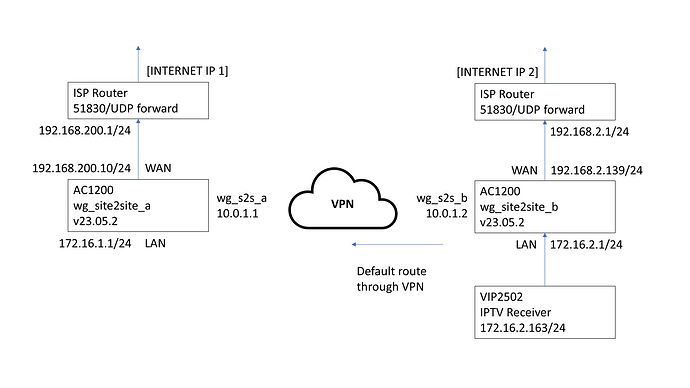
Hello all. I have an openwrt Wireguard VPN setup and trying to run an IPTV receiver through that VPN. I have openwrt routers managing both ends of the VPN. The IPTV endpoint receiver device cannot receive the IPTV feed, I suspect from my research its related to multicast / IGMP support. I would appreciate some advice on how to get this up and running. I've installed IGMPproxy and enabled multicast on my Wireguard interfaces and haven't done any further changes yet as unsure of next steps.
My setup:
Site A:/etc/config/network
root@wg_site2site_a:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdff:ffff:ffff::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan'
option igmp_snooping '1'
config device
option name 'lan'
option macaddr 'xx'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '172.16.1.1'
option netmask '255.255.255.0'
config device
option name 'wan'
option macaddr 'xx'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option metric '1024'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option peerdns '0'
list dns '2001:4860:4860::8888'
list dns '2001:4860:4860::8844'
config interface 'wg_s2s_a'
option proto 'wireguard'
option private_key 'xx'
option listen_port '51830'
list addresses '10.0.1.1/24'
config wireguard_wg_s2s_a 's2s_vpn_site_b'
option public_key 'xx'
option preshared_key 'xx'
option description 'Site B'
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '172.16.2.0/24'
list allowed_ips 'fdee:eeee:eeee::/48'
list allowed_ips '10.0.1.2/32'
option private_key 'xx'
config wireguard_wg_s2s_a 's2s_vpn_site_c'
option description 'Site C'
option public_key 'xx'
option preshared_key 'xx'
list allowed_ips '172.16.3.0/24'
list allowed_ips 'fdee:ffff:ffff::/48'
list allowed_ips '10.0.1.3/32'
option private_key 'xx'
option route_allowed_ips '1'
option persistent_keepalive '25'
config device
option name 'wg_s2s_a'
option multicast '1'
Site B:/etc/config/network
root@wg_site2site_b:/etc/config# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdee:eeee:eeee::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan'
option igmp_snooping '1'
config device
option name 'lan'
option macaddr 'xx'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '172.16.2.1'
option netmask '255.255.255.0'
config device
option name 'wan'
option macaddr 'xx'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option metric '1024'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option peerdns '0'
list dns '2001:4860:4860::8888'
list dns '2001:4860:4860::8844'
config interface 'wg_s2s_b'
option proto 'wireguard'
option private_key 'xx'
option listen_port '51830'
list addresses '10.0.1.2/24'
config wireguard_wg_s2s_b 's2s_vpn_site_a'
option public_key 'xx'
option preshared_key 'xx'
option description 'Site A'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host 'xx'
option endpoint_port '51830'
list allowed_ips '172.16.1.0/24'
list allowed_ips '10.0.1.1/32'
list allowed_ips '0.0.0.0/0'
config device
option name 'wg_s2s_b'
option multicast '1'
Site A:/etc/config/igmpproxy
root@wg_site2site_a:~# cat /etc/config/igmpproxy
config igmpproxy
option quickleave 1
# option verbose [0-3](none, minimal[default], more, maximum)
config phyint
option network wan
option zone wan
option direction upstream
# list altnet 192.168.1.0/24
list altnet 0.0.0.0/0
config phyint
option network lan
option zone lan
option direction downstream
Site B:/etc/config/igmpproxy
root@wg_site2site_b:~# cat /etc/config/igmpproxy
config igmpproxy
option quickleave 1
# option verbose [0-3](none, minimal[default], more, maximum)
config phyint
option network wan
option zone wan
option direction upstream
# list altnet 192.168.1.0/24
list altnet 0.0.0.0/0
config phyint
option network lan
option zone lan
option direction downstream
Site A:/etc/config/firewall (only showing IGMP reference)
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
Site B:/etc/config/firewall (only showing IGMP reference)
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'