Hi Trendy,
Thanks. See below.
Ramon
{
"kernel": "5.4.67",
"hostname": "OpenWrt2",
"system": "ARMv7 Processor rev 0 (v7l)",
"model": "Netgear Nighthawk X4S R7800",
"board_name": "netgear,r7800",
"release": {
"distribution": "OpenWrt",
"version": "SNAPSHOT",
"revision": "r14553-7dc78d1d28",
"target": "ipq806x/generic",
"description": "OpenWrt SNAPSHOT r14553-7dc78d1d28"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'XXXXXXXXXXX::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.15.2'
option gateway '192.168.15.1'
list dns '192.168.15.1'
option delegate '0'
option ifname 'eth1.1'
option ip6assign '64'
option stp '1'
option igmp_snooping '1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '1t 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 5'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '1t 6t'
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.20.2'
option type 'bridge'
option ifname 'eth1.3'
list dns '192.168.20.1'
option delegate '0'
option ip6assign '64'
option macaddr 'XX:XX:XX:XX:XX:XX'
option gateway '192.168.20.1'
option stp '1'
option igmp_snooping '1'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'soc/1b500000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option log_level '0'
option legacy_rates '0'
option htmode 'VHT160'
option country 'XX'
option distance '200'
option rts '500'
option channel '36'
option txpower '23'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option auth_secret 'XXXXX'
option auth_port '1812'
option ssid 'XXXXX'
option wpa_disable_eapol_key_retries '1'
option ieee80211w '2'
option encryption 'wpa2+ccmp'
option ieee80211k '1'
option ieee80211v '1'
option bss_transition '1'
option time_advertisement '2'
option time_zone 'XXXXXXXXXXX'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option eap_reauth_period '0'
option skip_inactivity_poll '1'
option auth_server '192.168.15.65'
option ft_bridge 'br-lan'
option nasid 'XXXXXXX'
option ieee80211r '1'
option mobility_domain 'XXXX'
option ft_over_ds '1'
option ft_psk_generate_local '0'
option r1_key_holder 'XXXXXXX'
option pmk_r1_push '1'
list r0kh ' ff:ff:ff:ff:ff:ff,*,XXXXXX'
list r1kh '00:00:00:00:00:00,00:00:00:00:00:00,XXXXXX'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'soc/1b700000.pci/pci0001:00/0001:00:00.0/0001:01:00.0'
option htmode 'HT20'
option channel '1'
option log_level '0'
option legacy_rates '0'
option country 'XX'
option distance '200'
option rts '500'
option txpower '15'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'XXX'
option wpa_disable_eapol_key_retries '1'
option ieee80211w '2'
option ieee80211k '1'
option ieee80211v '1'
option bss_transition '1'
option time_advertisement '2'
option time_zone 'XXXXX'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '1'
option encryption 'wpa2+ccmp'
option auth_port '1812'
option auth_secret 'XXXX'
option eap_reauth_period '0'
option skip_inactivity_poll '1'
option auth_server '192.168.15.XX'
option ft_bridge 'br-lan'
option nasid 'XXXXXXX'
option ieee80211r '1'
option mobility_domain 'XXXX'
option ft_over_ds '1'
option ft_psk_generate_local '0'
option r1_key_holder 'XXXXXXXXXX'
list r0kh 'ff:ff:ff:ff:ff:ff,*,XXXXXXX'
list r1kh '00:00:00:00:00:00,00:00:00:00:00:00,XXXX'
option pmk_r1_push '1'
config wifi-iface 'wifinet2'
option network 'guest'
option device 'radio0'
option mode 'ap'
option key 'XX'
option ssid 'XXXXXXXXXXXXXX'
option isolate '1'
option ieee80211k '1'
option ieee80211v '1'
option bss_transition '1'
option encryption 'psk2+ccmp'
option ft_bridge 'br-lan'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '0'
option time_advertisement '2'
option time_zone 'XXXXXXXXXXXXX'
option skip_inactivity_poll '1'
option ieee80211r '1'
option ft_over_ds '1'
option ft_psk_generate_local '1'
config wifi-iface 'wifinet3'
option network 'guest'
option device 'radio1'
option mode 'ap'
option key 'XXXXXXXXXXX'
option ssid 'XXXXXXXXX'
option isolate '1'
option ieee80211k '1'
option ieee80211v '1'
option bss_transition '1'
option encryption 'psk2+ccmp'
option ft_bridge 'br-lan'
option wnm_sleep_mode '1'
option wnm_sleep_mode_no_keys '0'
option time_advertisement '2'
option time_zone 'XXXXXXXXXX'
option skip_inactivity_poll '1'
option ieee80211r '1'
option ft_over_ds '1'
option ft_psk_generate_local '1'
config wifi-iface 'wifinet4'
option device 'radio0'
option mode 'ap'
option key 'XXXXXXXXXXXXXXX'
option ft_over_ds '1'
option ft_bridge 'br-lan'
option ssid 'XXXXXXXXXXXX'
option ieee80211r '1'
option ft_psk_generate_local '1'
option network 'guest'
option encryption 'psk2+ccmp'
option skip_inactivity_poll '1'
option nasid 'XXXXXXXXXXXXXXXXX'
config wifi-iface 'wifinet5'
option ssid 'XXX'
option device 'radio1'
option mode 'ap'
option key 'XXXXXXXXXXXXX'
option ft_over_ds '1'
option ft_bridge 'lan'
option ieee80211r '1'
option ft_psk_generate_local '1'
option network 'guest'
option encryption 'psk2+ccmp'
option skip_inactivity_poll '1'
option nasid 'XXXXXXXXXXXXXXXXX'
package dhcp
config dnsmasq
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option filterwin2k '1'
list server '192.168.15.1'
list server '192.168.20.1'
option boguspriv '0'
option resolvfile '/tmp/resolv.conf'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option ignore '1'
package firewall
config defaults
option output 'ACCEPT'
option drop_invalid '1'
option forward 'REJECT'
option input 'REJECT'
option synflood_protect '1'
config include
option path '/etc/firewall.user'
config zone
option name 'lan'
option input 'ACCEPT'
option network 'lan'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'guest'
option output 'ACCEPT'
option network 'guest'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option dest 'guest'
option src 'lan'
config rule
option dest_port '53'
option name 'allow guest dns'
option target 'ACCEPT'
option src 'guest'
config rule
option dest_port '67-68'
option name 'allow guest dhcp'
option target 'ACCEPT'
option src 'guest'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
option family 'IPv4'
option reload '1'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
47: br-guest: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.20.2/24 brd 192.168.20.255 scope global br-guest
valid_lft forever preferred_lft forever
49: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.15.2/24 brd 192.168.15.255 scope global br-lan
valid_lft forever preferred_lft forever
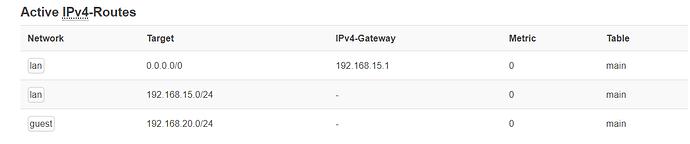
default via 192.168.15.1 dev br-lan proto static
192.168.15.0/24 dev br-lan proto kernel scope link src 192.168.15.2
192.168.20.0/24 dev br-guest proto kernel scope link src 192.168.20.2
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.15.0 dev br-lan table local proto kernel scope link src 192.168.15.2
local 192.168.15.2 dev br-lan table local proto kernel scope host src 192.168.15.2
broadcast 192.168.15.255 dev br-lan table local proto kernel scope link src 192.168.15.2
broadcast 192.168.20.0 dev br-guest table local proto kernel scope link src 192.168.20.2
local 192.168.20.2 dev br-guest table local proto kernel scope host src 192.168.20.2
broadcast 192.168.20.255 dev br-guest table local proto kernel scope link src 192.168.20.2
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Sep 25 04:31 /etc/resolv.conf -> /tmp/resolv.conf
lrwxrwxrwx 1 root root 35 Sep 25 18:20 /tmp/resolv.conf -> /tmp/resolv.conf.d/resolv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 82 Oct 22 11:14 resolv.conf.auto
==> /etc/resolv.conf <==
# Interface guest
nameserver 192.168.20.1
# Interface lan
nameserver 192.168.15.1
==> /tmp/resolv.conf <==
# Interface guest
nameserver 192.168.20.1
# Interface lan
nameserver 192.168.15.1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error