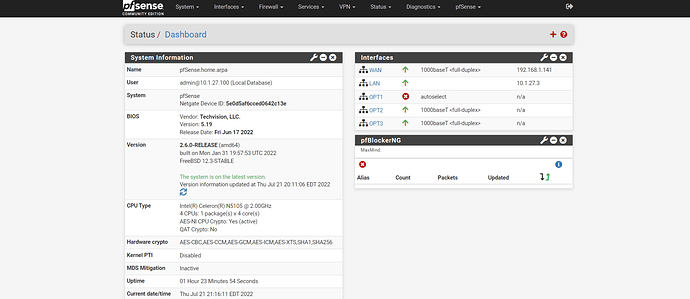
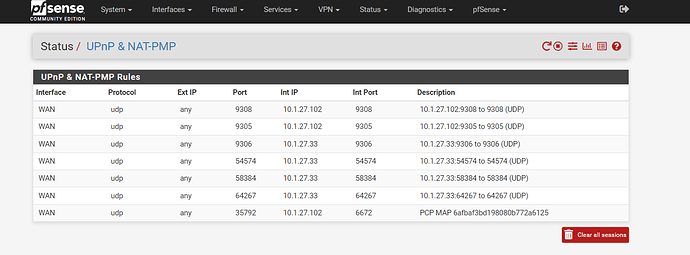
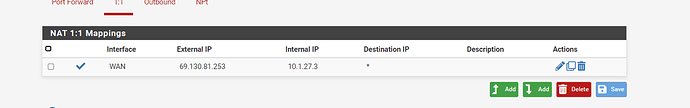
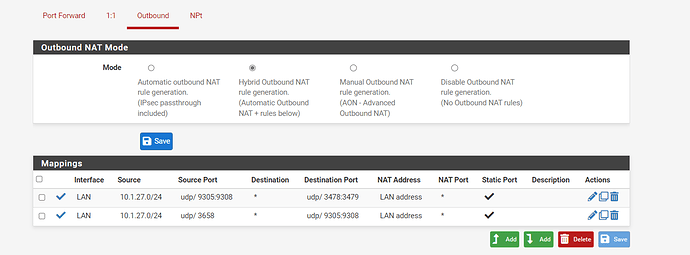
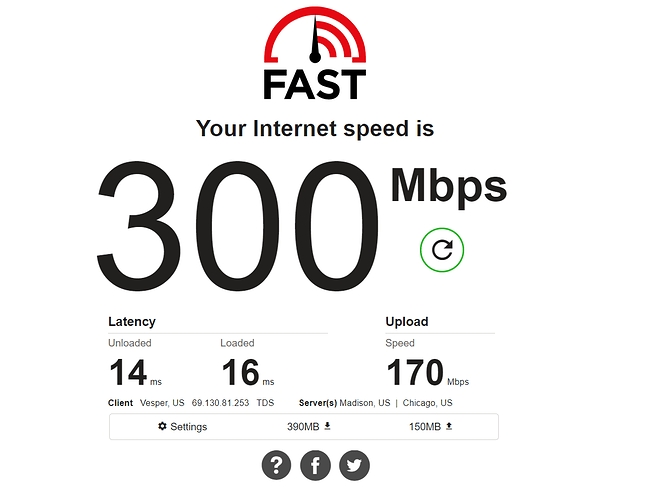
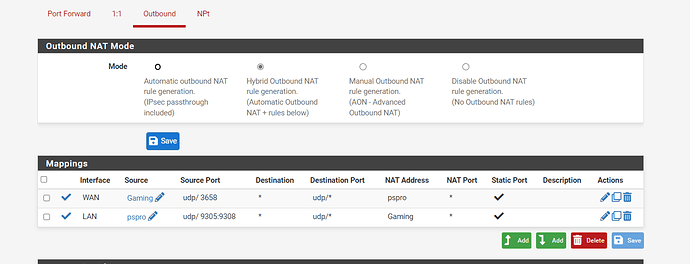
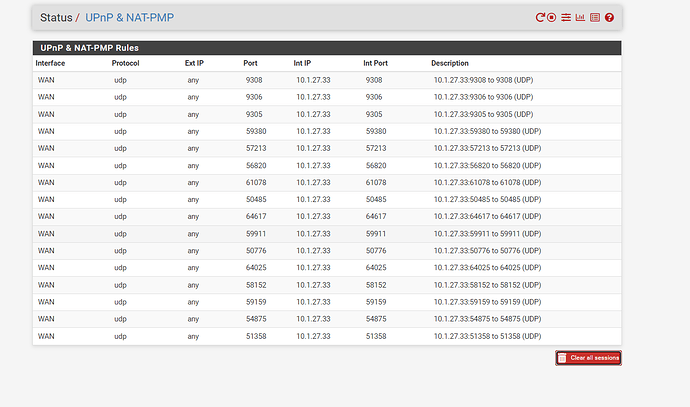
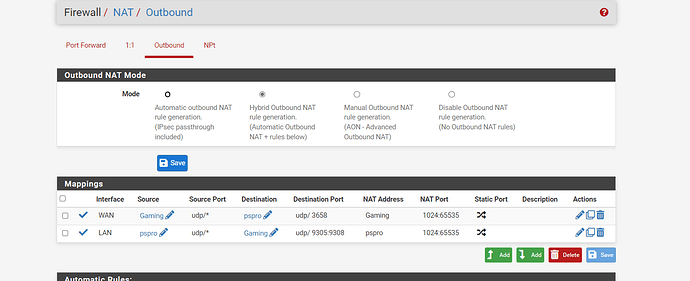
well ok but my network is complex i guess... so here is what i use for dscp marks
/root/dscp.sh
#!/bin/bash -x
IPT="iptables"
# Latency Sensitive (CS7, CS6, EF, VA, CS5, CS4)
# Streaming Media (AF4x, AF3x, CS3, AF2x, TOS4, CS2, TOS1)
# Best Effort (CS0, AF1x, TOS2, and those not specified)
# Background Traffic (CS1)
$IPT -t mangle -N dscp_mark > /dev/null 2>&1
$IPT -t mangle -F dscp_mark
$IPT -t mangle -A dscp_mark -i wan -j DSCP --set-dscp-class CS0
iptmark(){
$IPT -t mangle -A dscp_mark "$@"
}
## check if POSTROUTING already exits then jumps to our tables if not, add them
$IPT -t mangle -L POSTROUTING -n | grep dscp_mark || $IPT -t mangle -A POSTROUTING -j dscp_mark
sport1="3658"
sport2="9305:9308"
sport3="3074:3079"
sport4="3478:3479"
dport1="3478:3479"
dport2="9305:9308"
dport3="1117,1247,3074:3079,3893,7130,7463"
$IPT -t mangle -A PREROUTING -m set --match-set latsens srcip,srcport,dstip,dstport -j DSCP --set-dscp-class CS4 ## set dscp tag for our (latsens) ipset
$IPT -t mangle -A PREROUTING -m set --match-set streaming srcip,srcport,dstip,dstport -j DSCP --set-dscp-class AF32 ## set dscp tag for our (streaming) ipset
$IPT -t mangle -A PREROUTING -m set --match-set usrcdn srcip,srcport,dstip,dstport -j DSCP --set-dscp-class CS1 ## set dscp tag for our (usrcdn) ipset
$IPT -t mangle -A PREROUTING -p tcp -m set --match-set bulk srcip,srcport,dstip,dstport -j DSCP --set-dscp-class CS0 ## set dscp tag for our (bulk) ipset
$IPT -t mangle -A PREROUTING -m set --match-set network srcip,srcport,dstip,dstport -j DSCP --set-dscp-class CS3 ## set dscp tag for our (network) ipset
$IPT -t mangle -A PREROUTING -p udp -s 192.168.1.186 ! --dport 443 -m comment --comment "PS4 Pro Device" -j DSCP --set-dscp-class CS4
$IPT -t mangle -A PREROUTING -p udp -m udp -m multiport --sports $sport4 -j DSCP --set-dscp-class AF41 -m comment --comment "psn gaming ports"
$IPT -t mangle -A PREROUTING -p udp -m udp -m multiport --dports $dport1 -j DSCP --set-dscp-class AF41 -m comment --comment "psn gaming ports"
$IPT -t mangle -A PREROUTING -p udp -m udp -m multiport --sports $sport1,$sport2,$sport3 -j DSCP --set-dscp-class CS4 -m comment --comment "psn gaming ports"
$IPT -t mangle -A PREROUTING -p udp -m udp -m multiport --dports $dport2,$dport3 -j DSCP --set-dscp-class CS4 -m comment --comment "psn gaming ports"
# mark connections that go over 125 packets per second, not prioritized
iptmark -p udp -m hashlimit --hashlimit-name udp_high_prio --hashlimit-above 125/sec --hashlimit-burst 50 --hashlimit-mode srcip,srcport,dstip,dstport -j CONNMARK --set-mark 0x25 -m comment --comment "connmark for udp"
iptmark -p udp -m udp -m connmark ! --mark 0x25 -m connbytes --connbytes :940 --connbytes-dir both --connbytes-mode avgpkt -j DSCP --set-dscp-class CS4 -m comment --comment "small udp connection gets CS4"
iptmark -p tcp -m hashlimit --hashlimit-name tcp_low_prio --hashlimit-above 125/second --hashlimit-burst 50 --hashlimit-mode srcip,srcport,dstip,dstport --hashlimit-rate-match --hashlimit-rate-interval 1 -j DSCP --set-dscp-class CS1 -m comment --comment "big tcp connection gets CS1"
iptmark -p tcp -m set --match-set bulk srcip,srcport,dstip,dstport -j DSCP --set-dscp-class CS1 -m comment --comment "bulk traffic ipset"
iptmark -p tcp -m connbytes --connbytes 9375:187500 --connbytes-dir both --connbytes-mode bytes -j DSCP --set-dscp-class CS1
iptmark -p tcp -m connbytes --connbytes 187500: --connbytes-dir both --connbytes-mode bytes -j DSCP --set-dscp-class CS0
ackrate=125
iptmark -p tcp -m tcp --tcp-flags ALL ACK -o wan -m length --length 1:100 -m hashlimit --hashlimit-mode srcip,srcport,dstip,dstport --hashlimit-name ackfilter1 --hashlimit-above "${ackrate}/second" --hashlimit-burst $ackrate --hashlimit-rate-match --hashlimit-rate-interval 1 -m statistic --mode random --probability .5 -j DROP
iptmark -p tcp -m tcp --tcp-flags ALL ACK -o wan -m length --length 1:100 -m hashlimit --hashlimit-mode srcip,srcport,dstip,dstport --hashlimit-name ackfilter2 --hashlimit-above "$((ackrate*2))/second" --hashlimit-burst $ackrate --hashlimit-rate-match --hashlimit-rate-interval 1 -m statistic --mode random --probability .5 -j DROP
iptmark -p tcp -m tcp --tcp-flags ALL ACK -o wan -m length --length 1:100 -m hashlimit --hashlimit-mode srcip,srcport,dstip,dstport --hashlimit-name ackfilter3 --hashlimit-above "$((ackrate*3))/second" --hashlimit-burst $ackrate --hashlimit-rate-match --hashlimit-rate-interval 1 -m statistic --mode random --probability .5 -j DROP
iptmark -p tcp -m tcp --tcp-flags ALL ACK -o wan -m length --length 1:100 -m hashlimit --hashlimit-mode srcip,srcport,dstip,dstport --hashlimit-name ackfilter4 --hashlimit-above "$((ackrate*4))/second" --hashlimit-burst $ackrate --hashlimit-rate-match --hashlimit-rate-interval 1 -m statistic --mode random --probability .5 -j DROP
iptmark -p tcp -m tcp --tcp-flags ALL SYN -m length --length 0:500 -j DSCP --set-dscp-class CS4
iptmark -p tcp -m tcp --tcp-flags ALL ACK -m length --length 0:250 -j DSCP --set-dscp-class CS4
iptmark -m dscp ! --dscp 24 -m dscp ! --dscp 18 -m dscp ! --dscp 34 -m dscp ! --dscp 40 -m dscp ! --dscp 48 -m length --length 0:500 -j DSCP --set-dscp-class CS4 -m comment --comment "Flow contol AF32"
iptmark -m dscp ! --dscp 24 -m dscp ! --dscp 18 -m dscp ! --dscp 34 -m dscp ! --dscp 40 -m dscp ! --dscp 48 -m connbytes --connbytes 0:250 --connbytes-dir both --connbytes-mode avgpkt -j DSCP --set-dscp-class CS4 -m comment --comment "multi purpose connection gets AF32"
iptmark -p udp -m udp -m multiport --dports 53,5300 -m set ! --match-set network dstip,dstport -j DSCP --set-dscp-class CS3 -m comment --comment "dns connection and network ipset gets CS3"
iptmark -p udp -m udp -m multiport --sports 53,5300 -m set ! --match-set network srcip,srcport -j DSCP --set-dscp-class CS3 -m comment --comment "dns connection and network ipset gets CS3"
iptmark -p udp -m udp -m multiport --port 123 -j DSCP --set-dscp-class CS5 -m comment --comment "NTP udp"
iptmark -p icmp -j DSCP --set-dscp-class CS5 -m comment --comment "ICMP-pings"
this is dnsmasq for ipsets mostly is used to make netflix,youtube etc bulk
/etc/dnsmasq.conf
##CS4
ipset=/*.hardsuitlabs.com/latsens
##CS3
ipset=/abdlwi.broadband.dynamic.tds.net/*.dynamic.tds.net/*.cncrtn.broadband.dynamic.tds.net/*.tds.net/*.dynamic.tds.net/network
ipset=/pspro.lan/Fortune-3.lan/network
##CS1
ipset=/googletagmanager.com/googleusercontent.com/clients4.google.com/*.googleusercontent.com/google.com/static.xx.fbcdn.net/fbcdn.net/*.fbcdn.net/akamaihd.net/*.akamaihd.net/whatsapp.net/*.whatsapp.net/whatsapp.com/*.whatsapp.com/www-cdn.whatsapp.net/googleapis.com/*.googleapis.com/ucy.ac.cy/1e100.net/hwcdn.net/usrcdn
##CS0
# Youtube is also isolated by my isp
ipset=/cdn1-gae-ssl-default.akamaized.net/play-fe.googleapis.com/android.googleapis.com/chief-cdn.storage.googleapis.com/g.live.com/googlevideo.com/*.googlevideo.com/rr1---sn-vgqskned.googlevideo.com/rr2---sn-vgqskned.googlevideo.com/rr3---sn-vgqskned.googlevideo.com/rr4---sn-vgqskned.googlevideo.com/bulk
# AmazonVideo
ipset=/s3.ll.dash.row.aiv-cdn.net/aiv-delivery.net/amazonaws.com//api.amazonalexa.com/*.amazonalexa.com/bulk
#tiktok
ipset=/*.tiktok.*/frontier.us.tiktokv.com/*.us.tiktokv.com/bulk
### Tivo
ipset=/sage-hec.oi.tivo.com/mm3.tivoservice.com/*.tivoservice.com/control2.tvinteractive.tv/*.tvinteractive.tv/bulk
## PSN Download
ipset=/party.rnps.dl.playstation.net/gs2.ww.prod.dl.playstation.net/clientsettingscdn.roblox.com/ecsv2.roblox.com/*.roblox.com/*.ubisoft.com/theia.dl.playstation.net/bulk
##pluto t.v.
ipset=/cloudfront.tubi.video/s.adrise.tv/events.cid.samba.tv/*.samba.tv/t.pluto.tv/service-stitcher.clusters.pluto.tv/siloh-fs.plutotv.net/plutotv.com/k.pluto.tv/siloh.pluto.tv/*.pluto.tv/lds-ldr-production.tvinteractive.tv/tvmeta-dynamic.tvinteractive.tv/events.cid.samba.tv/bulk
#Netflix
ipset=/cdn-0.nflximg.com/*.nflximg.com/*nflxvideo*/nrdp.prod.ftl.netflix.com/secure.netflix.com/api-global.netflix.com/*.netflix.com/*.1.oca.nflxvideo.net/nrdp-ipv6.prod.ftl.netflix.com/*.1.nflxso.net/bulk
##Guest devices
ipset=/Bedroom.lan/sonytv.lan/bulk
###EA games
ipset=/river.data.ea.com/*.ea.com/bulk
and qosify
defaults-00
# SSH
tcp:22 network_services
# NTP
udp:123 network_services
# DNS
tcp:53 network_services
tcp:5300 network_services
udp:53 network_services
udp:5300 network_services
# DNS over TLS (DoT)
tcp:853 multimedia_conferencing
udp:853 multimedia_conferencing
# HTTP/HTTPS/QUIC
tcp:80 browsing
tcp:443 browsing
#udp:80 browsing
#udp:443 browsing
# Microsoft (Download)
dns:*1drv* bulk
dns:*backblaze* bulk
dns:*backblazeb2* bulk
dns:*ms-acdc.office* bulk
dns:*onedrive* bulk
dns:*sharepoint* bulk
dns:*update.microsoft* bulk
dns:*windowsupdate* bulk
# Custom
dns:*.hardsuitlabs.com gaming
dns:*.broadband.dynamic.tds.net network_services
dns:*.dynamic.tds.net network_services
dns:*.ea.com bulk
dns:river.data.ea.com bulk
dns:ps4.np.playstation.net network_services
dns:apps.mzstatic.com bulk
dns:*.np.stun.playstation.net network_services
dns:*.cncrtn.broadband.dynamic.tds.net network_services
# MEGA (Download)
dns:*mega* bulk
# Dropbox (Download)
dns:*dropboxusercontent* bulk
# Google (Download)
dns:*drive.google* bulk
dns:*googleusercontent* bulk
# Steam (Download)
dns:*steamcontent* bulk
# Epic Games (Download)
dns:*download.epicgames* bulk
dns:*download2.epicgames* bulk
dns:*download3.epicgames* bulk
dns:*download4.epicgames* bulk
dns:*epicgames-download1* bulk
# YouTube
dns:*googlevideo* besteffort
# Facebook
dns:*fbcdn* besteffort
# Twitch
dns:*ttvnw* besteffort
# TikTok
dns:*tiktok* besteffort
# Netflix
dns:*nflxvideo* besteffort
# Amazon Prime Video
dns:*aiv-cdn* besteffort
dns:*aiv-delivery* besteffort
dns:*pv-cdn* besteffort
# Disney Plus
dns:*disney* besteffort
dns:*dssott* besteffort
# HBO
dns:*hbo* besteffort
dns:*hbomaxcdn* besteffort
# BitTorrent
tcp:6881-7000 bulk
tcp:51413 bulk
udp:6771 bulk
udp:6881-7000 bulk
udp:51413 bulk
# Usenet
tcp:119 bulk
tcp:563 bulk
# Live Streaming to YouTube Live, Twitch, Vimeo and LinkedIn Live
tcp:1935-1936 broadcast_video
tcp:2396 broadcast_video
tcp:2935 broadcast_video
# Xbox
tcp:3074 gaming
udp:88 gaming
#udp:500 gaming # UDP port already used in "VoWiFi" rules
udp:3074 gaming
udp:3544 gaming
#udp:4500 gaming # UDP port already used in "VoWiFi" rules
# PlayStation
tcp:3478-3480 gaming
#udp:3478-3479 gaming # UDP ports already used in "Zoom" rules
udp:9305-9308 gaming
# Call of Duty
#tcp:3074 gaming # TCP port already used in "Xbox" rules
tcp:3075-3076 gaming
#udp:3074 gaming # UDP port already used in "Xbox" rules
udp:3075-3079 gaming
udp:3658 gaming
# FIFA
tcp:3659 gaming
udp:3659 gaming
# Minecraft
tcp:25565 gaming
udp:19132-19133 gaming
udp:25565 gaming
# Supercell Games
tcp:9339 gaming
udp:9339 gaming
# Zoom, Microsoft Teams, Skype and FaceTime (they use these same ports)
udp:3478-3497 multimedia_conferencing
# Zoom
dns:*zoom* multimedia_conferencing
tcp:8801-8802 multimedia_conferencing
udp:8801-8810 multimedia_conferencing
# Skype
dns:*skype* multimedia_conferencing
# FaceTime
udp:16384-16387 multimedia_conferencing
udp:16393-16402 multimedia_conferencing
# GoToMeeting
udp:1853 multimedia_conferencing
udp:8200 multimedia_conferencing
# Webex Meeting
tcp:5004 multimedia_conferencing
udp:9000 multimedia_conferencing
# Jitsi Meet
tcp:5349 multimedia_conferencing
udp:10000 multimedia_conferencing
# Google Meet
udp:19302-19309 multimedia_conferencing
# TeamViewer
tcp:5938 multimedia_conferencing
udp:5938 multimedia_conferencing
# Voice over Internet Protocol (VoIP)
tcp:5060-5061 telephony
udp:5060-5061 telephony
# Voice over WiFi or WiFi Calling (VoWiFi)
udp:500 telephony
udp:4500 telephony
and config
/etc/config/qosify
config defaults
list defaults /etc/qosify/*.conf
option dscp_icmp +besteffort
option dscp_default_tcp unmarked_traffic
option dscp_default_udp unmarked_traffic
config class unmarked_traffic
option ingress CS1
option egress CS1
option prio_max_avg_pkt_len 1256
option dscp_prio CS4
option bulk_trigger_pps 150
option bulk_trigger_timeout 10
option dscp_bulk CS1
config class browsing
option ingress CS0
option egress CS0
option prio_max_avg_pkt_len 575
option dscp_prio AF41
option bulk_trigger_pps 940
option bulk_trigger_timeout 10
option dscp_bulk CS1
config class bulk
option ingress CS1
option egress CS1
config class besteffort
option ingress CS0
option egress CS0
config class network_services
option ingress CS2
option egress CS2
config class broadcast_video
option ingress CS3
option egress CS3
config class gaming
option ingress CS4
option egress CS4
prio_max_avg_pkt_len 940
config class multimedia_conferencing
option ingress AF42
option egress AF42
option prio_max_avg_pkt_len 1000
option dscp_prio AF41
config class telephony
option ingress EF
option egress EF
config interface wan
option name wan
option disabled 0
option bandwidth_up 40mbit #Upload Speed (Use mbit)
option bandwidth_down 250mbit #Download Speed (use mbit)
option overhead_type raw #Overhead type
# defaults:
option ingress 1
option egress 1
option mode diffserv4
option nat 1
option host_isolate 1
option autorate_ingress 0
option ingress_options ""
option egress_options "ack-filter wash"
option options "ether-vlan noatm overhead 22 mpu 64"
logs...
root@OpenWrt:~# qosify-status
===== interface wan: active =====
egress status:
qdisc cake 8001: root refcnt 2 bandwidth 40Mbit diffserv4 dual-srchost nat wash ack-filter split-gso rtt 100ms noatm overhead 22 mpu 64
Sent 326892923 bytes 453069 pkt (dropped 1757, overlimits 458995 requeues 0)
backlog 0b 0p requeues 0
memory used: 364Kb of 4Mb
capacity estimate: 40Mbit
min/max network layer size: 28 / 1472
min/max overhead-adjusted size: 64 / 1494
average network hdr offset: 14
Bulk Best Effort Video Voice
thresh 2500Kbit 40Mbit 20Mbit 10Mbit
target 7.13ms 5ms 5ms 5ms
interval 102ms 100ms 100ms 100ms
pk_delay 4.88ms 156us 95us 700us
av_delay 352us 6us 5us 55us
sp_delay 3us 1us 2us 3us
backlog 0b 0b 0b 0b
pkts 220655 57482 159723 16966
bytes 289124060 9560675 24580955 3791193
way_inds 8 2158 927 1373
way_miss 382 292 8287 803
way_cols 0 0 1 0
drops 23 2 3 1
marks 0 0 0 0
ack_drop 124 105 1498 1
sp_flows 0 0 0 1
bk_flows 0 0 1 0
un_flows 0 0 0 0
max_len 2776 1486 1486 1486
quantum 300 1220 610 305
ingress status:
qdisc cake 8002: root refcnt 2 bandwidth 250Mbit diffserv4 dual-dsthost nat nowash ingress no-ack-filter split-gso rtt 100ms noatm overhead 22 mpu 64
Sent 2616622705 bytes 2000751 pkt (dropped 9116, overlimits 1843540 requeues 0)
backlog 0b 0p requeues 0
memory used: 2854840b of 12500000b
capacity estimate: 250Mbit
min/max network layer size: 46 / 1472
min/max overhead-adjusted size: 68 / 1494
average network hdr offset: 14
Bulk Best Effort Video Voice
thresh 15625Kbit 250Mbit 125Mbit 62500Kbit
target 5ms 5ms 5ms 5ms
interval 100ms 100ms 100ms 100ms
pk_delay 7.84ms 1.7ms 1.06ms 735us
av_delay 3.01ms 152us 45us 32us
sp_delay 1.24ms 6us 2us 2us
backlog 0b 0b 0b 0b
pkts 1663602 287700 45863 12702
bytes 2217100816 396149367 10720461 4905340
way_inds 8 4 167 12
way_miss 340 608 1309 801
way_cols 0 0 0 0
drops 9098 13 3 2
marks 0 0 0 0
ack_drop 0 0 0 0
sp_flows 1 0 1 1
bk_flows 0 1 0 0
un_flows 0 0 0 0
max_len 68356 63898 19318 5630
quantum 476 1514 1514 1514
and bufferbloat
but done with openwrt for the moment now running pfsense!!!!
back to square 1 fun fun fun!!!!
almost forgot this goes in /etc/config/firewall for ipsets to work...
config ipset
option enabled '1'
option name 'latsens'
option storage 'hash'
option match 'ip'
option family 'ipv4'
option timeout '86400'
config ipset
option enabled '1'
option name 'network'
option storage 'hash'
option match 'ip'
option family 'ipv4'
option timeout '86400'
config ipset
option enabled '1'
option name 'streaming'
option storage 'hash'
option match 'ip'
option family 'ipv4'
option timeout '86400'
config ipset
option enabled '1'
option name 'usrcdn'
option storage 'hash'
option match 'ip'
option family 'ipv4'
option timeout '86400'
config ipset
option enabled '1'
option name 'bulk'
option storage 'hash'
option match 'ip'
option family 'ipv4'
option timeout '86400'