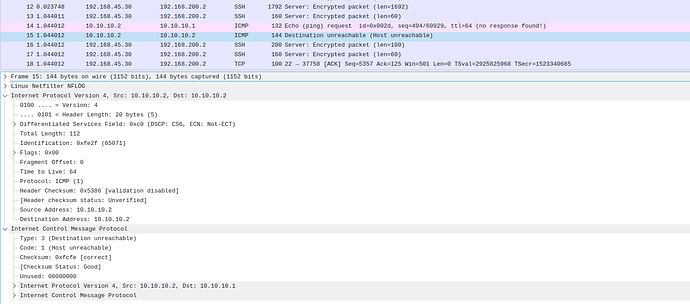
Hello everyone,
I am scratching my head for a few weeks on how to set up a Routed site-to-site VPN between pfSense and openwrt. 
The connection is establishing and according to my troubleshooting it seems that traffic traverses the tunnel but it is dropped on the openwrt side.
I will provide the configuration at the openwrt side of the tunnel 
 OpenWrt
OpenWrt
/etc/swanctl/swanctl.conf
connections {
bypass {
remote_addrs = 127.0.0.1
children {
bypasslan {
local_ts = 10.1.1.0/24
remote_ts = 10.1.1.0/24
mode = pass
start_action = trap
}
}
}
router01 {
fragmentation = yes
unique = replace
version = 2
proposals = aes256-sha256-modp2048
dpd_delay = 10s
dpd_timeout = 60s
rekey_time = 25920s
reauth_time = 0s
over_time = 2880s
rand_time = 2880s
encap = no
mobike = no
local_addrs = router01.viewdns.net
remote_addrs = 94.228.37.60
local {
id = fqdn:ipsec-home
auth = psk
}
remote {
id = fqdn:ipsec-tucana
auth = psk
}
children {
tucana {
close_action = start
dpd_action = restart
#mode = tunnel
policies = no
life_time = 3600s
rekey_time = 3240s
rand_time = 360s
start_action = trap
remote_ts = 192.168.201.1/30
local_ts = 192.168.201.2/30
#reqid = 100
mark_in = 32
mark_out = 42
esp_proposals = aes256gcm128-modp2048
}
}
}
}
secrets {
ike-0 {
secret = passwd
id-0 = %any
id-1 = fqdn:ipsec-tucana
}
}
/etc/strongswan.conf
# CUSTOM from pfSense
starter {
load_warning = no
}
charon {
# number of worker threads in charon
threads = 16
ikesa_table_size = 32
ikesa_table_segments = 4
init_limit_half_open = 1000
install_routes = no
install_virtual_ip = no # not in pfSense side. Added from internet tutorials.
load_modular = yes
ignore_acquire_ts = yes
cisco_unity = no
syslog {
identifier = charon
# log everything under daemon since it ends up in the same place regardless with our syslog.conf
daemon {
ike_name = yes
app = -1
asn = -1
cfg = -1
chd = -1
dmn = -1
enc = -1
esp = -1
ike = -1 # set to 2 to troubleshoot
imc = -1
imv = -1
job = -1
knl = -1 # set to 2 to troubleshoot
lib = -1
mgr = -1
net = 2
pts = -1
tls = -1
tnc = -1
}
# disable logging under auth so logs aren't duplicated
auth {
default = -1 # set to 2 for troubleshooting; -1 to supress
ike = -1
}
}
plugins {
#kernel-netlink{
# fwmark = !0x42
#}
include strongswan.d/charon/*.conf
}
}
include strongswan.d/*.conf
include /var/ipsec/strongswan.conf
/etc/config/network
...
config interface 'ipsec_vlan201'
option ifname 'ip_vti1'
option proto 'static'
option ipaddr '192.168.201.2'
option netmask '255.255.255.252'
...
/etc/config/firewall
...
config rule
option name 'Allow-IPSec-IKE-input'
option target 'ACCEPT'
list proto 'udp'
option src 'wan'
option dest_port '500 4500'
config rule
option name 'Allow-IPSec-ESP-input'
option target 'ACCEPT'
list proto 'esp'
option src 'wan'
config rule
option name 'Allow-IPSec-Auth-Header-input'
option target 'ACCEPT'
list proto 'ah'
option src 'wan'
...
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan'
option extra_src '-m policy --dir in --pol none'
option extra_dest '-m policy --dir out --pol none'
config zone
option name 'vlan5'
option network 'vlan5 eth0_VLAN5'
option output 'ACCEPT'
option input 'ACCEPT'
option family 'ipv4'
option forward 'ACCEPT'
option extra_src '-m policy --dir in --pol none'
option extra_dest '-m policy --dir out --pol none'
...
config zone
option family 'ipv4'
option output 'ACCEPT'
option input 'ACCEPT'
option forward 'ACCEPT'
option log '1'
option name 'vlan201'
option log_limit '2/minute'
option network 'ipsec_vlan201'
option extra_src '-m policy --dir in --pol ipsec --proto esp'
option extra_dest '-m policy --dir out --pol ipsec --proto esp'
list device 'ip_vti1'
I have added the extra iptables rules to non vpn zones as suggested on this post
I am able to connect with the configuration above as seen below 
root@R1 /etc/config > swanctl --load-all
root@R1 /etc/config > swanctl --initiate -c tucana

ipsec statusall
Status of IKE charon daemon (strongSwan 5.8.2, Linux 4.14.221, armv7l):
uptime: 2 hours, since Aug 08 22:05:13 2021
worker threads: 10 of 16 idle, 6/0/0/0 working, job queue: 0/0/0/0, scheduled: 5
loaded plugins: charon test-vectors ldap pkcs11 aes des blowfish rc2 sha2 sha1 md4 md5 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs8 pkcs12 pgp dnskey sshkey pem openssl gcrypt af-alg fips-prf gmp curve25519 agent xcbc cmac hmac ctr ccm gcm curl mysql sqlite attr kernel-netlink resolve socket-default connmark forecast farp stroke vici smp updown eap-identity eap-md5 eap-mschapv2 eap-radius eap-tls xauth-generic xauth-eap dhcp whitelist led duplicheck addrblock unity
Listening IP addresses:
192.168.201.2
192.168.30.1
192.168.40.1
192.168.50.1
192.168.10.1
192.168.20.1
192.168.5.1
192.168.6.1
192.168.60.1
194.75.11.234
Connections:
bypass: %any...127.0.0.1 IKEv1/2
bypass: local: uses any authentication
bypass: remote: uses any authentication
bypasslan: child: 10.1.1.0/24 === 10.1.1.0/24 PASS
router01: router01.viewdns.net...94.228.37.60 IKEv2, dpddelay=10s
router01: local: [ipsec-home] uses pre-shared key authentication
router01: remote: [ipsec-tucana] uses pre-shared key authentication
tucana: child: 192.168.201.0/30 === 192.168.201.0/30 TUNNEL, dpdaction=restart
Shunted Connections:
bypasslan: 10.1.1.0/24 === 10.1.1.0/24 PASS
Routed Connections:
tucana{1}: CREATED, TUNNEL, reqid 1
tucana{1}: 192.168.201.0/30 === 192.168.201.0/30
Security Associations (1 up, 0 connecting):
router01[3]: ESTABLISHED 51 minutes ago, 194.75.11.234[ipsec-home]...94.228.37.60[ipsec-tucana]
router01[3]: IKEv2 SPIs: 4a7b5f08f680f34e_i* ee6f0c589a57b258_r, rekeying in 5 hours
router01[3]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
tucana{5}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: cef99bfc_i c9d7dc00_o
tucana{5}: AES_GCM_16_256/MODP_2048, 9599 bytes_i, 0 bytes_o, rekeying in 47 minutes
tucana{5}: 192.168.201.0/30 === 192.168.201.0/30
The interface ip_vti1 was addes with the command below 
root@R1 /etc/config > ip tunnel add ip_vti1 local 194.75.11.234 remote 94.228.37.60 mode vti ikey 32 okey 42
root@R1 /etc/config > sysctl -w net.ipv4.conf.ip_vti1.disable_policy=1
root@R1 /etc/config > ip link set ip_vti1 up
root@R1 /etc/config > ip -c a
30: ip_vti1@NONE: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1472 qdisc noqueue state UNKNOWN group default qlen 1000
link/ipip 194.75.11.234 peer 94.228.37.60
inet 192.168.201.2/30 brd 192.168.201.3 scope global ip_vti1
valid_lft forever preferred_lft forever
inet6 fe80::200:5efe:c24b:bea/64 scope link
valid_lft forever preferred_lft forever
A route was added as 
root@R1 /etc/config > ip route
...
192.168.201.0/30 dev ip_vti1 proto kernel scope link src 192.168.201.2
I have captured ESP packets on my WAN 
root@R1 /etc/config > tcpdump -n -v -i pppoe-wan proto \\esp
tcpdump: listening on pppoe-wan, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
00:58:19.921492 IP (tos 0x0, ttl 54, id 46196, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5ea), length 64
00:58:20.463300 IP (tos 0x0, ttl 54, id 29878, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5eb), length 64
00:58:21.004909 IP (tos 0x0, ttl 54, id 465, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5ec), length 64
00:58:21.536088 IP (tos 0x0, ttl 54, id 8152, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5ed), length 64
00:58:22.077409 IP (tos 0x0, ttl 54, id 29796, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5ee), length 64
00:58:22.618782 IP (tos 0x0, ttl 54, id 29587, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5ef), length 64
00:58:23.137175 IP (tos 0x0, ttl 54, id 21944, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5f0), length 64
00:58:23.678087 IP (tos 0x0, ttl 54, id 31737, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5f1), length 64
00:58:24.186914 IP (tos 0x0, ttl 54, id 33641, offset 0, flags [none], proto ESP (50), length 84)
94.228.37.60 > 194.75.11.234: ESP(spi=0xcef99bfc,seq=0x5f2), length 64
Also a capture from a ping to the IP on the other side of the tunnel on the iface ip_vti1 
root@R1 /root > ping -I ip_vti1 192.168.201.1
PING 192.168.201.1 (192.168.201.1): 56 data bytes
no replies
...
root@R1 /etc/config > tcpdump -n -v -i ip_vti1
tcpdump: listening on ip_vti1, link-type RAW (Raw IP), capture size 262144 bytes
01:00:17.221710 IP (tos 0x0, ttl 64, id 2874, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 0, length 64
01:00:18.221836 IP (tos 0x0, ttl 64, id 2962, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 1, length 64
01:00:19.221920 IP (tos 0x0, ttl 64, id 3050, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 2, length 64
01:00:20.221997 IP (tos 0x0, ttl 64, id 3083, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 3, length 64
01:00:21.222136 IP (tos 0x0, ttl 64, id 3145, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 4, length 64
01:00:22.222282 IP (tos 0x0, ttl 64, id 3217, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 5, length 64
01:00:23.222431 IP (tos 0x0, ttl 64, id 3280, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.201.2 > 192.168.201.1: ICMP echo request, id 18761, seq 6, length 64
^C
7 packets captured
7 packets received by filter
0 packets dropped by kernel
17 packets dropped by interface
I have noticed a weird behaviour on the interface. The command ip -s tunnel show some statistics of the tunnel and ip_vti1 has errors on RX that looks like the gateway monitoring pings coming from the pfSense and on TX my pings that's errors out with NoRoute. 
root@R1 /etc/config > ip -s tunnel
ip_vti1: ip/ip remote 94.228.37.60 local 194.75.11.234 ttl inherit ikey 32 okey 42
RX: Packets Bytes Errors CsumErrs OutOfSeq Mcasts
0 0 14640 0 0 0
TX: Packets Bytes Errors DeadLoop NoRoute NoBufs
0 0 1550 0 1550 0
 I believe I have provided a good picture of my problem and I would appreciate if anyone with more experience could have a look into my setup and suggest about what to look next cause I can not see where the problem is.
I believe I have provided a good picture of my problem and I would appreciate if anyone with more experience could have a look into my setup and suggest about what to look next cause I can not see where the problem is.
Many thanks 
 ?
?
 ( A potential feature request for future releases ).
( A potential feature request for future releases ).
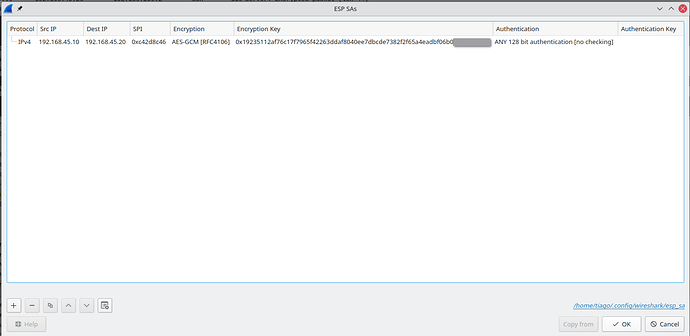
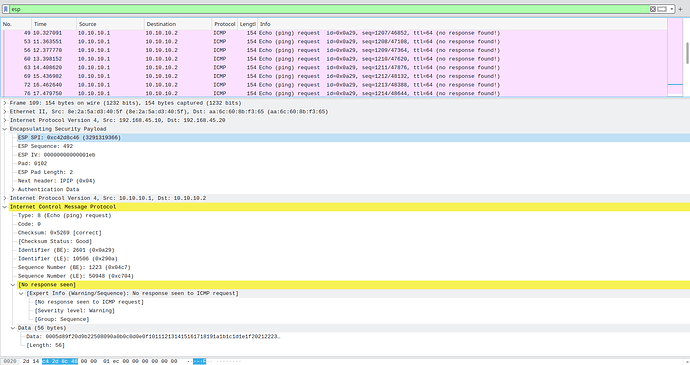
 The troubleshooting continues ...
The troubleshooting continues ...