I managed to set up an IKEv1 IPsec tunnel (Strongswan) on OWRT master (with firewall4), but despite the left and right subnets are configured correctly, the packets towards the rightsubnet are still forwarded towrads the WAN interface instead of the VPN tunnel itself.
I tried to use this comment], but the
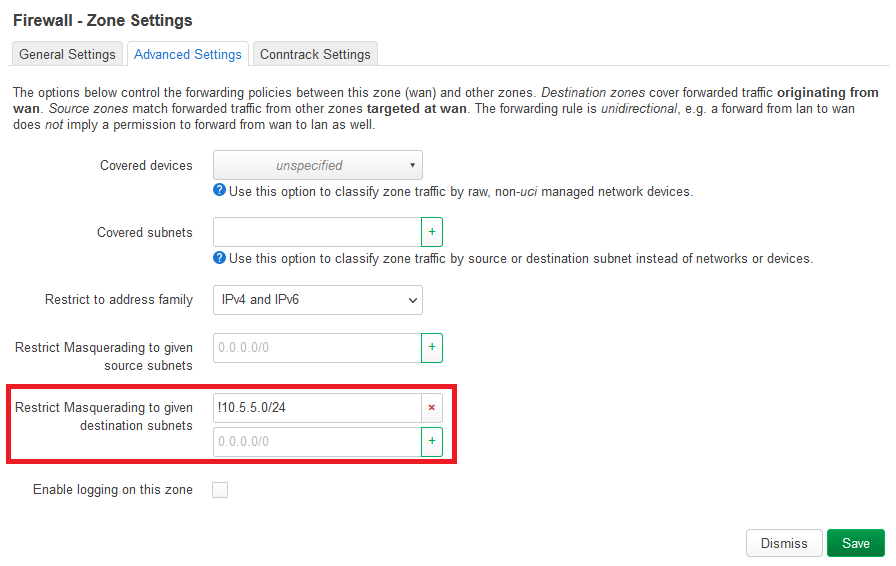
option extra_src '-m policy --dir in --pol ipsec --proto esp'
option extra_dest '-m policy --dir out --pol ipsec --proto esp'
options are not supported under firewall4.
I think the only thing I need is to set up routing/firewalling between the 192.168.2.0/24 (left subnet) and 10.5.5.0/24 (right subnet) and then it should be fine.
I have read all the suggested topics, no luck there. Interesting thing is, that when I use the exact same ipsec.conf on a VM behind the router (bridged to the LAN subnet), then the routing works, I can reach the remote end through the tunnel.
The tunnel itself is up as much as I can tell (server end also tells tunnel is up):
Connections:
VPN_NOC-VPN_NOC_c: %any...144.178.x.x IKEv1 Aggressive, dpddelay=10s
VPN_NOC-VPN_NOC_c: local: [xxxx.yyyyyy.zzzz] uses pre-shared key authentication
VPN_NOC-VPN_NOC_c: remote: [144.178.x.x] uses pre-shared key authentication
VPN_NOC-VPN_NOC_c: child: 192.168.2.0/24 === 10.5.5.0/24 TUNNEL, dpdaction=start
Security Associations (1 up, 0 connecting):
VPN_NOC-VPN_NOC_c[1]: ESTABLISHED 35 minutes ago, 84.236.x.x[xxxx.yyyyyy.zzzz]...144.178.x.x[144.178.x.x]
VPN_NOC-VPN_NOC_c[1]: IKEv1 SPIs: cc404d97959217f9_i* b89431274e1684cb_r, pre-shared key reauthentication in 2 hours
VPN_NOC-VPN_NOC_c[1]: IKE proposal: AES_CBC_192/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_3072
VPN_NOC-VPN_NOC_c{1}: REKEYED, TUNNEL, reqid 1, expires in 24 minutes
VPN_NOC-VPN_NOC_c{1}: 192.168.2.0/24 === 10.5.5.0/24
VPN_NOC-VPN_NOC_c{2}: INSTALLED, TUNNEL, reqid 1, ESP SPIs: c2e80c79_i f7792e8d_o
VPN_NOC-VPN_NOC_c{2}: AES_CBC_192/HMAC_SHA2_256_128/MODP_3072, 0 bytes_i, 0 bytes_o, rekeying in 8 minutes
VPN_NOC-VPN_NOC_c{2}: 192.168.2.0/24 === 10.5.5.0/24
Any and all help is appreciated.
MOD: I looked at VPN Policy-Based Routing, but as much as it seems, this is not usable for IPsec as there is no "VPN" interface available...