DHCPv6 client' instead of 'DHCP client' and restarted the interface. Thereafter, as expected, I pulled an IPv6 address via DHCP and could use ping6 as a test, BUT the IPv4 address was gone and I couldn't use ping4 (again, as expected). After then going back into the WAN (eth0.2) configuration and changing it back to 'DHCP client', I pull an IPv4 address on WAN and an IPv6 address on WAN6 (which…
2 Likes
d-cubed
February 24, 2021, 8:42pm
7
You are awesome. I had not touched my router config. Any thoughts on how that might have happened?
uci -q delete network.wan.type
uci -q delete network.wan6.type
uci set network.wan6.ifname="@wan"
uci commit network
/etc/init.d/network restart
and it worked. Thank you.
Nano should be available. Do opkg update and you should get it
2 Likes
d-cubed
February 25, 2021, 1:54pm
10
so odd, it didn't work - then it did
system
March 7, 2021, 1:54pm
11
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.