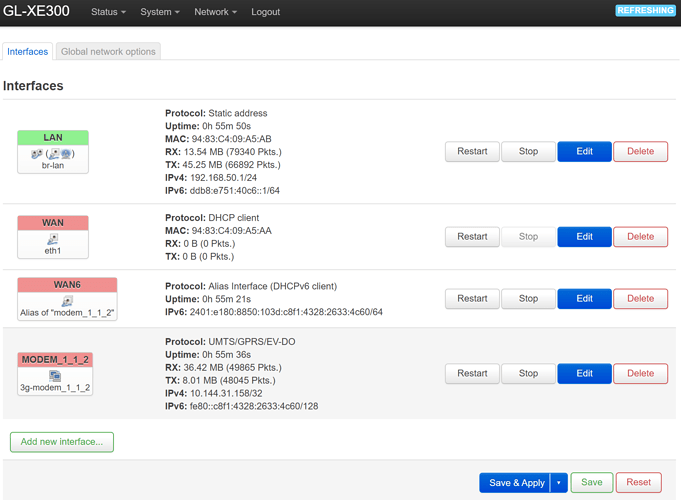
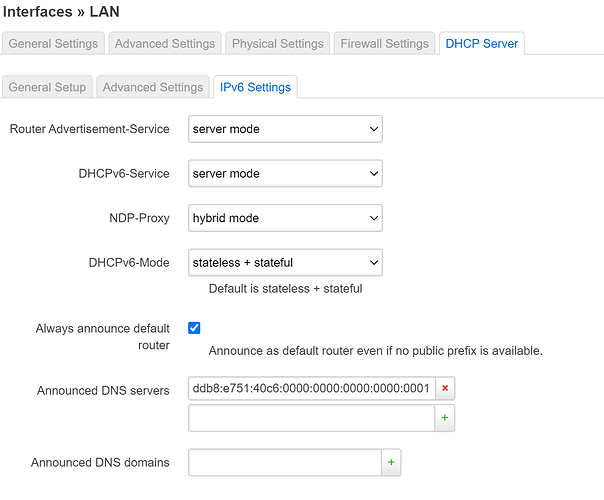
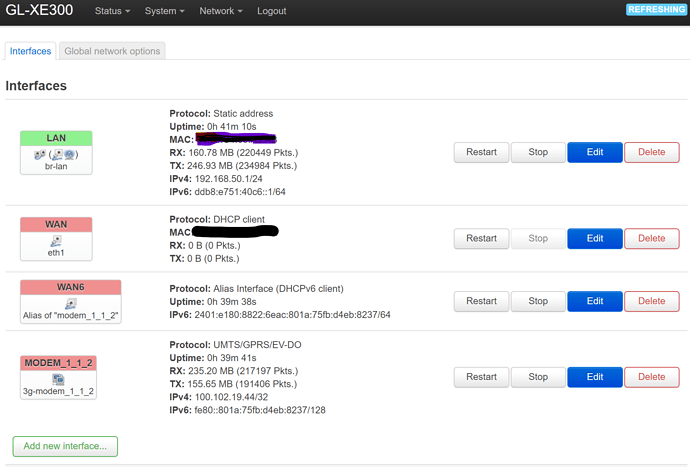
Newbie here.ipv6.google.com , it works normal.
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
option network 'modem_1_1_2 wan wan6'
option input 'ACCEPT'
option forward 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option target 'ACCEPT'
list icmp_type 'echo-request'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option dest '*'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-reply'
list icmp_type 'echo-request'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
option src 'wan'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config forwarding
option dest 'wan'
option src 'lan'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
config rule
list proto 'tcp'
list dest_ip 'ddb8:e751:40c6::360'
option dest_port '8123'
option src 'wan'
option name 'test'
option dest 'lan'
option target 'ACCEPT'
option src_port '8123'
option family 'ipv6'
Use builtin IPv6-management in Lan and DHCPv6 client in WAN6 was checked.
1 Like
trendy
June 3, 2021, 10:48am
2
You can tell them on my behalf that they are ridiculous and the shame of telecoms.ip6tables-save -c -t nat
# Generated by ip6tables-save v1.8.3 on Thu Jun 3 11:06:24 2021
*nat
:PREROUTING ACCEPT [6548:1251365]
:INPUT ACCEPT [389:33087]
:OUTPUT ACCEPT [136:12645]
:POSTROUTING ACCEPT [2:320]
:GL_SPEC_DMZ - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[6551:1251607] -A PREROUTING -j GL_SPEC_DMZ
[6551:1251607] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[6551:1251607] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i 3g-modem_1_1_2 -m comment --comment "!fw3" -j zone_wan_prerouting
[136:12645] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[2:320] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
[134:12325] -A POSTROUTING -o 3g-modem_1_1_2 -m comment --comment "!fw3" -j zone_wan_postrouting
[2:320] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[6551:1251607] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[134:12325] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Thu Jun 3 11:06:24 2021
無線區域網路介面卡 Wi-Fi:
連線特定 DNS 尾碼 . . . . . . . . : lan
IPv6 位址. . . . . . . . . . . . .: ddb8:e751:40c6::8fc
IPv6 位址. . . . . . . . . . . . .: ddb8:e751:40c6:0:b4d2:c3:ec9b:4577
臨時 IPv6 位址. . . . . . . . . . : ddb8:e751:40c6:0:d851:7142:16bf:d509
連結-本機 IPv6 位址 . . . . . . . : fe80::b4d2:c3:ec9b:4577%7
IPv4 位址 . . . . . . . . . . . . : 192.168.50.172
子網路遮罩 . . . . . . . . . . . .: 255.255.255.0
預設閘道 . . . . . . . . . . . . .: fe80::9683:c4ff:fe09:a5ab%7
192.168.50.1
I have called the customer services but they just answered there is no such an option they can do for me. I have to find another way out.
I have added two ip6tables rules in firewall custom rules but still not working.
force_dns() {
# lanip=$(ifconfig br-lan |sed -n 's/.*dr:\(.*\) Bc.*/\1/p')
lanip=$(uci get network.lan.ipaddr)
tor=$(ps|grep /usr/sbin/tor|grep -v grep)
[ "$1" = "add" ] && {
ip=$(uci get glconfig.general.ipaddr)
[ -z "$ip" ] && ip=$(uci get network.lan.ipaddr)
iptables -t nat -D PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $ip
iptables -t nat -D PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $ip
uci set glconfig.general.ipaddr=$lanip
uci commit glconfig
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
if [ -n "$tor" ];then
iptables -t nat -C PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
iptables -t nat -C PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
fi
}
[ "$1" = "remove" ] && {
lanip=$(uci get glconfig.general.ipaddr)
[ -z "$lanip" ] && lanip=$(uci get network.lan.ipaddr)
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
[ "$?" = "0" ] && iptables -t nat -D PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
[ "$?" = "0" ] && iptables -t nat -D PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
if [ -n "$tor" ];then
iptables -t nat -D PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
iptables -t nat -D PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
fi
}
}
force=$(uci get glconfig.general.force_dns)
if [ -n "$force" ]; then
force_dns add
else
force_dns remove
fi
gl-firewall
# PPTP Passthrough
iptables -t raw -D OUTPUT -p tcp -m tcp --dport 1723 -j CT --helper pptp
iptables -t raw -A OUTPUT -p tcp -m tcp --dport 1723 -j CT --helper pptp
ip6tables -t nat -A prerouting_wan_rule -p tcp -m tcp --dport 8123 -j DNAT --to-destination [fe80::9cec:e95a:417f:4312]:8123
ip6tables -t filter -A forwarding_wan_rule -m conntrack --ctstate DNAT -j ACCEPT
It's still the same.
force_dns() {
# lanip=$(ifconfig br-lan |sed -n 's/.*dr:\(.*\) Bc.*/\1/p')
lanip=$(uci get network.lan.ipaddr)
tor=$(ps|grep /usr/sbin/tor|grep -v grep)
[ "$1" = "add" ] && {
ip=$(uci get glconfig.general.ipaddr)
[ -z "$ip" ] && ip=$(uci get network.lan.ipaddr)
ip6tables -t nat -D PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $ip
ip6tables -t nat -D PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $ip
uci set glconfig.general.ipaddr=$lanip
uci commit glconfig
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
if [ -n "$tor" ];then
iptables -t nat -C PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
iptables -t nat -C PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
[ ! "$?" = "0" ] && iptables -t nat -I PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
fi
}
[ "$1" = "remove" ] && {
lanip=$(uci get glconfig.general.ipaddr)
[ -z "$lanip" ] && lanip=$(uci get network.lan.ipaddr)
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
[ "$?" = "0" ] && ip6tables -t nat -D PREROUTING -i br-+ -s 0/0 -p udp --dport 53 -j DNAT --to $lanip
iptables -t nat -C PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
[ "$?" = "0" ] && ip6tables -t nat -D PREROUTING -i br-+ -s 0/0 -p tcp --dport 53 -j DNAT --to $lanip
if [ -n "$tor" ];then
ip6tables -t nat -D PREROUTING -i br-lan -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 9053
ip6tables -t nat -D PREROUTING -i br-lan -p udp -m udp --dport 53 -j REDIRECT --to-ports 9053
fi
}
}
force=$(uci get glconfig.general.force_dns)
if [ -n "$force" ]; then
force_dns add
else
force_dns remove
fi
gl-firewall
# PPTP Passthrough
iptables -t raw -D OUTPUT -p tcp -m tcp --dport 1723 -j CT --helper pptp
iptables -t raw -A OUTPUT -p tcp -m tcp --dport 1723 -j CT --helper pptp
ip6tables -t nat -A prerouting_wan_rule -p tcp -m tcp --dport 8123 -j DNAT --to-destination [fe80::9cec:e95a:417f:4312]:8123
ip6tables -t filter -A forwarding_wan_rule -m conntrack --ctstate DNAT -j ACCEPT
config include 'custom'
option reload '1'
option path '/etc/firewall.user'
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'modem_1_1_2 wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option target 'ACCEPT'
list icmp_type 'echo-request'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config forwarding
option dest 'wan'
option src 'lan'
config rule
option src_port '8123'
option src 'wan'
option name 'test'
option target 'ACCEPT'
option dest 'lan'
list dest_ip 'fe80::9cec:e95a:417f:4312'
option dest_port '8123'
list proto 'tcp'
option family 'ipv6'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
# Generated by ip6tables-save v1.8.3 on Thu Jun 3 13:45:52 2021
*nat
:PREROUTING ACCEPT [3933:767522]
:INPUT ACCEPT [417:35370]
:OUTPUT ACCEPT [150:13312]
:POSTROUTING ACCEPT [0:0]
:GL_SPEC_DMZ - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[3933:767522] -A PREROUTING -j GL_SPEC_DMZ
[3933:767522] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[3932:767442] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
[1:80] -A PREROUTING -i 3g-modem_1_1_2 -m comment --comment "!fw3" -j zone_wan_prerouting
[150:13312] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
[150:13312] -A POSTROUTING -o 3g-modem_1_1_2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[3932:767442] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[150:13312] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[1:80] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
uci reorder firewall.nat6="0"
uci commit firewall
/etc/init.d/firewall restart
After I restart firewall, there is some warning.
-----------------------------------------------------
root@GL-XE300:~# uci reorder firewall.nat6="0"
root@GL-XE300:~# uci commit firewall
root@GL-XE300:~# /etc/init.d/firewall restart
Warning: Option @zone[1].masq6 is unknown
Warning: Option 'sambasharewan'.dest_proto is unknown
Warning: Section 'sambasharewan' does not specify a protocol, assuming TCP+UDP
Warning: Option 'sambasharelan'.dest_proto is unknown
Warning: Section 'sambasharelan' does not specify a protocol, assuming TCP+UDP
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv4 raw table
* Flushing IPv6 filter table
* Flushing IPv6 nat table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-ISAKMP'
* Rule 'Allow-IPSec-ESP'
* Rule #8
* Rule #9
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 nat table
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 raw table
* Zone 'lan'
- Using automatic conntrack helper attachment
* Zone 'wan'
* Populating IPv6 filter table
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ISAKMP'
* Rule 'Allow-IPSec-ESP'
* Rule #8
* Rule #9
* Rule 'test'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 nat table
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_lan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_wan_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'prerouting_rule'
Warning: fw3_ipt_rule_append(): Can't find target 'postrouting_rule'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.nat6'
nat6: Firewall config="cfg04dc81" zone="lan" zone_masq6="0".
nat6: Firewall config="cfg05dc81" zone="wan" zone_masq6="1".
nat6: Found firewall zone_name="wan" with zone_masq6="1" zone_masq6_privacy="1".
nat6: Setting up masquerading nat6 for zone_name="wan" with zone_masq6_privacy=" 1"
nat6: Ensuring ip6tables chain="zone_wan_postrouting" contains our MASQUERADE.
nat6: Ensuring ip6tables chain="zone_wan_input" contains our permissive DNAT rul e.
nat6: Ensuring ip6tables chain="zone_wan_forward" contains our permissive DNAT r ule.
nat6: Done setting up nat6 for zone="wan" on devices:
* Running script '/etc/firewall.user'
uci: Entry not found
uci: Entry not found
iptables: No chain/target/match by that name.
iptables: No chain/target/match by that name.
ipset v7.3: The set with the given name does not exist
iptables: No chain/target/match by that name.
iptables: No chain/target/match by that name.
* Running script '/var/etc/gls2s.include'
! Skipping due to path error: No such file or directory
* Running script '/usr/bin/glfw.sh'
* Running script '/usr/sbin/glqos.sh'
The interface of 'modem_1_1_2' was the source of sim card, and 'WAN6' is the interface where I get the IPv6 address. Does that different name affect my setting rules?
Set your modem to bridge mode so OpenWrt can get the /64 prefix.
The interface 'modem1_1_2' is built in the GL-XE300 router, I don't have an extra modem.
Finally, the port was opened successfully. But one more dumb question.
trendy
June 8, 2021, 11:50am
14
Did you save them in the firewall script ?
Thanks, it saved in script successfully.http://www.ipv6scanner.com/cgi-bin/main.py " and it shows open. But it still not work.
trendy
June 8, 2021, 3:21pm
16
What is the output of ip6tables-save -c | grep DNAT
root@GL-XE300:~# ip6tables-save -c | grep DNAT
[0:0] -A prerouting_wan_rule -p tcp -m tcp --dport 8123 -j DNAT --to-destination [ddb8:e751:40c6::50]:8123
[0:0] -A prerouting_wan_rule -p tcp -m tcp --dport 8123 -j DNAT --to-destination [ddb8:e751:40c6::50]:8123
[0:0] -A forwarding_wan_rule -m conntrack --ctstate DNAT -j ACCEPT
[0:0] -A forwarding_wan_rule -m conntrack --ctstate DNAT -j ACCEPT
root@GL-XE300:~#
I don't known why there is double rules of the output.
trendy
June 8, 2021, 3:50pm
18
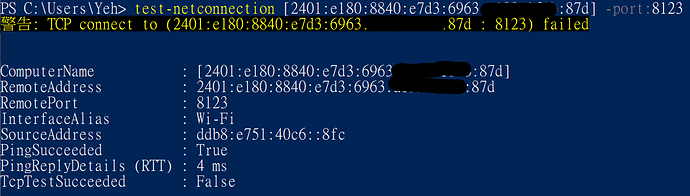
There is no hit on the firewall. Are you running this test from the internet or from inside the lan?
1 Like
I run the test inside the lan.